If you’re trying to understand what does cyber attack mean without getting lost in technical jargon, you’ve come to the right place. In my decade of experience in cybersecurity, I’ve seen how confusing these terms can be for most people. The news is filled with stories of data breaches and hackers, but the basics often get overlooked. My goal here at Afdevinfo.com is to demystify these concepts, giving you the clear, practical knowledge you need to stay safe online.
This article demystifies the complex world of cyber attacks. Here are the key takeaways you need to know:
- Definition: A cyber attack is a deliberate and malicious attempt to breach a digital system.
- Common Types: The most frequent attacks are Phishing (deception), Ransomware (extortion), and Malware (malicious software).
- Targets & Motives: Attacks target both individuals and organizations, primarily driven by financial gain.
- Warning Signs: Watch for odd emails, a slow computer, suspicious bank charges, or account lockouts.
- Emergency Response: If attacked, immediately disconnect from the internet, change critical passwords (on a safe device), and run an antivirus scan.
- Core Defense: Awareness (being vigilant) and enabling Two-Factor Authentication (2FA) everywhere are your best protection.
1. What is a cyber attack? A simple definition for everyone
Before we dive deep, let’s establish a clear and simple foundation. Understanding the core concept is the first step toward protecting yourself.
Heard the term ‘cyber attack’ but not sure what it really means? At its heart, the idea is quite simple. It’s not about complex code or Hollywood-style hacking scenes; it’s about intent. To put it plainly, it’s an attack that happens in the digital world instead of the physical one.
A cyber attack is a deliberate and malicious attempt by an individual or organization to breach the information system of another person or organization.
The keywords here are ‘deliberate’ and ‘malicious’. These aren’t accidents. They are calculated actions designed to cause harm, whether it’s stealing your money, your data, or simply causing chaos. I find it helpful to use an analogy: A cyber attack is like someone trying to break into your house (your computer or account) through a digital window or door to steal things (your data), cause damage (disrupt your services), or install surveillance (spyware).
2. The evolution of cyber attacks
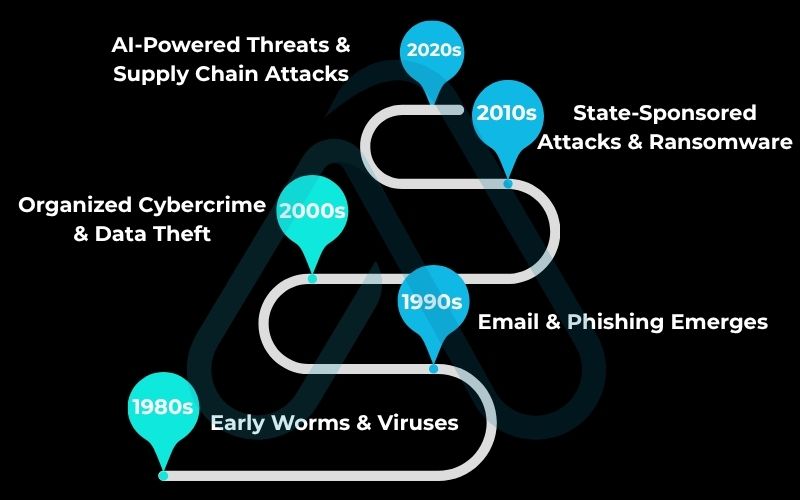
To understand the threats we face today, it helps to see how they’ve evolved. What started as simple pranks has morphed into a multi-billion dollar criminal industry and a new form of global conflict.
Here’s a quick look at the major eras of cyber attacks:
- 1980s (Early Worms & Viruses): This was the era of digital graffiti. Early attacks were often created by hobbyists and academics to prove a point, spreading slowly through floppy disks. They were disruptive but rarely had financial motives.
- 1990s (Email & Phishing Emerges): With the rise of the internet and email, attackers found a new way to reach victims directly. This decade saw the birth of phishing, where deceptive emails tricked people into revealing personal information.
