In a world of constant digital noise, figuring out how can you protect your home computer is more important than ever. As a tech expert with over a decade of experience at Afdevinfo, I know how overwhelming cybersecurity can feel. Generic advice often misses the mark because your digital life is unique. That’s why I’ve created this practical, personalized guide to move you from feeling vulnerable to feeling empowered. I’m not just going to list rules; I’m going to show you how to build a security plan that fits your life.
Here is a quick look at what I’ll help you accomplish today:
- Assess your current security level with a quick, no-judgment checklist.
- Master the 6 essential pillars of digital protection, from passwords to backups.
- Choose the right tools with a simple, visual guide to security software.
- Create a personalized security plan tailored to your specific needs, whether you’re a remote worker, a parent, or a smart home user.
1. Quick-start checkup: How safe is your computer right now?
Before we dive in, let’s get a baseline of your current security. This isn’t a test with a failing grade; it’s a simple personal cybersecurity checklist to help you identify which areas need the most attention. Be honest with your answers!
Answer 'Yes' or 'No' to the following questions:
- Is your operating system (Windows or macOS) set to update automatically?
- Do you use a unique, complex password for every single online account?
- Is Multi-Factor Authentication (MFA) enabled on your primary email and banking accounts?
- Do you have a reputable antivirus program installed, and is it running real-time scans?
- Is your computer’s built-in firewall turned on?
- Have you changed the default administrative password on your home Wi-Fi router?
- Do you perform regular backups of your important files to an external drive or cloud service?
If you answered ‘no’ to more than a few questions, don’t worry. That’s precisely why you’re here. This guide will walk you through fixing each point, step-by-step, turning every ‘no’ into a confident ‘yes’.
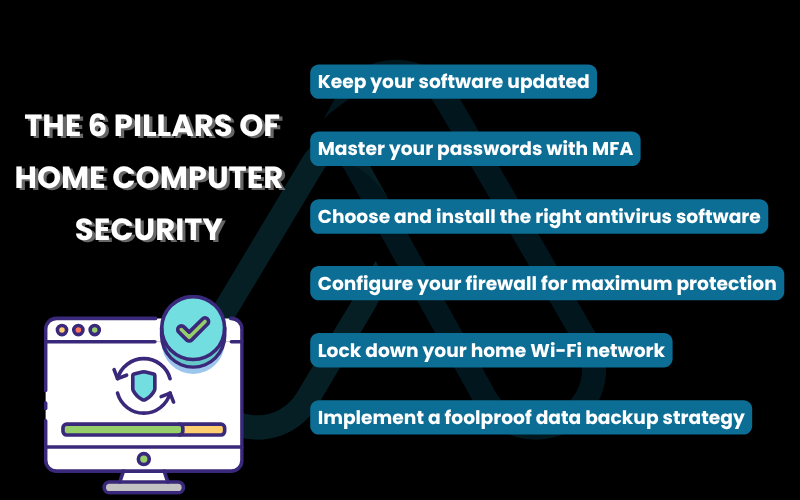
2. How can you protect your home computer: The 6 pillars of home computer security
Think of your computer’s security like building a house. You can’t just put up a fancy door; you need strong walls, a solid roof, and locked windows. These six pillars are the essential foundation that every user, regardless of skill level, must implement to stay safe.
2.1. Keep your software updated
When asked about how often to update computer security settings, the common advice is: update as soon as possible. Ignoring software updates can be likened to leaving a broken window unfixed, as security vulnerabilities can be exploited by hackers. Updates often contain critical patches that protect the system from known vulnerabilities.
Both Windows and macOS offer automatic update features, which help users receive important security patches without needing to check manually. However, it is also important to note that some updates can cause issues or conflicts with existing applications, particularly with newer operating systems like Windows 11. Microsoft has issued warnings regarding potential problems that may arise after certain updates.
Therefore, deciding whether to update immediately should involve weighing the importance of maintaining security against the stability of the system. Users may choose to delay updates to monitor community feedback before applying a new version.
