1. Understanding the cyber threat landscape in 2025
If you’re trying to understand what kind of cyber attacks are there, you’re not alone. The term ‘cyber attack’ is everywhere, but what does it actually mean for you, your business, or your data? After more than a decade in cybersecurity, I’ve seen firsthand how overwhelming the jargon can be. This guide cuts through the noise. It’s not just another list; it’s an up-to-date, personalized roadmap to understanding the threats that matter most in 2025 and beyond.
To help you navigate this complex world, here’s what I’ll cover in this guide:
- The Evolution of Threats: How attacks have shifted from simple viruses to sophisticated, AI-powered campaigns.
- A Simple Framework: Breaking down all attacks into three easy-to-understand pillars.
- A Deep Dive into Common Attacks: Clear explanations of phishing, ransomware, DDoS, and more.
- Personalized Prevention: Actionable checklists tailored specifically for you, whether you’re an individual, a small business owner, or an IT professional.
2. The evolution of cyber attacks: A 2024-2025 timeline
The world of cyber attacks is anything but static. What worked for a hacker five years ago is often obsolete today. I’ve watched this evolution closely, seeing a dramatic shift from broad, shotgun-style attacks to hyper-targeted, surgically precise campaigns. The rise of Ransomware-as-a-Service (RaaS) has industrialized digital extortion, while the increase in supply chain cyber attacks shows that attackers are thinking strategically, targeting weaker links to compromise bigger targets. These evolving network security threats require a modern understanding of the landscape.
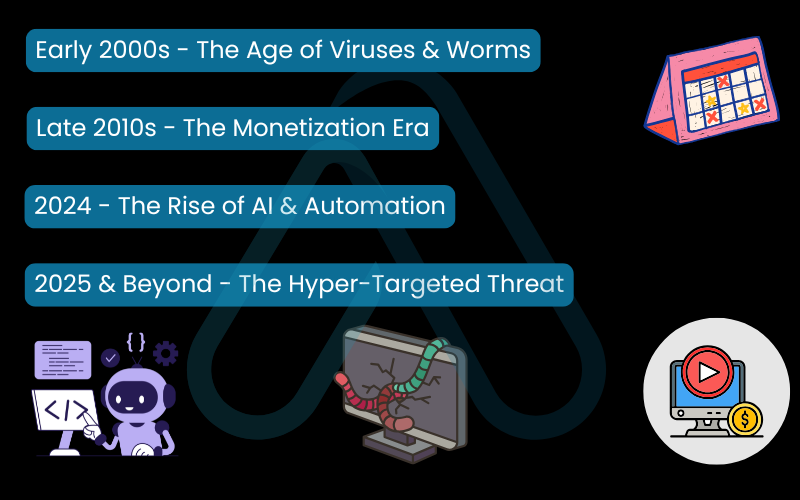
Here’s a simplified timeline of the key shifts I’ve observed leading into 2025:
- Early 2000s – The Age of Viruses & Worms: Attacks were often about disruption or demonstrating technical skill, spreading rapidly but with less financial motive.
- Late 2010s – The Monetization Era: Ransomware becomes a dominant force, turning cyber attacks into a highly profitable criminal enterprise. Data breaches focus on stealing financial and personal information for sale on the dark web.
- 2024 – The Rise of AI & Automation: Attackers begin using AI to craft incredibly convincing phishing emails at scale. Ransomware gangs adopt a ‘double extortion’ model, not just encrypting data but also stealing it and threatening to leak it.
- 2025 & Beyond – The Hyper-Targeted Threat: We’re now seeing the weaponization of deepfakes for highly personalized vishing and whaling attacks. Supply chain attacks become a primary vector, exploiting trust in software vendors to infiltrate thousands of businesses at once.