- 2000s (Organized Cybercrime & Data Theft): The dot-com boom meant valuable data, credit card numbers, personal identities was now stored online. Cyber attacks shifted from pranks to profit, with organized criminal groups focusing on large-scale data theft.
- 2010s (State-Sponsored Attacks & Ransomware): Nations began using cyber attacks for espionage and warfare. Simultaneously, ransomware exploded, allowing criminals to encrypt a victim’s files and demand payment, targeting everything from personal laptops to hospital networks.
- 2020s (AI-Powered Threats & Supply Chain Attacks): Today, we face the most sophisticated cybersecurity threats yet. Attackers use AI to create more convincing phishing scams, and they target software supply chains to cause a massive information system breach affecting thousands of companies at once.
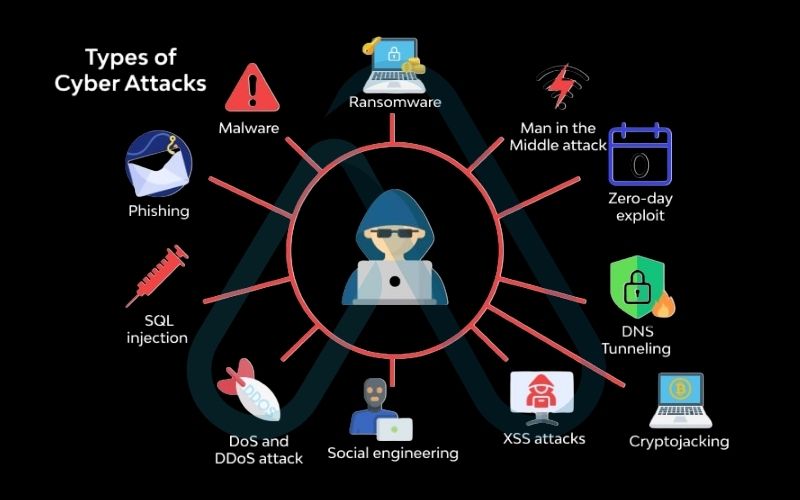
3. What are the most common types of cyber attacks?
While the methods behind cyber attacks can be incredibly complex, I’ve found that most of them fall into a few common categories. Understanding these core types is crucial for recognizing them in the wild.
3.1. Phishing: The deceptive lure
Phishing is a form of social engineering, which means it preys on human psychology rather than technical flaws. The attacker’s goal is to trick you into willingly giving up sensitive information. They do this by masquerading as a trustworthy entity.
Imagine getting an email that looks like it’s from Netflix, asking you to update your payment details via a link. That’s a classic phishing attempt to steal your credit card info. These attacks can come through email, text messages (smishing), or even phone calls (vishing).
3.2. Ransomware: The digital hostage-taker
Ransomware is a particularly nasty type of malicious software. Once it infects your device, it encrypts your files, documents, photos and everything, making them completely inaccessible. The attacker then displays a message demanding a ransom, usually in cryptocurrency, in exchange for the decryption key. This affects both individuals who might lose precious family photos and large organizations like hospitals, which have been forced to shut down critical services.
| Warning I strongly advise against ever paying the ransom, as there’s no guarantee you’ll get your data back, and it funds criminal activity. |
3.3. Malware: The uninvited guest
Malware, short for ‘malicious software,’ is the broad umbrella term for any software designed to cause harm. It’s the parent category for viruses, spyware, trojans, and even ransomware. Its core function is to cause disruption, steal data, or gain unauthorized access to a system.
| Think of it this way if your computer is a house, malware is a catch-all term for any unwelcome pest inside, whether it’s a termite (virus) eating the structure or a hidden camera (spyware) watching you. Any malicious activity on your computer is likely due to some form of malware. |
3.4. Denial-of-service (DoS/DDoS) attacks
Unlike the other attacks that focus on stealing data, the goal of a Denial-of-Service (DoS) attack is to make an online service unavailable to its legitimate users. The attacker floods a target server or network with so much traffic that it becomes overwhelmed and crashes. A Distributed Denial-of-Service (DDoS) attack is even more powerful, using a network of thousands of compromised computers (a ‘botnet’) to launch the flood.