In summary, enabling automatic updates is a crucial measure for protecting computers, but users should also take careful steps to ensure that updates do not adversely affect performance or system stability.
2.2. Master your passwords with multi-factor authentication (MFA)
Passwords alone are no longer enough. Even a complex one can be cracked or stolen. This is where multi-factor authentication for computers, or MFA, comes in. Think of it like needing two keys to open a door instead of just one – it requires your password plus a second form of verification, usually a code sent to your phone. To enable it on a service like Google, you can follow these steps:
- Log in to your Google Account.
- Navigate to the ‘Security’ section.
- Find the ‘2-Step Verification’ option and click to begin setup.
- Follow the on-screen prompts to link your phone number or an authenticator app.
This single step dramatically increases your account security, making it incredibly difficult for anyone else to gain access, even if they have your password.
2.3. Choose and install the right antivirus software
A common question I hear is, ‘Do I need antivirus software for my home PC?’ The answer is an unequivocal yes. While built-in tools like Windows Defender have become quite good, they represent a baseline. Dedicated third-party antivirus software for home use offers a more comprehensive suite of malware protection against viruses, ransomware, spyware, and more. Free versions can be effective, but paid solutions often provide a crucial advantage. Here are some key features to look for:
- Real-time protection: Actively scans files and downloads as they happen.
- Ransomware protection: Prevents malicious software from encrypting your files.
- Web protection: Blocks you from visiting known malicious websites.
- Regular updates: Constantly updates its virus definitions to catch new threats.
2.4. Configure your firewall for maximum protection
Your computer’s firewall acts as a digital gatekeeper, or a bouncer at a club. It monitors incoming and outgoing network traffic, deciding what to allow and what to block based on a set of security rules. It’s your first line of defense against network-based attacks. Both Windows and macOS have powerful firewalls built-in, but you need to ensure they’re active.
On Windows, you can search for ‘Windows Defender Firewall’ in the Start Menu.
On macOS, go to ‘System Settings’ > ‘Network’ > ‘Firewall’. My top firewall protection tips are to ensure it’s turned on for both private and public networks and to block all incoming connections for apps you don’t recognize.
2.5. Lock down your home Wi-Fi network
An insecure Wi-Fi network is an open door for hackers to access every single device connected to it. If you’ve ever wondered, ‘How can I protect my Wi-Fi network from hackers?’, the answer lies in securing your router. Here is my essential checklist to secure your home Wi-Fi network:
- Change the administrator login: Your router came with a default username and password (like ‘admin’/’password’). Change it immediately to something unique.
- Use strong encryption: In your router settings, ensure you are using WPA3 encryption. If WPA3 isn’t available, WPA2 is the next best option. Avoid the outdated WEP standard at all costs.
- Set a strong Wi-Fi password: This is the password you use to connect your devices. Make it long and complex, combining letters, numbers, and symbols.
- Change the network name (SSID): Don’t use your family name or address as your Wi-Fi name, as it can give away personal information.
2.6. Implement a foolproof data backup strategy
Backups are your ultimate safety net. If your computer is infected with ransomware, your hard drive fails, or you accidentally delete a critical file, a recent backup can save you. I always recommend the 3-2-1 rule, one of the most reliable home computer backup strategies.
It’s simple: have at least 3 total copies of your data, store the copies on 2 different media types (e.g., your computer and an external drive), and keep 1 copy off-site (e.g., in the cloud or at a different physical location). This redundancy ensures that no single event, like a fire or theft, can wipe out all your data.
3. Your digital toolkit: A visual guide to security software
Choosing the right software can be overwhelming. To help you decide, I’ve broken down some of the best options across key categories like antivirus solutions, password managers, and VPNs. This simple table gives you a clear, at-a-glance comparison to find the tool that fits your needs.
