That nagging feeling that someone is watching your screen is more than just paranoia – it’s a valid digital-age concern, and I’m here to help you get to the bottom of it. As a security expert, I’ve seen it all, and in this guide, I’ll walk you through exactly how to tell if someone is monitoring your computer, whether it’s a work machine or your personal device at home. This is the most comprehensive resource you’ll find, moving from simple observation to advanced diagnostics. We won’t just find the problem; we’ll create a plan to fix it.
Here’s the roadmap I’ve laid out for you:
- Observable Signs: We’ll start with the behavioral and performance red flags you can spot without any special tools.
- Software Checks: I’ll guide you through using your computer’s built-in utilities to hunt for suspicious software.
- Network Analysis: For those who want to be certain, we’ll look at advanced methods for tracking hidden connections.
- Action Steps: If you find something, I’ll provide a clear, step-by-step plan for what to do next.
1. 10+ tell-tale signs: Behavioral and performance red flags
Before we dive into any technical tools, your first line of defense is your own intuition backed by observation. Monitoring software, no matter how stealthy, leaves footprints. While these signs aren’t definitive proof on their own, a combination of them is a strong indicator that warrants a deeper investigation.
1.1. Performance degradation you can’t ignore
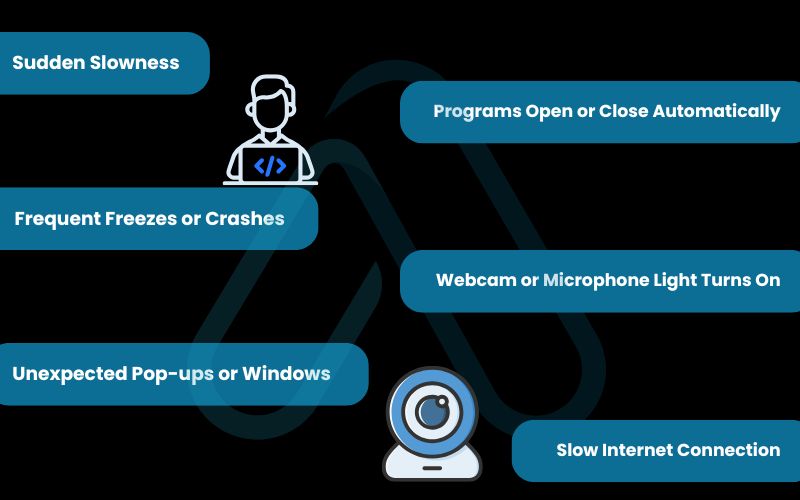
Monitoring software is like an uninvited app that’s always running in the background, consuming resources and draining your computer’s energy. If you’ve noticed these symptoms, it’s time to pay attention. Here’s a quick checklist of performance issues to look for:
- Sudden Slowness: Is your computer taking much longer to boot up, open applications, or perform routine tasks, even when you aren’t doing anything intensive?
- Overheating and Fan Noise: Does your laptop get unusually hot or do its fans spin at full speed for no apparent reason? This is a classic sign of hidden background processes consuming high CPU cycles.
- Drastically Reduced Battery Life: If your laptop battery suddenly can’t hold a charge for nearly as long as it used to, it could be because spyware is constantly running and draining power.
- Frequent Freezes or Crashes: Monitoring tools can be poorly written or conflict with other software, leading to system instability, blue screens, or unexpected reboots.
1.2. Unexpected computer behavior
These signs are more direct and can indicate that someone has unauthorized remote access to your machine. It’s crucial not to dismiss these as simple glitches, as they can be signs of active remote desktop surveillance. Here are some of the most alarming behaviors:
- Your Mouse Moves on Its Own: If you see your cursor moving, clicking, or highlighting things without your input, it’s a major red flag for remote access.
- Unexpected Pop-ups or Windows: Are command prompt windows or other applications flashing open and then closing quickly? This could be scripts running in the background.
- Settings Change Mysteriously: Have you found your homepage, security settings, or screen saver changed without your permission?