I often use the analogy of a thousand people calling a pizza shop at the same time, so no real customers can get through. This tactic is commonly used against specific targets, as listed below.
- Websites and web servers
- Online gaming platforms
- Business services and applications

4. Cyber attack vs. security breach vs. cybercrime: What does it all mean?
In news reports and daily conversation, these terms are often used interchangeably, but in my field, they have distinct meanings. Clarifying them helps you understand exactly what’s happening.
Here is a simple table to break down the differences:
| Term | Simple Definition | Example |
|---|---|---|
| Cyber Attack | The action or attempt to gain unauthorized access or cause damage to a digital system. | A hacker sending a phishing email to an employee. |
| Security Breach | The result of a successful cyber attack, where an intruder gets past security defenses. It’s a confirmed information system breach. | The hacker’s phishing email works, and they successfully access the company’s internal network. |
| Cybercrime | Any illegal act that involves a computer or network. It’s the overarching legal term. | Using the access from the security breach for data theft and selling customer information online. |
5. Who gets targeted and why in the real-world impact?
A common misconception I hear is that cyber attacks are random. While some are, most are highly targeted with specific motivations behind them. It’s not just about faceless corporations; it affects all of us.
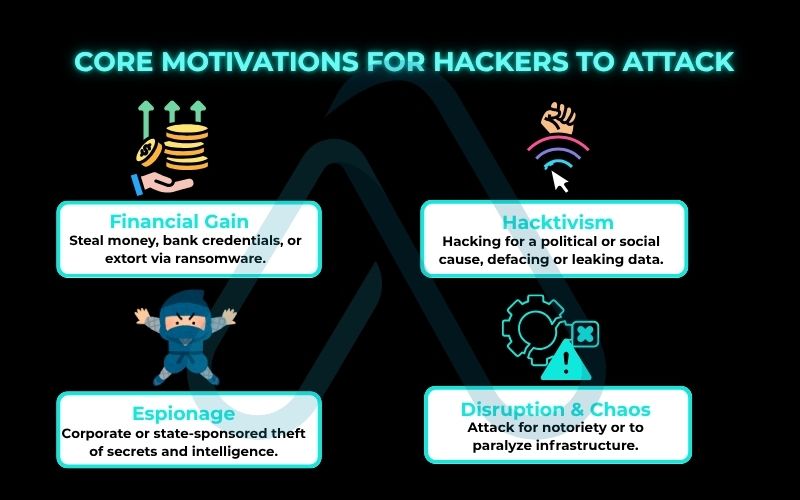
Here are the primary motivations I see behind most attacks:
- Financial Gain: The most common driver. This includes stealing bank credentials, credit card info, or extorting money via ransomware.
- Espionage: This can be corporate (stealing trade secrets from a competitor) or state-sponsored (governments hacking each other for intelligence).
- Activism (‘Hacktivism’): Hacking for a political or social cause, often involving defacing websites or leaking sensitive documents to expose wrongdoing.
- Disruption/Chaos: Some attackers are simply motivated by the desire to cause mayhem, disrupt critical infrastructure, or prove they can.
5.1. For individuals: It’s personal
For you and me, the impact of a cyber attack is deeply personal. It’s an invasion of our digital lives. Your bank account, your private photos, your personal identity, these are the targets. The consequences can be devastating and long-lasting.
Potential damages for an individual include:
- Stolen money directly from bank accounts.
- Fraudulent credit cards or loans opened in your name.
- Compromised social media or email accounts used to scam your friends and family.
- Personal data, photos, or conversations being sold on the dark web or used for blackmail.
5.2. For organizations: It’s catastrophic
When a business, government, or hospital is attacked, the scale of the damage is magnified, and it creates a ripple effect that impacts customers and citizens that means us. An attack on a single company can expose the personal data of millions of its users.
Here are the primary ways organizations are affected:
- Financial Loss: This includes the cost of remediation, regulatory fines, legal fees, and lost business revenue during downtime.
