1. What is digital security? A clear definition for 2025
Over my decade in this field, I’ve seen a lot of confusion around this topic. So, let’s start with a clear what is digital security definition for today’s world. Think of it less as just one lock on your front door and more as the entire security system for your home—the locks, the alarm, the cameras, and even the insurance policy. It’s about protecting your entire digital life, not just one part of it.
Digital security is the comprehensive practice of protecting all your online assets, identity, and data from unauthorized access, use, or theft. It covers everything from your social media accounts and emails to your financial data and personal devices.
This holistic approach to digital information security is crucial because our lives are more integrated with technology than ever before. We’re not just protecting a computer anymore; we’re protecting our identity, finances, and reputation across a vast network of interconnected services.
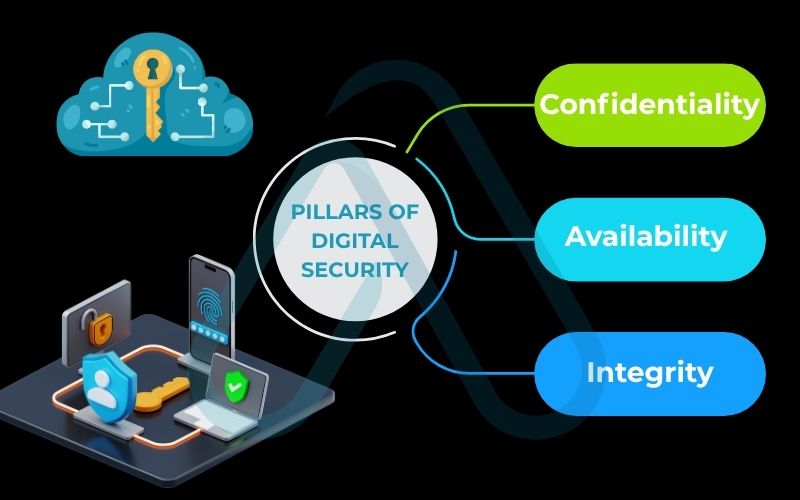
1.1. The three pillars of digital security
At the core of all good security practices is a framework known as the CIA Triad. It’s a foundational model I always come back to because it simplifies what we’re trying to achieve. It consists of three key principles.
Here’s what each pillar means in practice:
- Confidentiality: This is about privacy and secrecy. It ensures that your data is accessible only to authorized users. In simple terms, it’s the guarantee that only you and the intended recipient can read your private messages on Signal.
- Integrity: This pillar ensures that your data is accurate, consistent, and trustworthy. It means that the information has not been altered or tampered with. A perfect example is your online bank statement; integrity guarantees the numbers you see haven’t been secretly changed.
- Availability: This is about access. It ensures that you can access your data and services whenever you need to. When you need to pull an important file from your cloud storage for a meeting, availability is what makes that possible without disruption.
2. Why digital security is more critical than ever
The conversation around digital security has shifted dramatically. It’s no longer a ‘nice-to-have’ for the tech-savvy; it’s an absolute ‘must-have’ for everyone. According to IBM’s 2023 Cost of a Data Breach Report, the average cost of a breach has hit an all-time high of $4.45 million. While that’s a corporate number, it reflects a surge in sophisticated digital security threats that directly impact our daily lives and demand better online identity protection.
2.1. The 2025 digital threat map: A visual guide
To understand why security is so important, you need to know what you’re up against. The threat landscape of 2025 is more complex than ever, powered by automation and artificial intelligence. I’ve seen these threats evolve firsthand, moving from simple viruses to highly sophisticated, targeted attacks.
Here are some of the common digital security threats in 2025 that I’m seeing most often:
- AI-Powered Phishing: Phishing emails are no longer full of typos. AI now crafts perfectly convincing, personalized messages that are incredibly difficult to distinguish from legitimate communications.
- Deepfake Scams: Malicious actors use AI to create fake audio or video of someone you trust, like a boss or family member, to trick you into sending money or revealing sensitive information.
- Ransomware-as-a-Service (RaaS): Cybercriminals no longer need to be coding geniuses. They can now ‘rent’ ransomware tools, leading to a massive increase in attacks against individuals and small businesses.
- IoT Vulnerabilities: Every smart device in your home—from your TV to your doorbell—is a potential entry point for attackers if not properly secured.

2.2. Personal vs. organizational risks: What’s at stake?
The stakes are high for everyone, but what’s at risk differs depending on whether you’re an individual or a business. Understanding the distinction in personal vs organizational digital security helps you focus your protective efforts where they matter most.
For You (The Individual)
For individuals, the risks are deeply personal. A breach could mean having your social media account taken over and used to scam your friends, seeing fraudulent charges on your credit card, or, in the worst case, having your entire identity stolen. The consequences are direct financial loss, reputational damage, and immense personal stress.