3. The primary pillars of cyber attacks: A simple framework
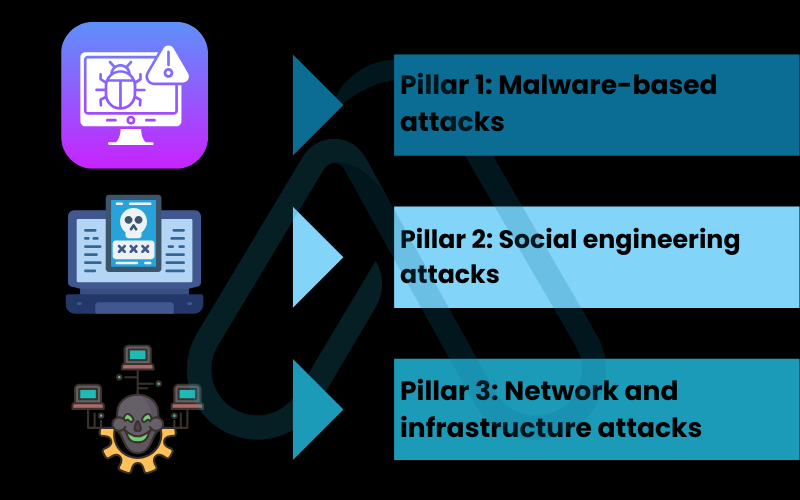
To truly understand the threats we face, we need a simple way to categorize them. I find it helpful to think of cyber attacks like different ways a burglar might break into a house. They could use a malicious tool (like a lockpick), trick the owner into opening the door, or attack the house’s structure itself (like the door or a window). Similarly, I group all cyber attacks into three primary pillars.
3.1. Pillar 1: Malware-based attacks
This is the ‘malicious tool’ pillar. Malware, short for malicious software, is any piece of code designed to harm, disrupt, or gain unauthorized access to a computer system. It’s the weapon an attacker deploys once they find a way into your digital home. Understanding the different types of malware attacks is fundamental to good cybersecurity.
Here are the most common forms of malware I encounter:
- Ransomware:
What it is: Software that encrypts your files, making them inaccessible until you pay a ransom to the attacker.How it works: It typically spreads through phishing emails or unpatched software vulnerabilities. Once executed, it scrambles your data and displays a ransom note.Real-World Example: The 2017 WannaCry attack crippled hospitals and businesses worldwide by encrypting their critical files.
- Viruses:
What it is: Malicious code that attaches itself to a legitimate program or file.How it works: It requires human action, like opening an infected document, to execute and spread. Once active, it can corrupt files, steal data, or take over your machine.Real-World Example: The infamous ILOVEYOU virus in 2000 spread via email attachments, causing billions in damages.
- Trojans:
What it is: Malware disguised as a legitimate piece of software.How it works: You might download what you think is a useful utility, but it secretly contains a malicious payload that creates a backdoor for attackers.Real-World Example: The Emotet trojan often masquerades as a financial document, but once opened, it steals banking credentials and installs other malware.
3.2. Pillar 2: Social engineering attacks
This is the ‘human manipulation’ pillar. Social engineering is the art of psychological manipulation, tricking people into divulging sensitive information or performing actions that compromise security. It bypasses technical defenses by targeting the most vulnerable element: human trust. These social engineering attacks are often the starting point for a more significant breach.
Attackers prey on basic human emotions like fear, urgency, curiosity, and the desire to be helpful. A classic example is an email that looks like it’s from your CEO (a figure of authority) asking for an urgent wire transfer (urgency). Your instinct to help quickly can override your security sense. Technology alone can’t stop these attacks; it requires awareness and a healthy dose of skepticism.
A Sobering Fact: According to multiple industry reports, social engineering is a factor in over 90% of all successful cyber breaches. This highlights just how critical the human element is in our digital defenses.
3.3. Pillar 3: Network and infrastructure attacks
This is the ‘structural’ pillar. Instead of tricking a person or using malware on a single device, these attacks target the underlying systems and connectivity that power our digital lives. Think of it like the highway system: malware is a bad car, social engineering tricks a driver, but a network attack creates a massive traffic jam (DDoS) or diverts traffic to a dangerous neighborhood (Man-in-the-Middle).