- Reputational Damage: Trust is a currency. A major breach can cause customers to lose faith in a company’s ability to protect their data, leading them to take their business elsewhere.
- Operational Disruption: A ransomware attack can halt a factory’s production line, a hospital’s ability to access patient records, or a city’s public services.
5.3. Case studies: Recent high-profile cyber attacks
Theory is one thing, but real-world examples drive the point home. These events show how the concepts we’ve discussed play out.
| Case Study | Details | Lesson Learned |
| Case Study 1: The Colonial Pipeline Ransomware Attack | In 2021, a ransomware attack forced the shutdown of a major fuel pipeline in the United States, causing fuel shortages along the East Coast. The attackers gained access through a single compromised password that was not protected by multi-factor authentication. | Critical infrastructure is a major target, and the security of a massive system can hinge on a single, simple oversight. Basic cyber hygiene, like using 2FA, is non-negotiable. |
| Case Study 2: The MOVEit Data Breach | A vulnerability in a popular file transfer tool called MOVEit was exploited by a cybercrime group, leading to a massive supply chain attack in 2023. By breaching this one piece of software, the attackers stole data from hundreds of organizations that used it, including government agencies, universities, and major corporations. | Your security is only as strong as the security of your software providers. This highlights the interconnected nature of modern cybersecurity threats. |
6. How can you tell if you are being targeted by a cyber attack?
Recognizing the early warning signs is your best defense. I always tell people to think of it like a digital health check-up; catching the symptoms early can prevent a full-blown illness. The key is to be observant and not dismiss unusual activity.
Here are 7 red flags that you might be under attack:
- Unexpected Password Reset Emails: If you get emails from services like Google, Apple, or your bank asking to reset a password you didn’t request, it’s a huge sign someone is trying to get into your account.
- Strange Activity on Bank Statements: Small, unfamiliar charges are often a test by criminals to see if a stolen card number is active before they make larger purchases.
- Your Computer is Unusually Slow or Crashing: Malware running in the background can consume system resources, causing your device to lag, overheat, or crash frequently.
- Friends Receive Messages You Didn’t Send: If your contacts report getting odd emails or social media messages from you, your account has likely been compromised and is being used to spread spam or scams.
- Antivirus Alerts or Disabled Security Software: Frequent pop-ups from your antivirus are a clear warning. Even more concerning is if you find your antivirus or firewall has been turned off without your permission.
- Unwanted Browser Toolbars or Pop-ups: If your browser homepage has changed or you’re seeing a flood of pop-up ads, you’ve likely installed adware, a common type of malware.
- You’re Suddenly Locked Out of Your Accounts: If your password suddenly stops working for an account, an attacker may have already gotten in and changed it to lock you out.

7. What should you do first if you suspect an attack?
This is the moment where it’s easy to panic, but having a clear plan is your most powerful tool. If you suspect you’re under attack, don’t panic. Based on my experience helping people through these situations, here is your immediate action plan.
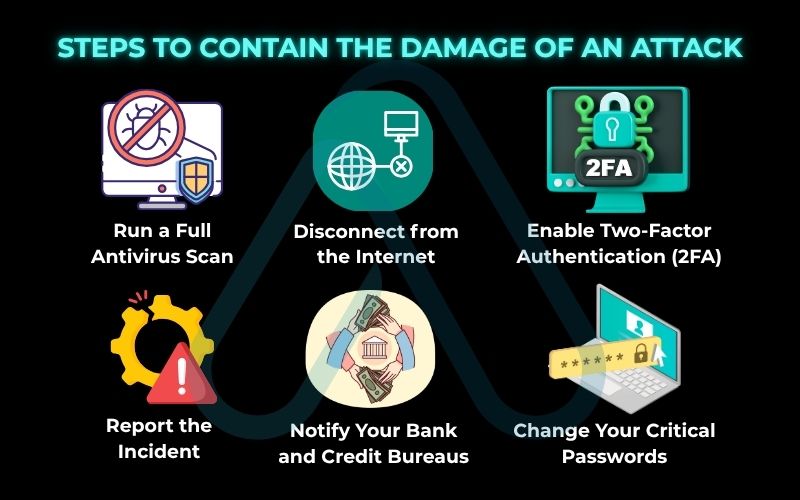
Follow these steps in order to contain the damage:
- Disconnect from the Internet: The first and most critical step. Unplug your Ethernet cable or turn off your Wi-Fi. This severs the attacker’s connection to your device and prevents malware from spreading further across your network or sending more of your data out.
