Is your computer acting strange? My guide on how to know if your computer has a virus is your calm, step-by-step plan to find out for sure. The fear is real, but rushing to conclusions can cause more stress than necessary. Over my decade of experience in cybersecurity, I’ve seen countless users panic, thinking a simple performance issue is a catastrophic infection. This guide is designed to give you clarity. It will help you confirm an infection, distinguish it from other common PC problems, and know exactly what to do next.
We’ll go beyond generic lists to provide a diagnostic tool that helps you determine if it’s truly a virus or another common computer problem.
1. How to know if your computer has a virus?
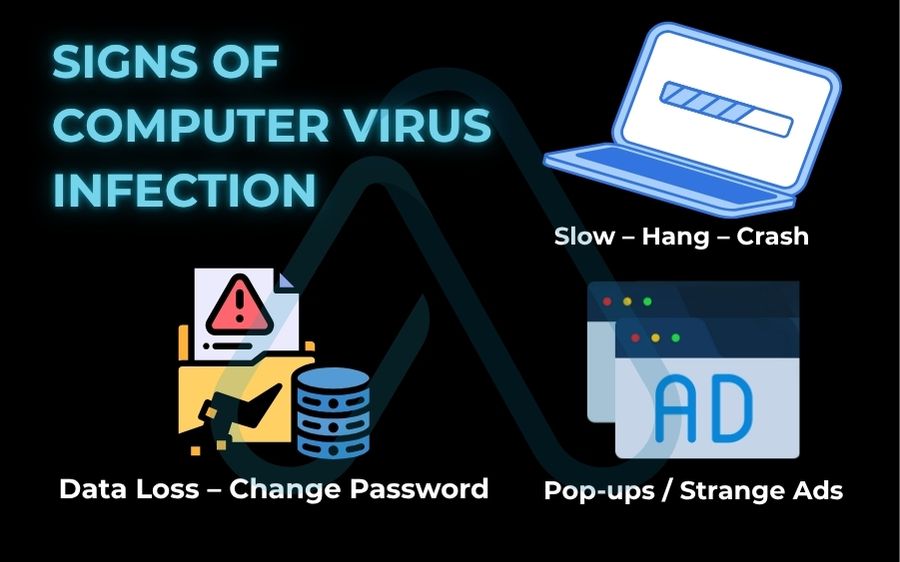
Before we dive into technical checks, let’s cover the most common computer virus warning signs. If your device is exhibiting several of these symptoms, the likelihood of an infection is much higher. I’ve grouped them into categories to make them easier to identify.
1.1. Sudden performance degradation
One of the most frequent signs of a computer infection is a sudden and unexplained drop in performance. A virus is like an uninvited guest hogging all the food (your system resources) at a party, leaving little for your actual programs. Here’s what to look for:
- Frequent crashes or the infamous Blue Screen of Death (BSOD).
- Programs are taking much longer than usual to open or are becoming unresponsive.
- Your computer’s fan is constantly running at high speed, even when the machine is idle.
1.2. Unwanted pop-ups, toolbars, and advertisements
This is the classic sign of adware or a browser hijacker. While many websites have legitimate pop-up ads, malicious ones behave differently. They might appear when your browser is minimized or even closed entirely, which is a very strong indicator of infection. You might also notice new, unfamiliar toolbars in your browser or find that your default search engine has been changed without your permission.
| Warning Never click on links or call phone numbers from unexpected security pop-ups claiming your computer is infected. They are almost always scams designed to trick you into paying for useless services or installing more malware. |
1.3. Suspicious security changes and data anomalies
These are not just inconveniences; they are red alerts indicating a direct attack on your computer’s defenses. These malware symptoms are particularly dangerous because they aim to leave you vulnerable. Be on high alert if you notice any of the following:
- Your antivirus or firewall software has been disabled, and you can’t turn it back on.
- You receive notifications that your passwords have been changed for online accounts you didn’t update.
- Files on your computer have mysteriously disappeared, been moved, or have been encrypted with strange file extensions.