These attacks are designed to disrupt services, intercept data in transit, or gain a foothold in an organization’s core systems. While less common for individuals, they are a primary concern for businesses and services we all rely on. The rise of sophisticated DDoS and DoS attacks highlights how fragile our online services can be, making these some of the most impactful network security threats today.
4. A closer look at what kind of cyber attacks are there
Now that we have our three-pillar framework, let’s dive into the specifics. I’ll break down the most common cyber attacks you’re likely to encounter, explaining how they work and, most importantly, how you can defend against them.
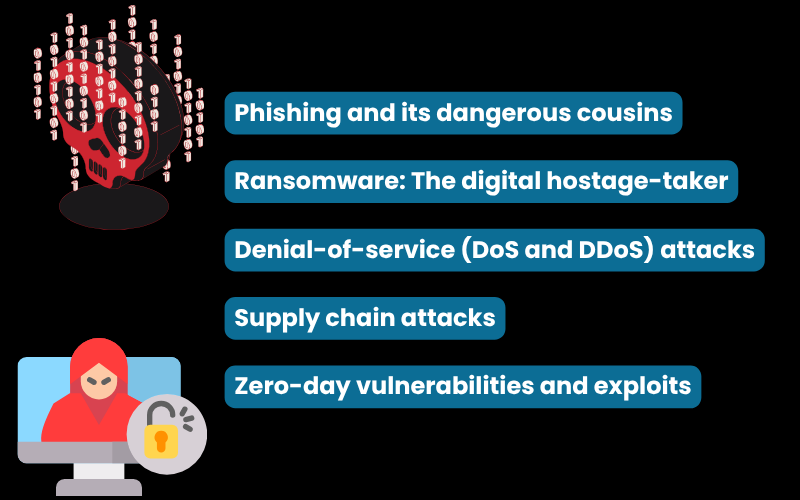
4.1. Phishing and its dangerous cousins
Phishing is one of the most prevalent social engineering attacks. It’s an attempt to trick you into giving up sensitive information like usernames, passwords, or credit card details by masquerading as a trustworthy entity in an electronic communication.
- Definition: Phishing is a broad-cast attack, like a fisherman casting a wide net, hoping to catch any fish.
- Method: Usually an email or text message containing a link to a fake login page or a malicious attachment.
- Example: A generic email from ‘Netflix’ claiming your account is suspended and you must ‘click here’ to update your payment details.
- Key Prevention Tip: Always hover over links before clicking to verify the destination URL, and never enter credentials on a site you didn’t navigate to yourself.
Phishing has several, more dangerous variations:
- Spear Phishing: A targeted attack aimed at a specific individual or organization. The message is highly personalized using information gathered from social media or company websites.
- Whaling: A type of spear phishing aimed at high-profile targets like CEOs or CFOs.
- Smishing: Phishing conducted via SMS text messages.
- Vishing: Phishing conducted over the phone (voice phishing).
To clarify the difference between phishing vs. spear phishing, I’ve put together this simple table:
| Factor | Phishing | Spear Phishing |
|---|---|---|
| Target | Broad, non-specific group | Specific individual or company |
| Personalization | Generic (e.g., ‘Dear Customer’) | Highly personalized (e.g., ‘Hi John, regarding the Q3 report…’) |
| Method | Mass email campaigns | Researched, crafted emails |
| Example | Fake ‘password reset’ email from a social media site | Email appearing to be from your IT department about a new system |
4.2. Ransomware: The digital hostage-taker
Ransomware is one of the most feared types of malware attacks for a reason. It holds your data hostage.
- Definition: Malicious software that encrypts your files, making them inaccessible.
- Method: Attackers demand a ransom, usually in cryptocurrency, in exchange for the decryption key. Modern ransomware often includes ‘double extortion,’ where attackers also steal a copy of your data and threaten to leak it publicly if you don’t pay.