- Programs Open or Close Automatically: Applications you didn’t launch are suddenly running, or programs you are using abruptly close.
| Expert Tip: Many users dismiss these behaviors as a ‘glitch’ or a ‘bug’. In my experience, while glitches happen, consistent and repeated unexpected behavior is almost always a sign of a deeper problem, including unauthorized remote access. |
1.3. Suspicious network and data activity
Monitoring tools must send the data they collect back to the person watching. This transmission process can create observable network symptoms. I’ll show you how to do a more detailed network traffic analysis later, but here are the initial signs:
- Webcam or Microphone Light Turns On: If the indicator light for your webcam or microphone activates when you’re not using it, someone could be watching or listening.
- Spikes in Data Usage: A sudden, unexplained increase in your internet data usage could be caused by spyware constantly uploading screen recordings, keystrokes, and files. Many internet service providers offer tools to track your data usage; I recommend checking these logs if you’re suspicious.
- Slow Internet Connection: If your internet is sluggish only on one specific computer but fine on other devices, it might be due to monitoring software hogging your bandwidth.
2. Your first look: Basic diagnostic checks anyone can perform
Now that you know the outward signs, it’s time to look under the hood. You don’t need to be a tech wizard for this part. I’ll guide you through using the tools already built into Windows and macOS to spot suspicious processes and applications. These are your primary tools for spyware removal and keylogger detection.
2.1. Investigating active processes with Task Manager (Windows)
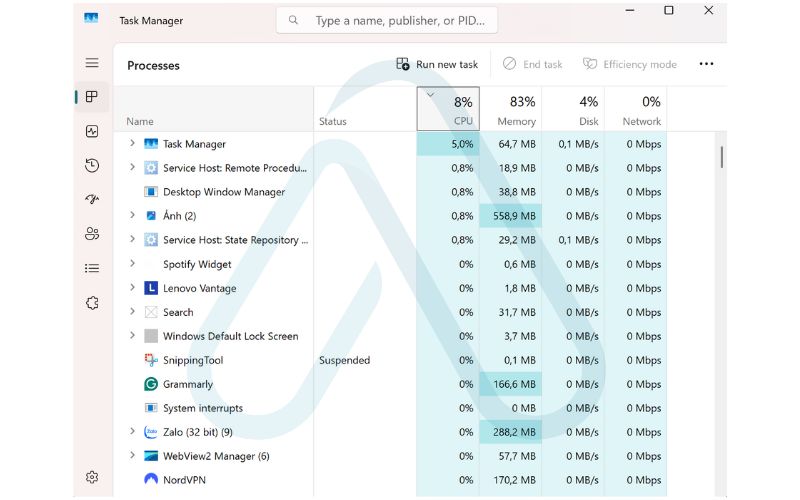
On Windows, the Task Manager is your command center for seeing everything that’s currently running. Here’s a simple process I use to hunt for anomalies:
- Open Task Manager: Press Ctrl + Shift + Esc on your keyboard.
- Look for High Resource Usage: In the ‘Processes’ tab, click on the ‘CPU’ and ‘Memory’ column headers to sort the list. Look for any non-system processes that are consistently using a high percentage of your resources.
- Identify Unknown Processes: Scan the list for names you don’t recognize. Be aware that many system processes have cryptic names, but spyware can also disguise itself.
- Research Suspicious Names: If you find a process you’re unsure about, right-click it and select ‘Search online’. This will perform a web search for the process name, which can quickly reveal if it’s legitimate or associated with monitoring software like Teramind, ActivTrak, or Hubstaff.
2.2. Using Activity Monitor to find spies on a Mac
For my Mac users, your equivalent tool is the Activity Monitor. It’s just as powerful as its Windows counterpart and is essential for finding out if you are being monitored.
- Open Activity Monitor: Go to ‘Applications’ > ‘Utilities’ and open ‘Activity Monitor’, or search for it using Spotlight (Cmd + Space).
- Check the CPU and Network Tabs: Similar to Task Manager, I recommend sorting by ‘% CPU’ to see what’s consuming the most power. Pay close attention to the ‘Network’ tab to see which processes are sending and receiving data.
- Spot Suspicious Processes: Look for processes with strange names or those that lack a clear origin or an icon. Just like on Windows, you can search online for any process name you don’t recognize to verify its purpose. A process that is sending a large amount of data but isn’t a browser or cloud sync app is highly suspicious.