2. Virus or something else? Your diagnostic decision tool
Here’s a truth I’ve learned from years of troubleshooting: not every slow computer is an infected computer. So, how do I know if my computer is infected or just slow? To help you answer this, I’ve created a diagnostic framework. Think of it as a decision-making tool to help you pinpoint the real culprit before you jump to the virus removal stage. While a visual flowchart would illustrate this best, you can follow the logic here to perform your own self-help diagnostic check.
2.1. When ‘slow’ doesn’t mean ‘infected’
Many common issues can mimic the performance drag of a virus. Before assuming the worst, check for these non-malware causes. Here is a table of common symptoms and their potential non-viral causes:
| Symptom | Common Non-Virus Cause |
|---|---|
| Slow boot time | Too many applications are set to launch at startup. |
| General slowness | Your hard drive is nearly full, leaving no room for temporary files. |
| Programs are crashing | An outdated driver is causing a conflict with a recent software update. |
| The Internet is slow | Your Wi-Fi signal is weak, or there are issues with your internet service provider. |
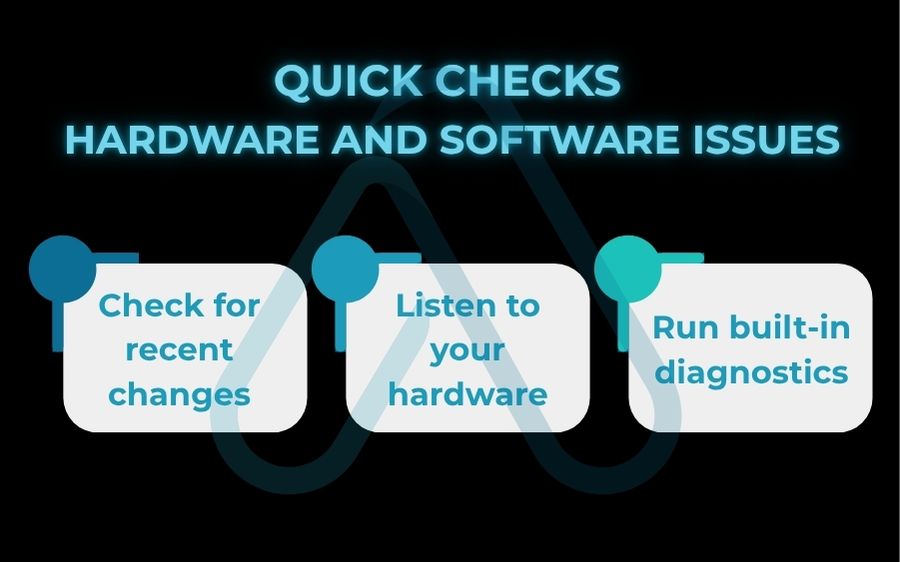
2.2. Ruling out hardware and software issues
Sometimes the problem is physical or related to a recent change you made. I always empower users to be detectives for their own machines before calling in the cavalry. Here are some quick checks you can perform without special software:
- Check for recent changes: Did the problem start right after you installed a new program or updated your operating system? It could be a software conflict.
- Listen to your hardware: Do you hear any unusual clicking or grinding noises from your computer case? This can be a sign of a failing hard drive.
- Run built-in diagnostics: Windows has tools like Windows Memory Diagnostic that can check for RAM issues. A quick search for your model can show you how to run these.
3. How to check for viruses on your device (Windows, Mac, & mobile)
If you’ve ruled out other issues, it’s time to actively check for malware. My strongest recommendation is always to start by running a full, deep scan with a reputable antivirus program. Manual checks are useful for finding clues, but a dedicated scanner is the most reliable tool. For easy navigation, you can jump to your system: Windows | macOS | Mobile.