Here is a visual breakdown of the top security tools for 2025:
| Tool Name | Best For… | Key Feature | Price (approx.) |
|---|---|---|---|
| SecureGuard Antivirus | All-around protection | Real-time threat detection & ransomware rollback | $40/year |
| PassFortress Manager | Password security | One-click strong password generation & auto-fill | $30/year |
| CloakVPN | Privacy & remote work | Military-grade encryption & no-logs policy | $10/month |
| Defender Plus Suite | Windows users | Enhanced firewall & parental controls | $50/year |
| VaultPass Free | Beginners | Secure password storage for up to 50 entries | Free |
4. Defending against emerging threats: What to watch for in 2025
Staying secure means looking ahead. The threats of yesterday are not the threats of tomorrow. As your technology expert, I want to equip you with the advanced knowledge to recognize and defend against the next wave of cyberattacks before they become mainstream.
4.1. The new face of phishing: AI-powered scams and social engineering
The days of phishing emails riddled with typos are over. AI is now being used to craft perfectly worded, highly convincing emails, texts, and social media messages. These attacks prey on human psychology through sophisticated social engineering. My number one rule is: ‘When in doubt, don’t click. Verify independently.’ If you get an urgent email from your bank, don’t click the link; open a new browser tab and go to their website directly.
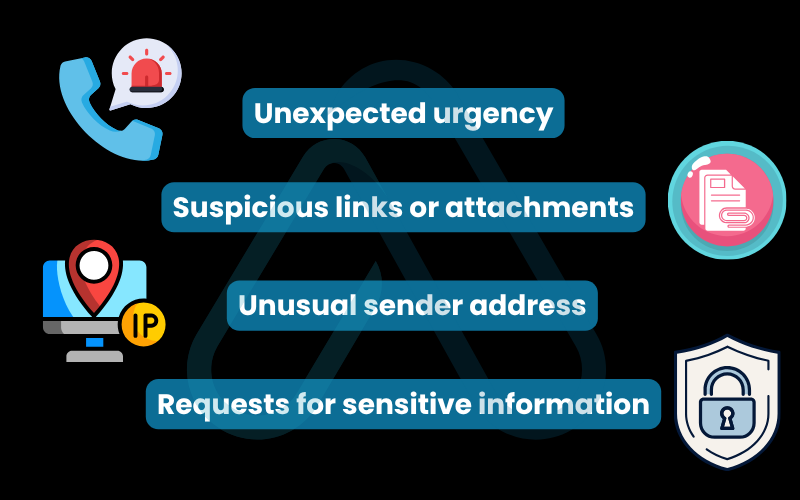
To help you prevent phishing attacks, here is my red flag checklist:
- Unexpected urgency: Is the message pressuring you to act immediately?
- Suspicious links or attachments: Does the email contain attachments you weren’t expecting?
- Unusual sender address: Does the sender’s email address look slightly off?
- Requests for sensitive information: Is it asking for passwords, credit card numbers, or other personal data?
4.2. Ransomware 101: Preventing a digital hostage situation
Ransomware is malicious software that acts like a digital kidnapper. It encrypts all your personal files – photos, documents, everything – and holds them hostage until you pay a ransom, usually in cryptocurrency.
These attacks often happen through phishing emails or by exploiting unpatched software vulnerabilities. The most recent ransomware trends show an increase in attacks on home users. This is where your backup strategy becomes your hero. If you have a clean backup, you can simply restore your files without ever considering the ransom.
Recommendation is clear: Never pay the ransom.
The FBI and CISA’s official
There is no guarantee you will get your data back, and it may fund criminal activity.
5. Personalized protection: Security plans for your unique needs
Cybersecurity isn’t one-size-fits-all. Your digital life is unique, and your protection should be too. How you can protect your home computer depends entirely on how you use it. Below, I’ve created mini-guides for different user profiles to help you build a plan that truly fits.