For Your Business
For an organization, the risks scale up dramatically. A single breach can lead to massive financial losses from operational disruption, regulatory fines (like those under GDPR), and the cost of remediation. Beyond the financials, a public data breach can shatter customer trust and cause irreparable damage to the company’s reputation, as we’ve seen with many well-known corporate data breaches.
3. Digital security vs. cybersecurity vs. data security: The definitive comparison
One of the most common questions I get is about the difference between all these security terms. They’re often used interchangeably, but they have distinct meanings. I like to use an umbrella analogy to clear things up.
Think of Digital Security as the big umbrella. It’s the all-encompassing strategy for protecting your entire digital presence—your identity, assets, and technology. Under that umbrella, you have Cybersecurity, which is a major component focused specifically on defending against digital attacks. It’s the practice of protecting networks, devices, and systems from malicious actors. A smaller, more focused practice under that same umbrella is Data Security, which is all about protecting the data itself, through things like encryption and access controls, no matter where it lives.
3.1. Comparison table: What matters most for you?
To make the difference between cybersecurity and digital security even more practical, it helps to see how the focus changes based on who you are. This table breaks down the priorities for different user types.
I’ve created this table to show you where your focus should be:
| User Type | Primary Focus | Key Concerns | Example Priority |
|---|---|---|---|
| Individual User | Digital Security | Identity theft, online privacy, financial scams, account takeovers. | Using strong, unique passwords with a password manager and enabling Multi-Factor Authentication (MFA) on all important accounts. |
| Small Business Owner | Cybersecurity & Data Security | Data breaches, ransomware, business email compromise, compliance. | Implementing employee security training, maintaining secure data backups, and securing the company’s Wi-Fi network. |
| Enterprise IT Manager | Cybersecurity, Data Security, & Governance | Advanced persistent threats (APTs), regulatory compliance (GDPR, CCPA), insider threats, supply chain attacks. | Deploying a comprehensive Security Operations Center (SOC), conducting regular vulnerability assessments, and managing access controls. |
4. Your interactive guide: How much digital security do you need?
I firmly believe that a ‘one size fits all’ approach to security is a myth. The level of protection you need depends entirely on your digital footprint and activities. To help you figure this out, I’ve designed the logic for a simple assessment tool. It’s a starting point to help you build a security plan tailored to your life or business.
4.1. A decision flowchart for individuals and businesses
This flowchart is designed to guide you to one of three security levels: Essentials, Advanced, or Comprehensive. Follow the path that applies to you to see which checklist in the next section is your best starting point.
Path 1: For Individuals
- Do you use online banking or shopping?
- If Yes: Do you store sensitive personal documents (like tax returns or medical records) in the cloud?
- If Yes: You should start with the Advanced checklist.
- If No: You should start with the Essentials checklist.
- If No: Do you have any online accounts at all (email, social media)?
- If Yes: You should start with the Essentials checklist.
- If No: You have a minimal digital footprint, but basic precautions are still wise.
Path 2: For Businesses
- Do you handle or store any customer data (names, emails, payment info)?
- If Yes: Are you subject to data protection regulations like GDPR or CCPA?
- If Yes: You need a Comprehensive security strategy. Start with our small business checklist and consult a security professional.
- If No: You should start with the Advanced (small business) checklist as a minimum baseline.
- If No: You should still start with the Essentials (small business) checklist to protect company assets and accounts.
5. A practical quick-start guide to improving your digital security
Now that you have an idea of what you need, it’s time for the ‘now what?’. This section provides actionable data protection strategies you can implement today. Based on your result from the flowchart, you can use these checklists as your starting point. These security tools and techniques are some of the most effective ways to protect yourself.
5.1. Checklist for individuals: 5 steps to protect your online identity
For personal security, focus on high-impact actions that give you the most protection for the least effort. Here are five steps I recommend everyone take.
- Enable Multi-Factor Authentication (MFA) Everywhere. This is your single most powerful defense against account takeovers. It requires a second form of verification (like a code from an app) in addition to your password. Use an app like Authy or Google Authenticator.
- Use a Password Manager. It’s impossible for humans to remember strong, unique passwords for every account. A password manager like Bitwarden (which has an excellent free tier) creates and stores them for you securely.
- Keep Your Software Updated. Security updates patch vulnerabilities that attackers exploit. Enable automatic updates on your operating system, web browser, and other applications whenever possible.
- Recognize and Avoid Phishing Scams. Be skeptical of any unsolicited email or message that asks for personal information or creates a sense of urgency. Hover over links before clicking to see the actual destination URL.
- Review Your Privacy Settings. Regularly check the privacy and security settings on your key accounts like Google, Facebook, and X (formerly Twitter). Limit the amount of personal information you share publicly.

5.2. Checklist for small businesses: 5 foundational security measures
For small businesses, foundational security measures are critical for building trust and ensuring business continuity. Here are five essential steps.