2.3. Checking your installed programs and browser extensions
Sometimes, monitoring software isn’t hidden as a background process but is installed as a full application or a malicious browser extension. Here’s how to check:
- On Windows: Go to ‘Settings’ > ‘Apps’ > ‘Apps & features’. Carefully review the list of installed programs for anything you don’t remember installing.
- On macOS: Open the ‘Finder’ and go to the ‘Applications’ folder. Look through the list for any unfamiliar apps.
- Browser Extensions: In your web browser (Chrome, Firefox, Edge, etc.), go to the extensions or add-ons menu. Disable or remove any extension that you did not intentionally install yourself.
| Important warning: Be very careful not to delete or uninstall anything you are unsure about. Some items on these lists are critical system files or drivers. Always use the ‘Search online’ trick to verify a program’s identity before taking action. |
3. Going deeper: Advanced tools for detecting stealth monitoring
If the basic checks didn’t reveal anything but your gut tells you something is still wrong, it’s time to bring out the more powerful tools. These methods are for the moderately tech-savvy user who wants a higher degree of certainty. This is where we perform some real privacy-first diagnostics to uncover even the most well-hidden spies.
3.1. Using ‘netstat’ to uncover hidden connections
The `netstat` (network statistics) command is a powerful tool built into both Windows and macOS that shows you all active network connections to and from your computer. It’s my go-to for performing network traffic analysis without installing extra software. Here is how I use it to find unauthorized remote access:
- Open Command Prompt (Windows) or Terminal (macOS): On Windows, search for ‘cmd’, right-click it, and ‘Run as administrator’. On Mac, open the Terminal app.
- Run the Command: Type the following command and press Enter:
netstat -ano - Analyze the Output: You’ll see a list of connections. Look at the ‘Foreign Address’ column. This shows where your computer is connecting to. If you see connections to IP addresses you don’t recognize (that aren’t related to websites you’re visiting), take note of the corresponding ‘PID’ (Process ID) in the far-right column.
- Cross-Reference the PID: Open Task Manager (Windows) or Activity Monitor (macOS), go to the ‘Details’ or ‘PID’ tab, and find the process with the matching ID. This will tell you exactly which application is making that suspicious connection.
3.2. Checking for kernel-level spies and rootkits
The most advanced monitoring tools are rootkits, which hide themselves deep within the operating system (at the kernel level), making them invisible to standard tools like Task Manager. Detecting these emerging stealth monitoring technologies requires specialized scanners. Here are a few reputable tools I trust:
Before you scan, remember that for the best results, you should run these tools from Safe Mode or, even better, a bootable USB drive, as this prevents the rootkit from actively hiding itself during the scan. Here is a comparison of some effective tools:
| Tool Name | Platform | Key Feature |
| Malwarebytes Anti-Rootkit | Windows | Specifically designed to find and remove the trickiest deep-level rootkits. |
| GMER | Windows | A powerful, advanced scanner that can detect hidden processes, modules, and services. |
| Bitdefender Rootkit Remover | Windows/macOS | A free, easy-to-use tool from a trusted cybersecurity company. |

3.3. Can antivirus detect monitoring software?
This is a question I get all the time. The answer is: yes, but it’s complicated. A good antivirus (AV) program is excellent at detecting known malware, viruses, and many types of commercial spyware. A full system scan is always a recommended step. However, many forms of employee monitoring software are considered ‘legitimate’ applications.
Because they can have valid uses (like corporate IT security), they are often whitelisted by antivirus companies and won’t be flagged as malicious. So, while you absolutely should run a full AV scan, don’t rely on it as your only method for detecting corporate surveillance tools.
4. Context is key: At work vs. at home
Understanding how to tell if someone is monitoring your computer heavily depends on the context. The rules, expectations, and potential responses are vastly different for a company-owned device versus your personal computer at home. Acknowledging these differences is critical to avoiding unnecessary panic and taking the right action.
4.1. On a work computer: What to expect and what’s not okay
Let’s be clear: if you are using a computer owned by your employer, you should assume some level of monitoring is taking place. Most companies have policies in place to protect their assets, ensure productivity, and maintain security. These policies are usually outlined in an Acceptable Use Policy (AUP) or employee handbook.
Before you panic, I strongly advise you to find and read this document. The employee monitoring software might be fully disclosed. The signs your PC is being monitored at work could be part of a standard, legal procedure. What’s not okay is monitoring that goes beyond the stated policy or ventures into capturing personal credentials or webcam footage without cause or consent.