3.1. For Windows users: How to check for viruses with Microsoft Defender and beyond
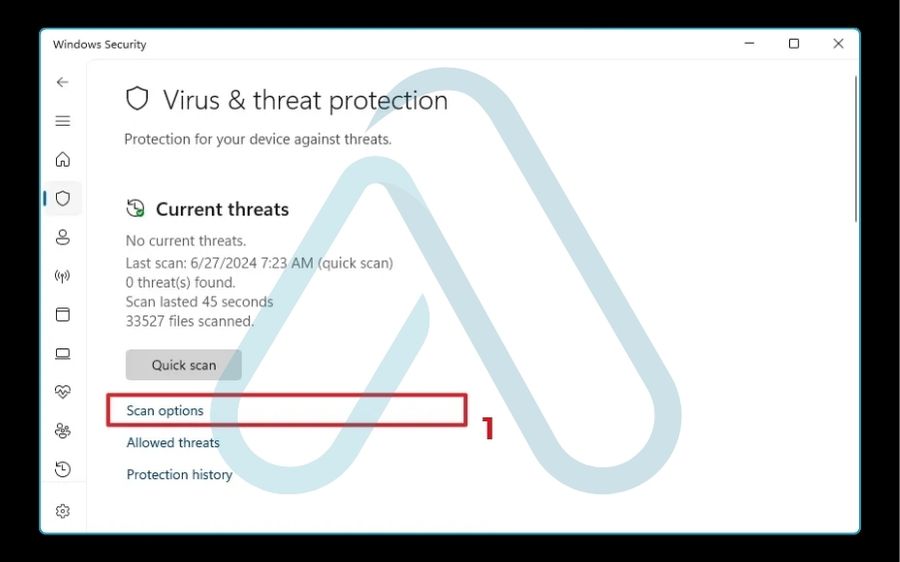
For most Windows 10 and 11 users, the built-in Microsoft Defender is a powerful first line of defense. Here is how I recommend running a comprehensive scan:
- Open your Settings app, then go to Privacy & security > Windows Security.
- Click on Virus & threat protection.
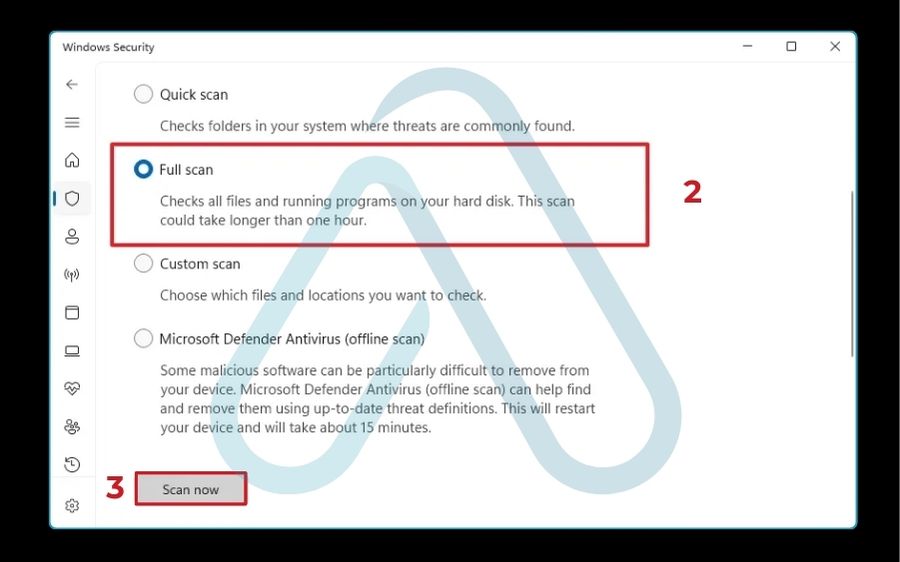
- Under ‘Current threats,’ click on Scan options.
- Select Full scan and then click Scan now. This will take some time, but it’s the most thorough option.
Beyond a scan, you can also open the Task Manager (Ctrl+Shift+Esc) and look at the ‘Processes’ tab. If you see processes with strange names consuming a high amount of CPU or disk resources, a quick web search on the name can often reveal if it’s malicious.