- Change Your Critical Passwords: From a separate, trusted device (like your smartphone using cellular data, not your compromised Wi-Fi), immediately change the passwords for your most important accounts: email, banking, and social media. Start with your primary email, as it’s often the key to resetting other accounts.
- Run a Full Antivirus Scan: Use a reputable antivirus program to perform a full, deep scan of your system. This may take a while, but it’s essential for identifying and quarantining any malware on your device.
- Notify Your Bank and Credit Bureaus: If you suspect any financial information was at risk, contact your bank and credit card companies immediately. They can freeze your accounts and monitor for fraudulent activity. Consider placing a fraud alert with the major credit bureaus.
- Enable Two-Factor Authentication (2FA): On every account that offers it, turn on 2FA. This provides a crucial second layer of security, requiring a code from your phone in addition to your password to log in. This single step could have prevented many of the breaches I’ve investigated.
- Report the Incident: Report the cybercrime to the relevant authorities. In the U.S., this would be the FBI’s Internet Crime Complaint Center (IC3). This helps law enforcement track criminal groups and can aid in your recovery process.
8. FAQs about what does cyber attack mean
Here are some of the most common questions I get asked about this topic, answered in a straightforward way.
Why are cyber attacks increasing nowadays?
Because there are more digital targets, hacking tools are more accessible, and cybercrime is highly profitable.
Can a cyber attack be stopped?
While not all attacks are preventable, most are. Strong security practices (strong passwords, 2FA, phishing awareness) greatly reduce personal risk.
Is my smartphone vulnerable to cyber attacks?
Yes, absolutely. Your phone is a prime target vulnerable to phishing, malware, malicious apps, and ‘smishing’ (SMS phishing).
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| 2FA | Two-Factor Authentication | A security process requiring two different authentication factors to verify a user’s identity. |
| DDoS | Distributed Denial-of-Service | A DoS attack launched from multiple compromised devices (a botnet). |
| DoS | Denial-of-Service | A cyber attack meant to shut down a machine or network, making it inaccessible to its intended users. |
| IoT | Internet of Things | A network of physical objects embedded with sensors and software to connect and exchange data with other devices over the internet. |
| Malware | Malicious Software | Any software intentionally designed to cause disruption to a computer, server, client, or computer network. |
| Phishing | N/A | A type of social engineering attack used to steal user data, including login credentials and credit card numbers. |
| Ransomware | N/A | A type of malware that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid. |
| Cybersecurity | N/A | The practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. |
9. Final thoughts: From awareness to action
We’ve covered a lot, from what a cyber attack means to its real-world impact and what you can do about it. My goal was to strip away the complexity and show that at its core, cybersecurity is about awareness and simple, consistent actions. Understanding that a cyber attack is a deliberate attempt to breach your digital life is the first step, but it’s what you do with that knowledge that truly matters.
Here are the most critical takeaways I want you to remember:
- It’s About Intent: A cyber attack is a malicious and deliberate act, not an accident.
- You Are a Target: Both individuals and organizations are targeted for specific reasons, most often financial gain.
- Awareness is Your Best Defense: Recognizing the signs of phishing and other common attacks can stop them before they cause damage.
- Proactive Steps Matter Most: Simple actions like using strong passwords, enabling 2FA, and keeping software updated are your strongest shields.
By reading this article, you’ve already taken the most important step in protecting your digital life. Now, it’s time to turn that knowledge into action. At Afdevinfo, we are dedicated to providing you with the practical tools and guidance you need. For more in-depth guides, explore our Online Security & Privacy categories.


