Feeling like your digital life is an open book? You’re right to be concerned. When I first started in cybersecurity over a decade ago, the threats were simpler, but now, knowing how can you protect your privacy on the internet is more complex and crucial than ever. Generic lists of tips are outdated. In 2025, you need a personalized, up-to-date roadmap to take back control. This guide is exactly that. We’ll start by building foundational habits, then explore essential tools, understand the new laws working in your favor, and finally, tackle emerging threats from AI and smart devices.
In the last year alone, data breaches exposed over 6 billion records worldwide. Your data is valuable, and it’s time to treat it that way.
In this guide, you’ll discover:
- A quick 60-second privacy self-assessment to find your starting point.
- The five essential habits for immediate online privacy protection.
- How to choose and use the best privacy tools like VPNs, password managers, and encrypted messengers.
- The impact of new privacy laws in 2025 and how to exercise your data rights.
- How to secure your smart home devices and defend against AI or biometric tracking.
- A glossary and practical FAQs to simplify technical terms and common questions.
1. Find your starting point: A 60-second privacy self-assessment
Before diving in, let’s find out where you stand. I’ve designed this quick assessment not to scare you, but to empower you by creating a personalized action plan. Answer these questions honestly to see which sections of this guide will help you the most.
| Question | YES | NO |
| Do you use the same or similar passwords for multiple websites? | Your accounts are at high risk. Your first stop should be section 2.2 on creating unbreakable passwords. | Great job! Proceed to Question 2. |
| Have you reviewed the privacy settings on your social media accounts in the last six months? | You’re on the right track. Proceed to Question 3. | You might be sharing more than you think. Jump to section 2.3 for a social media audit. |
| Do you use a VPN when connecting to public Wi-Fi (like at a café or airport)? | Excellent habit! Proceed to Question 4. | Your connection could be exposed. Learn about the best privacy tools in section 3. |
| Do you own smart home devices like a smart speaker, TV, or security camera? | These can be weak points. Head to section 5.1 for a smart home privacy checklist. | You’re all set. You can start from the beginning or jump to any section that interests you! |
2. The foundational five: Core habits for immediate online privacy protection
Before you spend a dime on software, the most significant gains in online privacy protection come from building the right habits. I always tell people these are the non-negotiable first steps for everyone. They are free, highly effective, and form the bedrock of how you can protect your personal information online.
2.1. How to stop websites from tracking you
Think of web trackers as digital breadcrumbs you leave across the internet, allowing companies to build a detailed profile of your habits and interests. I’ll show you how to erase them. This involves managing browser cookies (small files sites use to remember you) and blocking browser fingerprinting (a technique that identifies you by your unique device settings). Here are some essential browser privacy tips for online tracking prevention.
Here is a list of steps for the most popular browsers:
- Google Chrome: Navigate to Settings > Privacy and security > Third-party cookies. Select ‘Block third-party cookies’. Also, turn on the ‘Send a “Do Not Track” request with your browsing traffic’ option.
- Mozilla Firefox: Firefox’s Enhanced Tracking Protection is excellent and set to ‘Standard’ by default. For maximum protection, go to Settings > Privacy & Security and select the ‘Strict’ mode.
- Apple Safari: Safari has strong built-in privacy features. Ensure ‘Prevent cross-site tracking’ is enabled under Settings > Privacy. It also provides a Privacy Report to show you which trackers it has blocked.
For an extra layer, I personally use privacy-focused extensions like uBlock Origin (to block ads and trackers) and Privacy Badger (which specifically learns to block invisible trackers).

2.2. Creating and managing unbreakable passwords
I’ve seen firsthand how a single weak password can lead to disaster. The reason is simple: if a hacker steals the password from one minor website you use, they will try that same password on your email, banking, and social media accounts. If you reuse passwords, a breach on one site can compromise your entire digital life. That’s why the ‘why’ is so important before the ‘how’.
The single most important rule is: One Unique, Complex Password for Every Single Account.
The only practical way to achieve this is with a password manager. It generates and stores long, random passwords for you. All you have to do is remember one master password. To get started, I recommend looking at Bitwarden or 1Password. Finally, always enable two-factor authentication (2FA) wherever possible. This requires a second code (usually from your phone) to log in, providing a critical safety net even if your password is stolen.