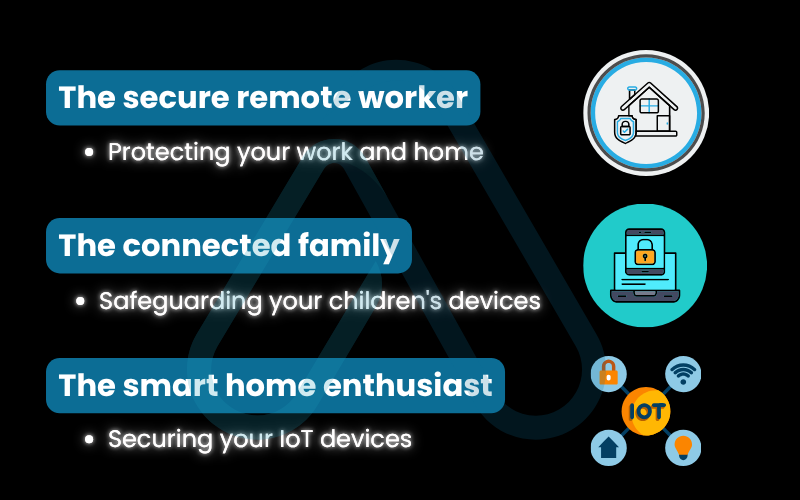
5.1. The secure remote worker: Protecting your work and home
When your home computer is also your work computer, the stakes are higher. You’re responsible for protecting your data and your employer’s sensitive information. The biggest risk is a blended environment where work and personal activities mix on an insecure network. My top work-from-home security advice is to create separation. Here is your to-do list:
- Use a VPN: A Virtual Private Network (VPN) for remote work encrypts your internet connection, protecting sensitive company data from being intercepted on your home Wi-Fi.
- Segment your network: If your router supports it, create a separate ‘Guest’ Wi-Fi network for personal devices and smart home gadgets, keeping your work computer isolated on the main network.
- Lock your computer: When you step away from your computer, always lock the screen (Windows Key + L on Windows, Control-Command-Q on Mac).
- Follow company policy: Adhere strictly to your employer’s security guidelines regarding software, data handling, and passwords.
5.2. The connected family: Safeguarding your children’s devices
Protecting a family’s digital life is about creating a safe environment for children to explore, learn, and connect. It’s a balance of technical controls and open communication. I recommend using parental control software to filter inappropriate content and manage screen time. However, technology alone isn’t enough. True child online safety comes from teaching digital literacy.
Here are a few conversation starters I’ve found useful:
- ‘Let’s talk about what makes a strong password and why we don’t share it, just like our house key.’
- ‘If someone online ever makes you feel uncomfortable, sad, or scared, you can always come to me, and you won’t be in trouble.’
- ‘What kind of personal information is safe to share online, and what should we always keep private?’
5.3. The smart home enthusiast: Securing your IoT devices
Your smart speakers, security cameras, thermostats, and even coffee makers are all part of the Internet of Things (IoT). While convenient, they can also pose a security risk. Every new smart device is another potential door into your network. Many IoT devices have weak default security settings, making them easy targets.
To achieve solid smart home protection, I advise this simple checklist for every new gadget you install:
- Change the default password immediately. This is the single most important step for IoT security.
- Disable features you don’t use, especially remote access if it’s not needed.
- Check for firmware updates regularly, as these often contain security patches.
- Place IoT devices on a separate guest network if possible, to isolate them from your primary computers.
6. Cyber first-aid: Your troubleshooting guide for security incidents
Even with the best protection, things can happen. Here’s what to do if you suspect a problem. Don’t panic – act. Following a clear plan can minimize damage and get you back on track quickly.
6.1. Scenario 1: You think your computer is infected
Is your computer suddenly acting strangely? Sluggish performance, constant pop-ups, or programs crashing are all common computer virus symptoms. If you suspect an infection, here is what to do immediately. I call this my 5-Step Emergency Scan Protocol:
- Disconnect from the Internet: Unplug the network cable or turn off your Wi-Fi. This prevents the malware from spreading or sending your data out.