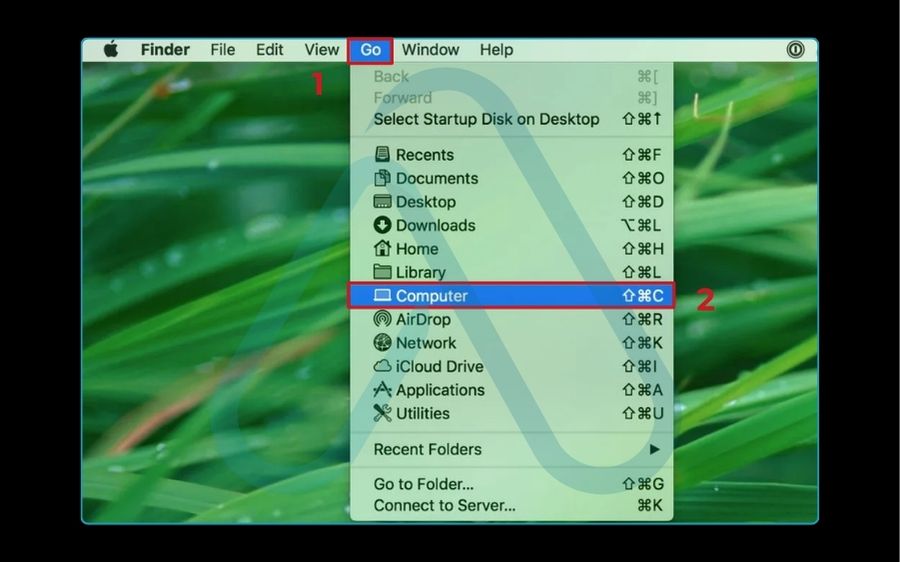
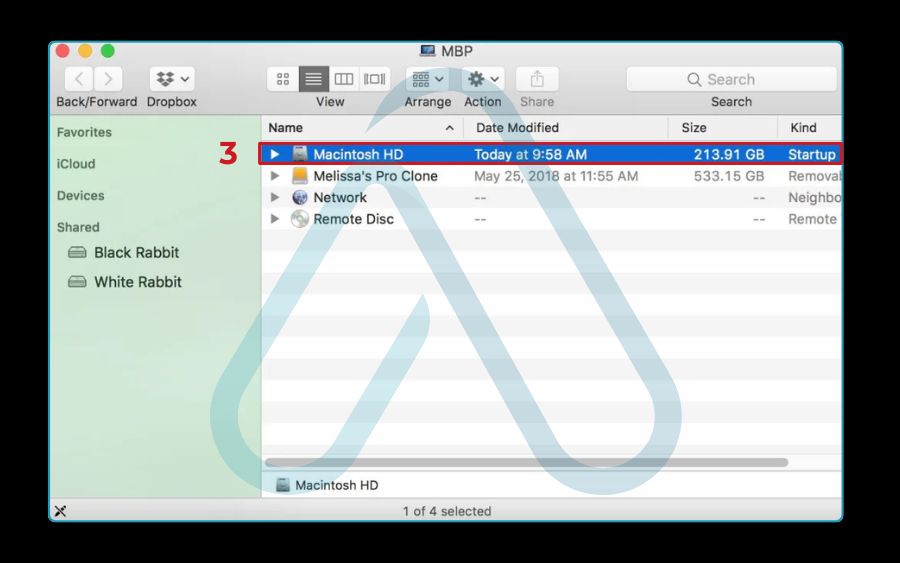
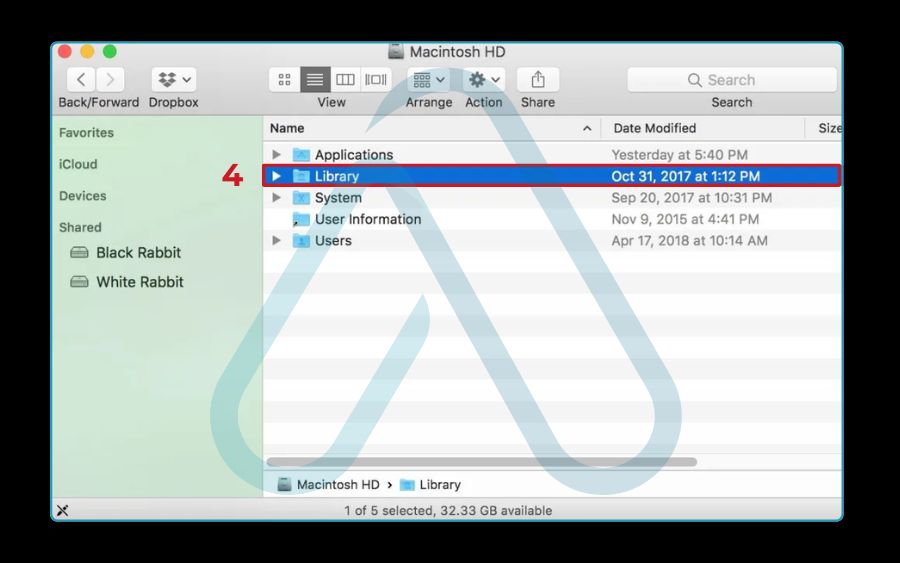
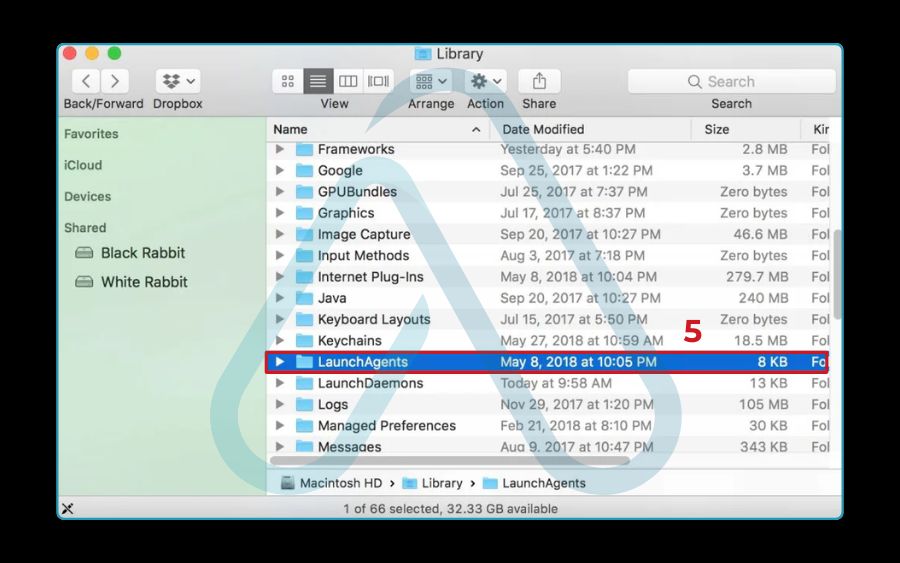
3.2. For Mac users: Checking Activity Monitor and launch agents
It’s a persistent myth that Macs can’t get malware. While macOS is secure, it is not immune. If you suspect an issue, I advise starting with Apple’s built-in tools. Here is my checklist for a manual Mac inspection:
- Check Activity Monitor: Open Activity Monitor (from Applications > Utilities) and look for any applications or processes using an unexpectedly high amount of CPU power.
- Review your Applications: Look in your Applications folder for any software you don’t remember installing.
- Inspect Login Items: In System Settings, go to General > Login Items. Check the ‘Allow in the Background’ section for any unfamiliar items that could be malware agents.
- Check Browser Extensions: Open your web browser(s) and remove any extensions you didn’t intentionally install.
3.3. For mobile users: Android and iOS symptoms
Your phone is a computer, too, and it can get infected. The signs are often different, focusing on resource drain and data usage. Look for a sudden, drastic drop in battery life, unusually high mobile data consumption, or apps you don’t recognize. On Android, be especially wary of apps installed from outside the official Google Play Store. On iOS, while traditional viruses are rare, phishing attacks and malicious calendar subscriptions are common threats.
| My most important advice for mobile security is this Only download applications from official app stores like the Apple App Store and Google Play Store. This single practice eliminates the vast majority of mobile malware threats. |
4. The silent threats: Advanced virus behaviors you might miss
What I find truly unnerving are the threats that don’t announce themselves with pop-ups or slowdowns. Some of the most dangerous malware is designed to be invisible. As a user, it’s important to understand the difference between a virus and malware. Malware is the broad term for any malicious software; a virus is just one type. These advanced malware threats are what even savvy users can miss.