4.2. Distinguishing IT maintenance from invasive surveillance
One of the biggest sources of anxiety is confusing legitimate IT functions with malicious spying. Your IT department uses tools for remote support, security patching, and asset management that can look like monitoring. Here’s a table to help you tell the difference:
| Legitimate IT Functions | Potentially Invasive Monitoring |
| Remote access for a scheduled support ticket you initiated (e.g., using TeamViewer). | Unexplained remote access when you have not requested help. |
| Software that pushes security updates or installs company-approved applications. | Keyloggers that capture everything you type, including personal passwords. |
| Endpoint protection software (antivirus) that scans for threats. | Software that takes screenshots or records your screen constantly without a stated purpose. |
| Asset management tools that track the computer’s serial number and installed software. | Webcam or microphone activation outside of official video conferencing calls. |
4.3. On your personal computer: Protecting your privacy at home
On your personal computer, the situation is much more serious. Any unauthorized monitoring is a severe privacy violation and potentially illegal. The vectors for this are different; it’s often not corporate software but spyware installed through suspicious downloads, phishing emails, or by someone with physical access to your device. If you suspect monitoring on a personal machine, your goal should be aggressive spyware removal and re-securing the device against future access.
If you suspect that a partner or family member has installed monitoring software on your device without your consent, this may be a form of tech-enabled domestic abuse. Please consider seeking help from resources specializing in digital safety and domestic violence.
A Note on Personal Safety
5. What if you find something? A step-by-step action plan
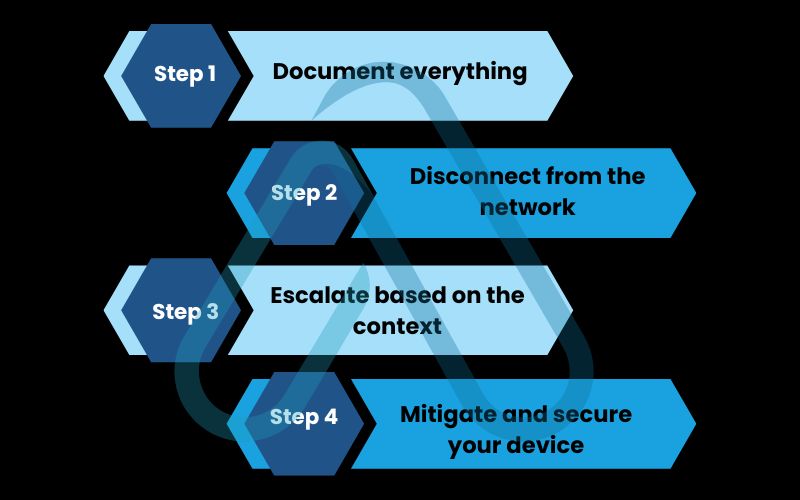
Discovering that you’re being monitored can be frightening. It’s crucial to stay calm and follow a logical plan to contain the situation and resolve it safely. I’ve created this decision flowchart to guide you from discovery to resolution.
5.1. Step 1: Document everything
Before you do anything else, gather evidence. This information is critical whether you’re reporting the issue to IT, HR, or law enforcement. Here’s what you should document:
- Take Screenshots: Capture images of the suspicious process in Task Manager, the unfamiliar program in your installed apps list, or the strange network connection from `netstat`.
- Write Down Details: Note the date, time, the name of the suspicious file or process, and a description of the strange behavior you’ve observed.
- Use Your Phone: If your mouse is moving on its own, use your phone to record a video of the screen.
5.2. Step 2: Disconnect from the network
Your first move is to cut the connection. Disconnecting your computer from the internet (unplug the Ethernet cable and turn off Wi-Fi) immediately stops the monitoring software from sending any more of your data out. This is a critical containment measure that puts you back in control.