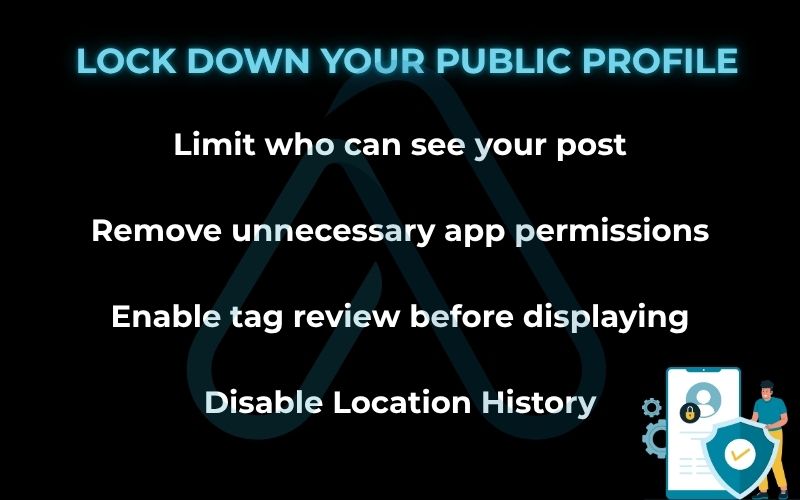
2.3. Locking down your public profile
Your high school reunion photos probably don’t need to be public forever. It’s time for a privacy settings guide for your social accounts. Go through each platform (Facebook, Instagram, LinkedIn, etc.) and ask yourself: who can see my posts, my friends list, and my personal details like my birthday or hometown? In my experience, most people are shocked at how public their profiles are by default.
Here is a social media privacy checklist to follow:
- Review Your Audience: Set your default posting audience to ‘Friends’ instead of ‘Public’. Go back and limit the audience for old posts.
- Prune Third-Party Apps: Check your settings for apps and websites you’ve logged into using your social media account. Revoke access for any you no longer use.
- Limit Tagging: Enable settings that require you to review and approve tags before they appear on your profile.
- Turn Off Location History: Disable precise location sharing in the app settings on your phone and be mindful of geotagging your posts.
3. A comparison of the best privacy tools for 2025
With your foundational habits in place, it’s time to build your personal privacy toolkit. The right software acts as a shield, protecting you from threats your habits alone can’t stop. To help you choose, I’ve analyzed the best privacy tools for 2025, focusing on what matters most: ease of use, cost, and the specific threats they protect you from.
3.1. Finding the right tool for your needs
To make it easier, I’ve created this comparison table of my top picks in three critical categories. This will help you find the right tool for your specific needs.
| Category | Tool | Best For | Key Feature | Ease of Use (1-5) | Cost |
|---|---|---|---|---|---|
| VPN | ProtonVPN | Maximum Security & Privacy | Secure Core servers routed through privacy-friendly countries like Switzerland. | 4 | Free (limited), Paid plans from $4.99/mo |
| Password Manager | Bitwarden | Beginners & Value | Open-source, fully featured, and offers an excellent free tier. | 5 | Free, Premium for $10/year |
| Encrypted Messenger | Signal | Secure Everyday Communication | End-to-end encryption by default for all messages and calls. Minimal data collection. | 5 | Free |
My personal pick for journalists or activists is ProtonVPN due to its strong legal jurisdiction and high-security features. For the average user looking to get started, Bitwarden is, in my opinion, the best combination of security, features, and value on the market.
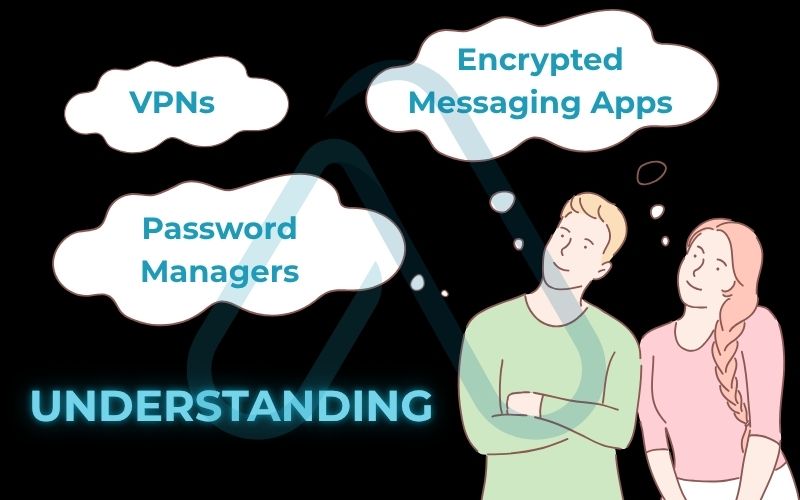
3.2. Understanding VPNs, password managers, and more
Ever wondered what a VPN *actually* does? Let’s break down these tool categories in plain English, so you know exactly what you’re getting.