Here are a few of the stealthy types I’ve encountered:
- Keyloggers: Software that secretly records every keystroke you make, capturing passwords, credit card numbers, and private messages.
- Cryptojacking: Malware that uses your computer’s processing power to mine for cryptocurrency in the background, slowing your machine down and increasing your electricity bill.
- Rootkits: A deeply embedded type of malware that gives an attacker administrative-level control over your computer while actively hiding its own presence from you and your security software.
4.1. Your computer is sending emails you didn’t write
If friends or colleagues tell you they’re receiving spam emails from your address, take it seriously. A common tactic for malware is to take over your email client or webmail session to spread itself to your contacts. The first thing you should do is check your ‘Sent’ folder for any messages you don’t recognize. This can cause significant reputational damage and is a sign that your account credentials have been compromised.
If you see this, change your email password from a separate, clean device right away.
4.2. Your internet connection seems unusually slow or active
Does your internet seem sluggish even when you’re not doing much? Or do you see the network activity light on your router blinking frantically when your computers are supposedly idle? This could be a sign that your machine has been co-opted into a botnet. In simple terms, your computer has become a ‘zombie’ used by an attacker to send spam, attack websites, or perform other illegal activities, all using your bandwidth. Telltale signs include:
- A noticeable drop in internet speed that isn’t related to your provider.
- Friends report being unable to access your shared files because of network traffic.
- Your security software reports that your computer is trying to connect to known malicious servers.
5. Confirmed: Your immediate action plan if you have a virus
If you’ve confirmed an infection, the key is not to panic. Follow a clear, methodical process to contain the damage and remove the threat. This is the immediate action plan I give to all my clients. Following these steps in order will help you regain control and is the first step to removing the computer virus.
Step 1:
Disconnect from the internet
This is your absolute first step. A virus can use your internet connection to send your private data to an attacker or spread itself to other devices on your network. Disconnecting cuts it off. Unplug your Ethernet cable or turn off your Wi-Fi immediately. Do not reconnect until you are confident the threat has been removed.
Step 2:
Boot into safe mode and run a scan
Safe Mode is a diagnostic startup mode that loads only the essential files and drivers Windows needs to run. Many types of malware are programmed not to load in Safe Mode, making them easier to detect and remove. Here are the general steps: Reboot your computer and, depending on your system, you may need to press a key like F8 repeatedly during startup. Once in the startup menu, select ‘Safe Mode with Networking’ (if you need internet for your antivirus updates) or just ‘Safe Mode’. Once there, run a full scan with your antivirus software.
Step 3:
Change your critical passwords
You must assume that any passwords you typed while the computer was infected have been stolen. It is critical that you perform this step on a different, uninfected device like your smartphone or another computer. If you change them on the infected PC, the malware could simply capture the new ones. Here is the priority list I recommend:
- Email accounts first! They are the key to resetting everything else.
- Online banking and financial applications.
- Primary social media and any work-related accounts.
6. Beyond removal: How to document and report the incident
Most guides stop at removal, but I believe the process isn’t over until you’ve documented and, if necessary, reported the incident. This is a step that elevates you from a victim to a proactive user and is especially crucial if you’re dealing with a work computer or a serious data breach.