- Example: A hospital’s patient records are encrypted, forcing them to cancel surgeries and revert to paper records until the system is restored or the ransom is paid.
- Key Prevention Tip: The single most effective defense is maintaining regular, offline backups of your critical data.
To answer the critical question, ‘How can I protect myself from ransomware?’, here is my proactive checklist:
- Maintain Offline Backups (3-2-1 Rule): Keep three copies of your data, on two different media types, with at least one copy stored offline or off-site.
- Keep Software Patched: Regularly update your operating system and applications to close the security holes attackers exploit.
- Use Reputable Security Software: A modern antivirus or endpoint protection solution can detect and block many ransomware variants.
- Practice Email Scrutiny: Since phishing is a primary delivery method, be extremely cautious of unexpected attachments or links.
4.3. Denial-of-service (DoS and DDoS) attacks
These are prime examples of network and infrastructure attacks designed to cause disruption.
- Definition: A Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attack aims to make an online service, like a website or application, unavailable to its intended users.
- Method: The attack floods the target system with so much traffic or so many requests that it becomes overwhelmed and either crashes or slows to a halt. The difference is the source: a DoS attack comes from a single source, while a DDoS attack uses thousands of compromised computers (a ‘botnet’) to attack from many sources at once.
- Example: A popular gaming service is taken offline during a major tournament by a massive flood of traffic from a botnet, preventing legitimate players from connecting.
- Key Prevention Tip: For businesses, using a specialized DDoS mitigation service is essential. For individuals, there is little to do but wait for the service provider to resolve the issue.
4.4. Supply chain attacks: The hidden threat
What is a supply chain attack in cybersecurity? It’s one of the most insidious threats because it exploits trust.
- Definition: A supply chain attack is an indirect attack that targets a less secure element in an organization’s ‘supply chain,’ such as a third-party software vendor or service provider.
- Method: By compromising a trusted vendor, attackers can push malicious code or gain access to all of that vendor’s customers. Instead of attacking one company, they attack one and get access to thousands. This is what makes supply chain cyber attacks so dangerous.
- Example: The infamous SolarWinds attack, where hackers injected malicious code into a legitimate software update for SolarWinds’ Orion platform. This update was then sent out to thousands of their customers, including government agencies and major corporations, giving the attackers a backdoor into their networks.
- Key Prevention Tip: For businesses, it’s crucial to vet vendors’ security practices and implement a zero-trust architecture that doesn’t automatically trust internal traffic.
4.5. Zero-day vulnerabilities and exploits
This is the cyber attack equivalent of a surprise attack with an unknown weapon.
- Definition: A ‘zero-day’ vulnerability is a flaw in software or hardware that is unknown to the vendor who created it. An ‘exploit’ is the malicious code attackers write to take advantage of that flaw.
- Method: Because the vendor is unaware of the flaw, there is no patch or fix available when the attack begins—they have ‘zero days’ to prepare a defense. Attackers who discover these vulnerabilities can use them to bypass security measures undetected.
- Example: A flaw is discovered in a popular web browser that allows an attacker to run malicious code on a user’s computer just by them visiting a compromised website.
- Key Prevention Tip: Since you can’t patch an unknown flaw, the best defense is a layered security approach, including robust security software, network monitoring, and a principle of least privilege to limit the damage an exploit can do.
The Lifecycle of a Zero-Day: Understanding the timeline is key. It typically follows this path: Discovery (by an attacker) -> Exploit Creation -> Attack Campaign -> Vendor Awareness (when the attack is discovered) -> Patch Development & Release.
5. Interactive guide: What type of attack are you most vulnerable to?
To make this practical, I’ve created a simple ‘choose your own adventure’ style quiz. Follow the path that best describes you to get a personalized insight into your primary risk areas.
Question 1: Are you primarily concerned with your personal security or the security of a business?
- If PERSONAL: Proceed to the ‘Personal User’ path.
- If BUSINESS: Proceed to Question 2.