5.3. Step 3: Escalate based on the context
Your next steps depend entirely on where this is happening. The wrong move here can make the situation worse, so choose your path carefully. Here’s my advice:
| Scenario | Recommended Action |
| If it’s a work computer… | Report your findings to your direct manager, your company’s IT security department, or HR, depending on who you trust and who the suspected actor is. Present your documented evidence calmly and professionally. |
| If it’s a personal computer… | Consider contacting a professional IT security consultant for help with spyware removal. If you believe a crime has been committed (e.g., stalking, theft of information), contact local law enforcement with your evidence. |
5.4. Step 4: Mitigate and secure your device
After the issue has been reported and addressed, you must secure your device to prevent it from happening again. Here are the essential steps for remediation:
- Change Your Passwords: Immediately change all your important passwords (email, banking, social media) from a different, trusted device.
- Run Spyware Removal Tools: Use reputable anti-malware and anti-spyware tools to clean the system.
- Consider a Full Reinstall: For maximum peace of mind, the only 100% guaranteed way to remove deep-level monitoring software is to back up your essential files (and only your files, not programs) and perform a complete reinstall of your operating system.
6. Understanding your rights: Legal and ethical considerations
Navigating the legality of computer monitoring can be complex, as laws vary significantly by region and context. This section provides a general overview, but it is not a substitute for professional legal advice.
| Disclaimer: The following is for informational purposes only and does not constitute legal advice. Please consult with a legal professional for guidance on your specific situation. |
Generally, in a workplace context, employers in many regions have the right to monitor company-owned equipment, especially if this policy is disclosed to employees in writing (like in an AUP). However, this right is not unlimited and typically does not extend to monitoring that infringes on protected employee rights or captures highly sensitive personal information without a clear business justification.
When it comes to answering, ‘Is it legal for someone to monitor my computer without my consent?’, the answer for a personal computer is almost always no. Unauthorized access to a personal computer is illegal under various computer fraud and abuse acts in most jurisdictions. Consent is the key factor, and on a device you own, you have the highest expectation of privacy.
7. FAQs about how to tell if someone is monitoring your computer
I’ve compiled answers to some of the most common questions I receive on this topic to give you quick and clear information.
How do I check for hidden monitoring software on my phone?
Check for high battery/data usage, unknown apps, suspicious permissions, and run a trusted security scanner.
Can someone monitor my computer if it’s turned off?
No. If it’s fully powered off, it cannot be monitored in real-time.
Does a factory reset remove all monitoring software?
Yes in almost all cases. A full reset wipes software, and only extremely rare firmware-level implants could survive it.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
| PUP | Potentially Unwanted Program | Software that may be unwanted, despite the user consenting to download it, often bundled with other software. |
| PID | Process Identifier | A unique number that the operating system’s kernel assigns to an active process. |
| netstat | Network Statistics | A command-line tool that displays active network connections, routing tables, and other network interface statistics. |
| Rootkit | N/A | A type of malicious software designed to gain unauthorized access to a computer while masking its existence or the existence of other software. |
| AUP | Acceptable Use Policy | A set of rules applied by the owner or manager of a network, website, or service, that restrict the ways in which it may be used. |
| OS | Operating System | The primary software that manages all the hardware and software on a computer, such as Windows, macOS, or Linux. |
| VPN | Virtual Private Network | A service that protects your internet connection and privacy online by creating an encrypted tunnel for your data. |
| CPU | Central Processing Unit | The primary component of a computer that performs most of the processing for installed hardware and software. |
| AV | Antivirus | Software designed to detect and destroy computer viruses and other malicious software. |
8. Final thoughts
Feeling watched is unsettling, but taking control of your digital privacy is one of the most empowering things you can do. By moving from suspicion to investigation and having a clear action plan, you can regain your peace of mind. Remember that you have the right to privacy, especially on your personal devices. Staying vigilant isn’t about being paranoid; it’s about being proactive in a digital world.
Here are the most critical takeaways from our guide:
- Trust Your Instincts: If your computer feels ‘off’ – slower, buggier, or behaving strangely – it’s worth investigating. Performance issues are often the first sign of hidden software.
- Use Your Tools: Your operating system has built-in utilities like Task Manager and Activity Monitor that are powerful first-response tools for finding suspicious processes.
- Context is Everything: The rules and appropriate reactions for a monitored work computer are completely different from finding spyware on your personal PC.
- Have a Plan: If you find something, don’t panic. Follow the steps: document, disconnect, escalate, and secure.
Your digital security is an ongoing journey, and I’m here to help you navigate it. For more in-depth guides on protecting your digital life, explore our Online Security & Privacy categories on Afdevinfo.