6.1. Why creating a record is crucial
So, why should you bother documenting what happened? If this is your work laptop, your IT department will need this information to assess the risk to the company network. For a personal device, this record can be invaluable for potential identity theft insurance claims or simply for your own learning to avoid future infections. I suggest creating a simple text file with the following information:
- My Malware Incident Log Template
- Date of Discovery: [Date you first noticed the issue]
- Initial Symptoms: [List the signs, e.g., slow performance, pop-ups]
- Malware Identified: [Name of the virus/malware if your AV provided it]
- Steps Taken: [e.g., Disconnected from the internet, ran a scan in Safe Mode, changed passwords]
6.2. Where and how to report malware
Reporting malware is a helpful civic duty in our digital world. When you report an infection, you provide data that helps antivirus vendors improve their detection tools and helps government agencies track cybercrime trends. This helps protect everyone. Here are a few places I suggest reporting serious infections:
- To your antivirus vendor: Most security software companies have a form on their website to submit new or undetected malware samples.
- To government agencies: In the U.S., you can report incidents to the FTC at ReportFraud.ftc.gov or to CISA (Cybersecurity & Infrastructure Security Agency).
7. Frequently asked questions
Here are my answers to a few common questions I receive about computer infections.
Can a computer have a virus with antivirus installed?
Yes, absolutely. Antivirus software is essential, but it isn’t foolproof. There are a few key reasons why an infection can still happen: the malware might be a brand-new ‘zero-day’ threat that the antivirus doesn’t have a signature for yet, a user might have accidentally overridden a security warning, or the malware itself was sophisticated enough to disable the antivirus software before it could react.
What’s the difference between a virus and malware?
I like to use an analogy: malware is like the general term ‘crime,’ while a virus is a specific type of crime, like ‘robbery.’ Malware is the umbrella term for all types of malicious software, including viruses, worms, trojans, ransomware, and spyware. A computer virus is a specific type of malware that works by attaching itself to a legitimate program and spreading when that program is run.
Will rebooting my computer get rid of a virus?
Almost never. While a simple restart can solve many temporary glitches, most malware is designed with ‘persistence’ in mind. This means it writes itself into critical system files or startup processes to ensure it reloads every single time you turn on your computer. Rebooting is a useful troubleshooting step, but it is not a malware removal method.
Glossary of key terms
| Term | Full Term | Meaning |
|---|---|---|
| Adware | Advertising-supported Software | Software that automatically displays or downloads advertising material when a user is online. |
| Botnet | Robot Network | A network of private computers infected with malicious software and controlled as a group without the owners’ knowledge. |
| BSOD | Blue Screen of Death | An error screen displayed on a Windows computer system following a fatal system error. |
| Cryptojacking | Cryptocurrency Jacking | The unauthorized use of someone else’s computer to mine cryptocurrency. |
| Keylogger | Keystroke Logger | A type of surveillance technology used to monitor and record each keystroke typed on a specific computer’s keyboard. |
| Malware | Malicious Software | An umbrella term used to refer to any software intentionally designed to cause damage to a computer, server, or network. |
| Phishing | – | A cybercrime in which a target is contacted by email, telephone or text message by someone posing as a legitimate institution to lure them into providing sensitive data. |
| Rootkit | – | A collection of computer software, typically malicious, designed to enable access to a computer while masking its existence. |
8. Final thoughts: Staying proactive is your best defense
We started this guide with that sinking feeling of anxiety, but I hope you now feel a sense of control and empowerment. By learning how to recognize the signs, diagnose the problem accurately, act decisively, and even report the incident, you’ve gained crucial skills for staying safe online. The ultimate goal, however, is prevention. A proactive security posture is the best defense against future threats.
Here are the most critical takeaways to remember:
- Trust your instincts: If your computer feels ‘off,’ investigate it. Don’t ignore persistent performance issues or strange behavior.
- Diagnose before you act: Not every problem is a virus. Ruling out common hardware and software issues can save you time and stress.
- Act with a plan: If you confirm an infection, follow a clear plan: disconnect, scan in Safe Mode, and change passwords from a safe device.
- Prevention is paramount: Your best defense is a good offense. Keep your software updated, use strong passwords, be wary of phishing, and always back up your important data.
At Afdevinfo, my mission is to make digital security accessible to everyone. By breaking down complex topics, I aim to give you the practical knowledge you need to protect your digital life. For more in-depth guides, explore our Online Security and Software Tutorials categories.