Virtual Private Networks (VPNs)
A VPN creates a secure, encrypted tunnel for your internet traffic. Think of it like a private subway for your data, shielding it from anyone on the same network, like on public Wi-Fi. It also hides your IP address (your device’s online address) from the websites you visit. However, a VPN doesn’t make you 100% anonymous; the VPN provider can still see your traffic, which is why choosing a trustworthy, no-logs provider like ProtonVPN or Mullvad is critical.
Password Managers
As I mentioned, these are digital vaults for your passwords. They encrypt your login credentials and sync them across your devices. They solve the biggest human weakness in security: the tendency to use weak, reused passwords. They are absolutely essential for online privacy protection.
Encrypted Messaging Apps
Apps like Signal and WhatsApp use end-to-end encryption, which means only you and the person you’re communicating with can read what’s sent. Nobody in between, not even the company that runs the app, can access your messages. For ultimate privacy, I recommend Signal, as it collects virtually no metadata about its users.
4. How new privacy laws affect you in 2025
Good news: new laws give you more power over your data. In 2025, a growing number of US states are joining California and Europe in enacting comprehensive privacy legislation. This isn’t just legal jargon; these laws give you tangible rights. Understanding how do privacy laws affect me in 2025 is key to taking control.
4.1. How to request data deletion
One of the most powerful new rights is the ‘right to deletion,’ sometimes called the ‘right to be forgotten.’ It means you can formally request that a company delete the personal information it has collected about you. While there are exceptions, it’s a powerful tool for cleaning up your digital footprint.
Here are the steps to exercise this right:
- Step 1: Identify the Company. Find the privacy policy on the company’s website. Look for a section on ‘Your Privacy Rights’ or a ‘Privacy Portal’.
- Step 2: Use a Template. If they don’t have a specific form, send an email to their privacy contact (e.g., privacy@company.com).
- Step 3: Track Your Request. Companies are legally required to respond within a specific timeframe (usually 30-45 days).
You can use the simple template below:
Subject: Data Deletion Request Pursuant to [Your State’s Law, e.g., CCPA]
Dear [Company Name],
I am writing to request the deletion of all personal information that you hold about me, in accordance with my rights under [Your State’s Law]. My account information is as follows:
Name: [Your Full Name]
Email Address: [Your Email Address]Please confirm once my data has been deleted. Thank you.
4.2. Opting out of AI profiling and data sales
These new laws also give you the right to opt out of having your data sold or used for targeted advertising and automated profiling. This is a direct response to the rise of AI-driven analytics that can make eerily accurate predictions about your behavior.
Look for a link in the footer of websites that says ‘Do Not Sell or Share My Personal Information.’ This link should take you to a page where you can easily submit your request. Some browser extensions, like the Global Privacy Control (GPC), can even help automate these opt-out requests for you.
5. Privacy on smart devices and emerging tech
Your computer and phone are no longer the only gateways to the internet. From smart speakers that are always listening to wearables that track your health, your digital life has expanded. Securing these devices is a critical step to protect your privacy on the internet and at home.
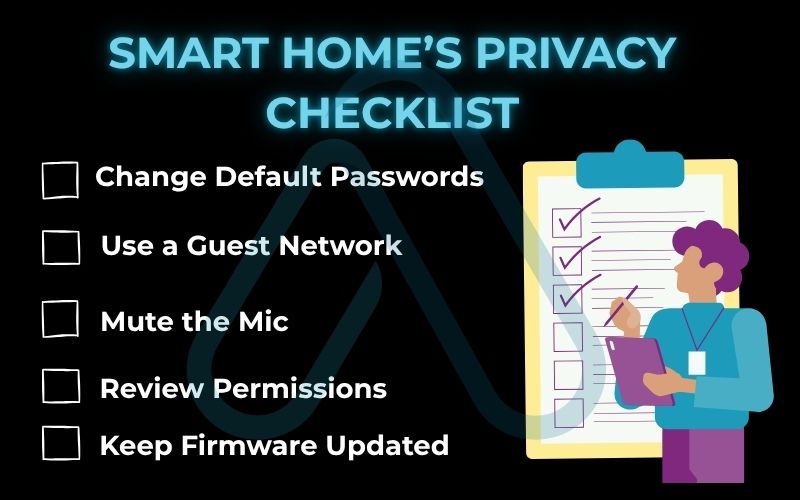
5.1. Your smart home’s privacy checklist
I always advise people to treat every connected device with a healthy dose of skepticism. A single insecure smart camera can give an attacker a foothold into your entire home network. Answering ‘How can I protect my privacy on smartphones and smart devices?’ starts right here.