Question 2 (Business): Are you a business owner/manager responsible for overall strategy, or an IT specialist who manages the technology?
- If BUSINESS OWNER/MANAGER: Proceed to the ‘SMB Leader’ path.
- If IT SPECIALIST: Proceed to the ‘Enterprise IT’ path.
—
Path 1: The Personal User
Your digital life is vast—social media, online banking, shopping, email. Attackers know this. Your biggest threat is likely Social Engineering (Pillar 2), specifically phishing and smishing. Attackers target you to steal credentials, which they can use for identity theft or to access your financial accounts. Your secondary risk is Malware (Pillar 1), often delivered via phishing emails or malicious downloads.
➡️ Your Action Plan: Focus on the prevention tips in section 6.1. For personal users. Building strong habits around password management and email scrutiny is your best defense.
Path 2: The SMB Leader
As a business leader, you wear many hats. Your biggest threat is twofold: Social Engineering (Pillar 2) targeting your employees and Ransomware (Pillar 1) targeting your business operations. An employee clicking one bad link can lead to a full-blown ransomware attack that could cripple your company. Attackers see SMBs as high-value targets that often lack enterprise-grade defenses.
➡️ Your Action Plan: Your top priorities are employee training and robust data backups. Focus on the actionable checklist in section 6.2. For small and medium businesses.
Path 3: The Enterprise IT Professional
You are on the front lines. While you deal with all threats, your most complex and dangerous challenges come from Network & Infrastructure Attacks (Pillar 3) and sophisticated, targeted campaigns like Supply Chain Attacks and Zero-Day Exploits. Your job is not just to build walls but to detect threats that have already bypassed them.
➡️ Your Action Plan: Your strategy must be proactive and assume a breach is possible. Focus on the high-level concepts in section 6.3. For enterprise IT teams, such as zero-trust architecture and incident response.
6. Your personalized prevention playbook: Actionable checklists
Understanding threats is the first step, but taking action is what truly protects you. Based on my experience, generic advice isn’t enough. Here are tailored checklists for different needs.
6.1. For personal users
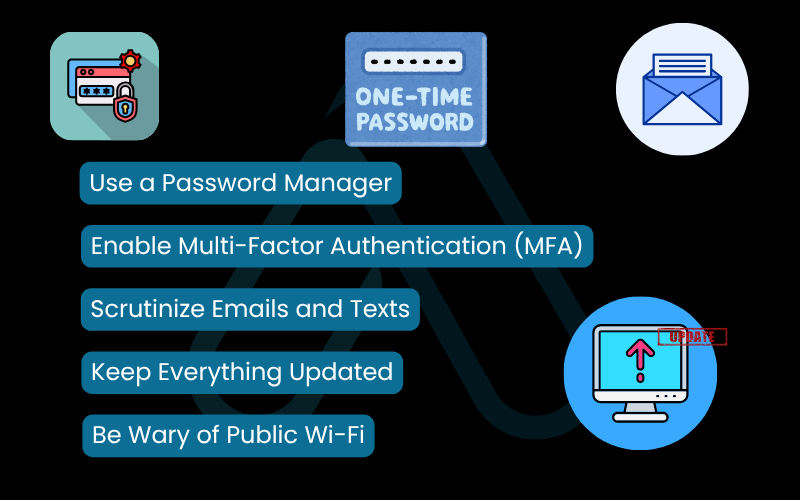
Your goal is to build a strong digital foundation. Here are the essential habits to adopt:
- Use a Password Manager: Create long, strong, and unique passwords for every single account. This is non-negotiable.
- Enable Multi-Factor Authentication (MFA): Turn on MFA (or two-factor authentication) everywhere it’s offered, especially on email, banking, and social media accounts.
- Scrutinize Emails and Texts: Treat any unsolicited communication with suspicion. Look for red flags like a sense of urgency, grammatical errors, and mismatched sender addresses.