- Boot into Safe Mode: Restart your computer in Safe Mode (with Networking, if you need to download tools). This loads only essential services, which can prevent some malware from running.
- Run a full antivirus scan: Open your antivirus software and initiate a full, deep system scan. This may take a while.
- Delete or quarantine threats: Follow your antivirus program’s instructions to remove any threats it finds.
- Change critical passwords: From a separate, clean device, immediately change the passwords for your email, banking, and social media accounts.
If these steps don’t resolve the issue, it may be time for professional malware removal help.

6.2. Scenario 2: You clicked on a phishing link or opened a bad attachment
It happens to the best of us. Realizing you’ve clicked on something malicious is a sinking feeling, but speed is your friend. The first few minutes are the most critical. Here is a simple breakdown of what to do versus what not to do:
| Do | Don’t |
|---|---|
| Immediately disconnect from the internet. | Don’t enter any usernames or passwords on the suspicious site. |
| Run a full antivirus scan. | Don’t assume everything is fine if you don’t see immediate problems. |
| Change the password for the compromised account from a safe device. | Don’t be embarrassed to report it. Inform your IT department if it’s a work device. |
| Monitor your financial and online accounts for suspicious activity. | Don’t delay. The faster you act, the less damage can be done. |
After taking these steps, it’s also helpful to report the phishing attempt to services like Google or Microsoft to help protect others. This reinforces our collective ability to prevent phishing attacks.
7. FAQs about how can you protect your home computer
As an expert in this field, I receive a lot of questions. Here are my quick and direct answers to some of the most common ones I hear.
What is the single best way to secure a home computer?
Keep software updated, use strong unique passwords with MFA, and install a reputable antivirus.
Is free antivirus software good enough?
Yes, for basic protection. Windows Defender works well, but paid options add extra security features.
How can I tell if my home Wi-Fi is secure?
Use WPA3 or WPA2 encryption, a strong Wi-Fi password, and change the router’s default admin login.
What are the most common threats to home computers today?
Phishing, malware, and ransomware are the main threats targeting users and system weaknesses.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| MFA | Multi-Factor Authentication | A security method requiring two or more verification factors to gain access. |
| WPA3 | Wi-Fi Protected Access 3 | The latest and most secure encryption protocol for Wi-Fi networks. |
| SSID | Service Set Identifier | The public name of a Wi-Fi network. |
| IoT | Internet of Things | A network of physical devices (like smart speakers and cameras) embedded with sensors and software. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your IP address. |
| Ransomware | Ransomware | A type of malicious software that blocks access to a victim’s data until a ransom is paid. |
| Phishing | Phishing | A fraudulent attempt to obtain sensitive information by disguising as a trustworthy entity. |
| Malware | Malicious Software | Software intentionally designed to cause damage to a computer, server, or network. |
| CISA | Cybersecurity and Infrastructure Security Agency | A U.S. federal agency responsible for cybersecurity and infrastructure protection. |
| FBI | Federal Bureau of Investigation | The domestic intelligence and security service of the United States. |
8. Final thoughts
Securing your digital life can feel like a monumental task, but I hope this guide has shown you that it’s a series of small, manageable steps. The core message I want you to take away is that proactive, personalized security is achievable for everyone. You now have the knowledge and the tools to understand how you can protect your home computer effectively. Your first step is the most important one.
Here are the most critical takeaways from our guide:
- Layer your defenses: Rely on a combination of updates, strong passwords with MFA, antivirus software, and backups.
- Stay vigilant: Be skeptical of unsolicited messages and learn to recognize the red flags of modern phishing and scams.
- Personalize your plan: Your security needs are unique. Apply the specific advice that fits your lifestyle, whether you work from home or manage a connected family.
Your digital security is a journey, not a destination. Start yours today by implementing just one tip from this guide. The peace of mind you’ll gain is well worth the effort. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.