Here is a checklist I use for securing common IoT devices:
- Change Default Passwords: This is the absolute first thing you should do. The default username and password for your device are often publicly available online.
- Use a Guest Network: Configure your Wi-Fi router to have a separate ‘guest’ network and connect all your smart devices to it. This isolates them from your main devices like your laptop and phone.
- Mute the Mic: Mute the microphone on your smart speakers (like Amazon Echo or Google Home) when you are not actively using them.
- Review Permissions: Just like on your phone, review the data collection policies and permissions for your smart TV and other devices. Do they really need access to your contacts or location?
- Keep Firmware Updated: Enable automatic updates to ensure your devices are protected against the latest known security vulnerabilities.
5.2. Proactive steps against AI and biometric tracking
Looking ahead, the biggest challenges to our privacy will come from AI-driven analytics and the increasing collection of biometric data (like your face, fingerprint, or voice). To future-proof your privacy and prevent identity theft online, you need to be proactive.
| My single most important tip: Treat your biometric data like your most secure password. Do not share it casually. |
Here are some practical, forward-looking steps you can take today:
- Disable Facial Recognition: Go into services like Google Photos and Facebook and turn off facial recognition tagging features.
- Be Wary of ‘Fun’ Quizzes: Many online personality quizzes are just funnels for data collection, gathering personal information that can be used to build a psychological profile of you.
- Check App Permissions: On your smartphone, be extremely cautious about which apps you grant access to your camera, microphone, or biometric hardware (Face ID/fingerprint scanner).
6. FAQs about how can you protect your privacy on the internet
After years of talking about this topic, I’ve found that a few questions come up again and again. Here are my clear, direct answers to the most common ones.
Is it possible to be 100% anonymous online?
No. Complete anonymity is nearly impossible, but you can greatly reduce your digital footprint through smart privacy practices.
Will using a VPN slow down my internet?
Yes, slightly. A VPN reroutes your traffic, but good VPNs keep the speed loss minimal and barely noticeable.
Do I really need a password manager?
Yes. It’s the best way to use strong, unique passwords for every account, protecting you from data breaches.
Glossary of key terms
Here is a breakdown of some technical terms I’ve used in this article.
| Abbreviation | Full Term | Meaning |
|---|---|---|
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your IP address, creating a secure connection, especially on public Wi-Fi. |
| 2FA | Two-Factor Authentication | A security process requiring two different types of information to log in, such as a password and a code from your phone. |
| IoT | Internet of Things | A network of physical devices (like smart speakers, cameras, and TVs) that are connected to the internet to collect and share data. |
| Browser Cookie | N/A | A small file stored on your computer by a website to remember your preferences, login status, and track your activity. |
| Browser Fingerprinting | N/A | A technique used by websites to identify and track you by collecting information about your browser, operating system, and hardware settings. |
7. Final thoughts: Making privacy a sustainable habit
I know this can feel like a lot of information, but protecting your privacy isn’t about doing everything at once. It’s about taking the first step and building sustainable habits over time. This guide is your roadmap, designed to be returned to whenever you need it.
Let’s recap the most critical takeaways from my experience:
- Start with the Foundations: Before anything else, fix your passwords, lock down your browser, and audit your social media. These free steps have the biggest impact.
- Choose Your Tools Wisely: You don’t need every tool, but a good password manager and a reliable VPN are the cornerstones of a modern privacy toolkit.
- Know Your Rights: New laws are on your side. Use your right to delete your data and opt out of being tracked and sold.
- Secure Your Entire Ecosystem: Your privacy is only as strong as your weakest link. Pay close attention to smart home devices and emerging tech.
Protecting your privacy is an ongoing process, not a one-time fix. But by taking these steps, you are no longer a passive user. You are an active, empowered guardian of your own digital life. Ready to start? Go back to the 60-second assessment and take your first step now.
As a trusted guide in the digital world, Afdevinfo is here to help you on your journey to a safer digital life. For more in-depth guides, explore our Online Security & Privacy categories.