- Conduct Regular Employee Security Training. Your employees are your first line of defense. Train them to recognize phishing, use strong passwords, and handle sensitive data securely. Make it a recurring part of your onboarding process.
- Implement a Data Backup and Recovery Plan. In the event of a ransomware attack or hardware failure, having secure, tested backups is the only thing that can save your business. Follow the 3-2-1 rule: three copies of your data, on two different media, with one copy off-site.
- Secure Your Wi-Fi Network. Change the default administrator password on your router, use WPA3 encryption if available (WPA2 at a minimum), and create a separate network for guests to keep business traffic isolated.
- Enforce a Strong Access Control Policy. Give employees access only to the data and systems they absolutely need to perform their jobs (the principle of least privilege). This limits the potential damage if one of their accounts is compromised.
- Use Endpoint Protection. Ensure every device that connects to your network (computers, servers, mobile phones) is protected with professional-grade antivirus and anti-malware software that is centrally managed and kept up to date. For excellent free resources, I recommend checking out CISA’s cybersecurity resources for small businesses.

6. The evolving landscape: Global regulations you need to know
Digital security isn’t just about technology; it’s also about law and compliance. Governments around the world are implementing regulations to protect consumer data, and understanding them is crucial, especially for businesses. These laws are a key part of modern data protection strategies.
Here’s a high-level overview of the key regulations you should be aware of:
- GDPR (General Data Protection Regulation): A European Union law that sets a strict standard for data protection and privacy. It affects any organization worldwide that processes the data of EU citizens, granting individuals significant control over their personal data.
- CCPA/CPRA (California Consumer Privacy Act/California Privacy Rights Act): A California-specific law that gives consumers more control over the personal information that businesses collect about them. It includes rights to know, delete, and opt-out of the sale of their personal information.
- Emerging AI Data Laws: This is a rapidly developing area. New regulations are being proposed globally to govern how personal data is used to train artificial intelligence models. The core principles often revolve around transparency (knowing your data is being used), fairness (preventing biased outcomes), and accountability. Staying informed on this is key for future compliance.
7. Frequently asked questions
I’ve compiled answers to some of the most common questions I hear about digital security. This should help clarify any lingering doubts you might have.
What is the difference between digital security and cybersecurity?
Think of digital security as the overall strategy to protect your entire online world, including your identity, data, and assets. Cybersecurity is a specific and crucial part of that strategy focused on defending your networks, computers, and systems from digital attacks.
What are some examples of digital security tools?
Here are some of the most essential types of tools I recommend for everyday use:
- Password Managers (e.g., Bitwarden)
- Virtual Private Networks (VPNs) (e.g., ProtonVPN)
- Antivirus Software (e.g., Malwarebytes)
- Encrypted Messaging Apps (e.g., Signal)
How can I protect my online identity and data?
The three most critical actions you can take right now are: first, get a password manager to create and store strong, unique passwords for every account. Second, enable Multi-Factor Authentication (MFA) on all critical accounts like your email and banking. Third, learn to be cautious and skeptical of unsolicited emails to avoid phishing attacks.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| AI | Artificial Intelligence | The simulation of human intelligence in machines, used in both security tools and malicious attacks. |
| CIA Triad | Confidentiality, Integrity, and Availability | A foundational model for guiding information security policies and practices. |
| CCPA/CPRA | California Consumer Privacy Act / California Privacy Rights Act | California laws granting consumers rights and control over their personal data. |
| GDPR | General Data Protection Regulation | An EU law that regulates how companies protect the personal data of its citizens. |
| IoT | Internet of Things | A network of physical devices (like smart home gadgets) embedded with sensors and software that connect to the internet. |
| MFA | Multi-Factor Authentication | A security method that requires two or more verification factors to gain access to an account. |
| Phishing | N/A | A type of social engineering attack where attackers trick victims into revealing sensitive information. |
| RaaS | Ransomware-as-a-Service | A business model where cybercriminals rent out ransomware tools to other attackers. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your IP address, enhancing online privacy. |
8. Final thoughts
Navigating the digital world can feel overwhelming, but securing it doesn’t have to be. As I’ve shown, digital security is a broad discipline, but protecting yourself boils down to understanding the risks and taking practical, consistent steps to mitigate them. It’s not about becoming a security expert overnight; it’s about building better habits.
Here are the key takeaways I want you to remember:
- Digital security is the holistic protection of your entire digital life, not just your devices.
- The most effective personal security measures are also the simplest: use a password manager, enable MFA, and stay vigilant against phishing.
- Your security needs are unique. Use the provided guidance to assess what level of protection is right for you or your business.
Protecting your digital life is an ongoing process, but it’s one you are fully capable of managing. Taking these small steps today will build a much safer foundation for your future online. For more in-depth guides, explore our Online Security and Digital Tools categories on Afdevinfo.com.