- Keep Everything Updated: Enable automatic updates for your operating system, web browser, and other applications to ensure you have the latest security patches.
- Be Wary of Public Wi-Fi: Avoid accessing sensitive accounts (like banking) on public Wi-Fi. If you must, use a reputable VPN to encrypt your connection.
6.2. For small and medium businesses (SMBs)
Your focus should be on high-impact, cost-effective measures that reduce the most significant risks.
- Conduct Employee Security Training: Your staff is your first line of defense. Regularly train them on how to spot phishing emails and other social engineering tactics.
- Implement the 3-2-1 Backup Rule: Your business’s survival may depend on it. Ensure you have three copies of critical data, on two media types, with one stored offline and inaccessible from the network.
- Deploy Endpoint Protection: Go beyond basic antivirus. Modern endpoint protection can detect and respond to more sophisticated threats like ransomware.
- Secure Your Network with a Firewall: A properly configured firewall is a fundamental tool for controlling traffic in and out of your network.
- Assess Vendor Risk: Before integrating a new software or service, perform due diligence on their security practices. You are only as secure as your weakest link.
6.3. For enterprise IT teams
Your playbook is about strategy, resilience, and proactive defense.
- Implement a Zero-Trust Architecture: Operate on the principle of ‘never trust, always verify.’ Authenticate and authorize every connection, regardless of whether it originates inside or outside the network perimeter.
- Develop an Incident Response (IR) Plan: Don’t wait for an attack to happen. Have a documented, tested plan for how you will detect, contain, eradicate, and recover from a security incident.
- Engage in Proactive Threat Hunting: Actively search your networks for signs of compromise rather than passively waiting for alerts. Look for indicators of compromise (IOCs) and anomalous activity.
- Manage Supply Chain Risk: Maintain a software bill of materials (SBOM) and conduct rigorous security assessments of all third-party vendors and software components.
- Utilize Advanced Threat Detection: Deploy solutions like Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) for centralized visibility and correlation of security events across your environment.
7. Cyber attack spotlight: Recent incidents in Africa and EMEA
To show these threats are not just theoretical, it’s important to look at real-world examples. My work at Afdevinfo focuses on providing relevant context, and the Africa and EMEA regions have seen a significant increase in cyber incidents.
Transnet, South Africa (2021)
The Attack: Ransomware. A variant of ransomware hit the IT systems of South Africa’s state-owned port and rail operator, forcing it to declare force majeure and revert to manual processes.
The Impact: The attack caused massive delays at key container terminals, disrupting supply chains and costing the national economy millions.
Key Takeaway: This incident demonstrated the vulnerability of critical national infrastructure and the devastating real-world consequences of a digital attack on operational technology (OT) systems.
Ireland’s Health Service Executive (HSE) (2021)
The Attack: Ransomware (Conti). A phishing email opened by a single staff member eventually allowed the Conti ransomware gang to deploy their malware across the entire national health system’s IT network.
The Impact: The attack was described as the most significant cyber attack on the Irish state ever. It forced the shutdown of all HSE IT systems, causing widespread cancellation of appointments and a reversion to paper-based record-keeping for weeks.
Key Takeaway: It showed how a single point of failure (one person clicking a link) can lead to a catastrophic, nationwide incident, reinforcing the need for both employee training and a zero-trust network model.
8. The future of cyber threats: What’s on the horizon for 2026?
As a technology expert, I’m always looking ahead. The threats of tomorrow are being built on the technology of today. Based on industry reports and my own analysis, here’s what I see on the horizon.
- AI-Driven Social Engineering: We will see a surge in hyper-realistic deepfake audio and video used for vishing and whaling attacks. Imagine getting a video call from your CEO, with their exact face and voice, asking for a wire transfer. The line between real and fake will blur dramatically.
- The Quantum Threat to Encryption: While still a few years away, the development of quantum computing poses a long-term threat to the encryption standards that protect nearly all our digital data today. Organizations need to start planning for a transition to quantum-resistant cryptography.
- Attacks on IoT and OT Environments: As more devices—from smart home appliances (IoT) to industrial control systems (OT)—come online, they become new targets. These devices often lack robust security, creating a massive new attack surface for hackers to exploit for DDoS botnets or to cause physical disruption.
- Weaponized AI vs. Defensive AI: The future of cybersecurity will be an arms race between AI systems. Attackers will use AI to find vulnerabilities and create new malware faster than ever, while defenders will rely on AI to detect these attacks in real-time.
9. Frequently asked questions
Over my years of writing tutorials and guides, I’ve found that some questions come up time and time again. Here are my direct answers to a few of the most common ones.
What is the most common type of cyber attack?
Phishing is widely considered the most common type of cyber attack. The reason is simple: it’s incredibly cheap and easy for attackers to deploy at a massive scale, and it exploits human psychology rather than complex technical vulnerabilities. It remains the number one entry point for almost all other types of attacks.
Can a cyber attack be stopped?
While stopping 100% of cyber attacks is an unrealistic goal, you can drastically reduce your risk and mitigate the impact of a successful attack. The best approach is a layered defense-in-depth strategy. This means combining prevention (firewalls, training), detection (security software, monitoring), and response (an incident response plan, backups) so that if one layer fails, another is there to catch the threat.
What is the difference between a virus and a worm?
The key difference lies in how they spread. A virus requires a host file (like an executable or document) and needs human action to propagate, such as a user opening the infected file. Think of it like a flu you catch by touching a contaminated doorknob. A worm, on the other hand, is a standalone piece of malware that can self-propagate across a network without any human intervention by exploiting vulnerabilities. It’s more like a flu that can travel through the air on its own.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| AI | Artificial Intelligence | The simulation of human intelligence in machines, used by both attackers and defenders. |
| CISA | Cybersecurity and Infrastructure Security Agency | A U.S. federal agency responsible for cybersecurity and infrastructure protection. |
| DDoS | Distributed Denial-of-Service | An attack that uses multiple compromised systems to flood a target with traffic. |
| DoS | Denial-of-Service | An attack from a single source to make a service unavailable. |
| EMEA | Europe, the Middle East, and Africa | A common geographical designation used in business. |
| IoT | Internet of Things | A network of physical devices, vehicles, home appliances, and other items embedded with electronics and software. |
| MFA | Multi-Factor Authentication | A security process that requires more than one method of authentication to verify a user’s identity. |
| MitM | Man-in-the-Middle | An attack where the attacker secretly intercepts and relays communication between two parties. |
| NIST | National Institute of Standards and Technology | A U.S. agency that develops cybersecurity standards and guidelines. |
| OT | Operational Technology | Hardware and software that detects or causes a change through the direct monitoring and/or control of physical devices. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your online identity. |
10. Final thoughts
The world of cybersecurity can seem daunting. Threats are constantly evolving, and the headlines are often filled with news of the latest breach. However, my goal with this guide was not to scare you, but to empower you. Understanding the ‘what’ and ‘how’ of cyber attacks is the first and most critical step toward building an effective defense.
By breaking down threats into simple pillars and providing actionable, personalized advice, I hope I’ve made this complex topic more accessible. Remember these key takeaways:
- Cybersecurity is a human challenge. Many attacks, like phishing, target people, not just technology. Awareness is a powerful tool.
- Proactive defense is crucial. Waiting for an attack to happen is a losing strategy. Fundamentals like backups, software updates, and MFA are your best protection.
- Your defense should be layered. No single tool is a silver bullet. A combination of technology, processes, and user education creates a resilient security posture.
- Knowledge is power. You don’t have to be a cybersecurity expert to be secure. By understanding the primary risks you face, you can focus your efforts where they matter most.
Protecting your digital life is an ongoing journey, not a destination. Stay curious, stay vigilant, and continue to educate yourself. For more in-depth guides, explore our Online Security and Software Tutorials categories on Afdevinfo.com.


