In the time it takes you to read this sentence, thousands of identity threats are launched across the globe. As a cybersecurity expert with over a decade in the field, I understand the growing anxiety around online safety. This is why I’ve created this guide on how to protect identity online, specifically updated for the challenges of 2025, including emerging threats from artificial intelligence. This isn’t just a list of tips; it’s an actionable blueprint for building your digital fortress.
Here is what I will walk you through in this guide:
- Understand 2025’s threats: We’ll look at the sophisticated new tools, like AI phishing, that criminals are using.
- Build your core defenses: I’ll show you the foundational habits that neutralize the vast majority of attacks.
- Choose the right tools: We’ll compare services that can monitor your identity for you.
- Learn recovery steps: If the worst happens, you’ll have a clear, step-by-step plan to regain control.
1. The new battlefield: 2025 threats you need to know
The digital landscape has changed dramatically. The cybersecurity tips that worked five years ago are now just the starting line. Today’s criminals are leveraging sophisticated technology to make their attacks more personal, believable, and harder to detect. Traditional security measures alone are often not enough.
My key takeaway for you is this: Cybercriminals are now using AI, and your defense strategy needs to evolve too.
1.1. AI-powered phishing and voice cloning scams
I’ve seen firsthand how AI has supercharged phishing and smishing (text message phishing) attacks. Gone are the days of poorly written emails with obvious typos. Think of a traditional phishing email as a generic flyer left on every door in a neighborhood.
An AI-powered phishing email is like a bespoke, handwritten letter delivered only to you, referencing your job, recent online purchases, and even the names of your colleagues. These attacks are hyper-realistic because AI can scrape data from your social media and other public sources to create a perfectly tailored trap.
Even more alarming is the rise of voice cloning. A scammer can use a few seconds of your voice from a social media video to create an audio deepfake. They might call a family member, sounding exactly like you, claiming to be in trouble and needing money urgently. The best defense is to be skeptical of unexpected, urgent requests and to verify them through a different communication channel.
To help you spot these advanced scams, here’s a comparison:
| Traditional Phishing Email | AI-Powered Phishing Email |
|---|---|
| Generic greeting like ‘Dear Customer’. | Uses your real name and sometimes your job title. |
| Contains obvious spelling or grammar errors. | Flawless grammar and a professional tone. |
| Makes a vague, urgent request (e.g., ‘Your account is suspended’). | References specific, personal details to build trust (e.g., ‘Following up on your recent order from…’). |
1.2. Synthetic identity fraud: The invisible threat
One of the most insidious threats I’m seeing more of is synthetic identity fraud. I call it the ‘ghost identity’ because it’s so hard to detect. Here’s how it works: a criminal takes a real, valid Social Security number (often belonging to a child or someone who doesn’t use credit) and combines it with completely fake information, like a made-up name and address. They then use this new, synthetic identity to apply for credit cards, open bank accounts, and take out loans.
For you, the individual whose SSN was stolen, the damage can go unnoticed for years until you apply for a loan and discover a ruined credit history tied to a name you don’t recognize. For banks, it’s also a nightmare because there’s no real person to go after the identity is a fabrication. The primary risk is a criminal building a strong credit profile with this ‘ghost’ and then maxing out all the credit lines before disappearing completely.
2. The foundational habits of digital identity protection
Before we explore advanced tools, let’s master the essentials. From my experience, I can tell you that implementing these core habits will neutralize over 90% of the common threats you face daily. Think of these not as tedious chores, but as empowering actions that put you back in control of your digital life. These are some of the most crucial digital privacy best practices you can adopt.
2.1. Create unbreakable passwords with a password manager
The single most effective security upgrade you can make today is adopting a password manager. For years, we were told to create ‘complex’ passwords like `P@ssw0rd1!`. The problem is, these are easy for computers to guess and impossible for humans to remember across hundreds of accounts. The new standard is long, unique passphrases, like `correct-horse-battery-staple`. A password manager creates and stores these for you, so you only have to remember one master password.
Here’s how you can get started in three simple steps:
- Choose a reputable password manager: I recommend well-known services like 1Password, Bitwarden (which has a great free tier), or Dashlane.
- Install it on all your devices: Add the browser extension to your computer and the app to your phone. This ensures your passwords are with you everywhere.
- Start with your most critical accounts: Begin by changing the passwords for your primary email, banking, and social media accounts. Over time, you can update the rest.
2.2. Activate two-factor authentication (2FA) everywhere
When it comes to secure passwords and 2FA, think of them as a team. Your password is the key to your house, but 2FA is the security code you have to enter once you’re inside. It’s a second layer of security that requires you to verify your identity using something you have (like your phone) in addition to something you know (your password).
A common question I get is, ‘Is two-factor authentication enough to stop identity theft?’ The answer is no, it’s not a silver bullet, but it’s a critical layer that stops the vast majority of automated attacks that rely on stolen passwords. Even if a criminal has your password, they can’t get in without that second code. However, not all 2FA methods are created equal.
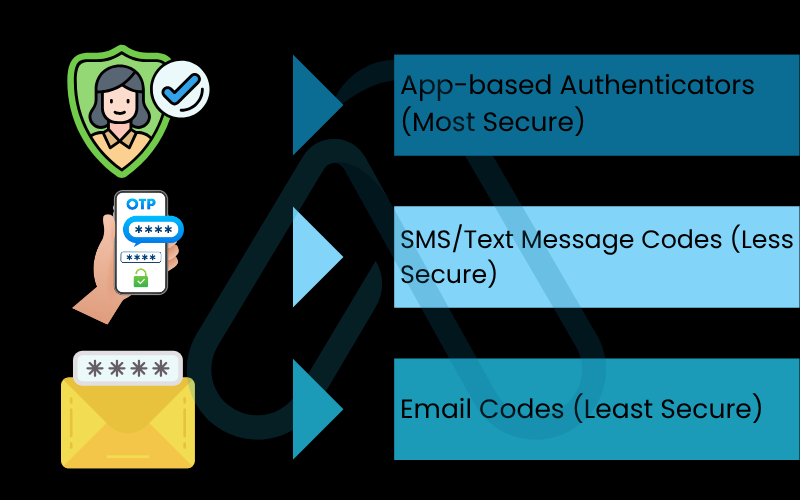
Here is my ranking of 2FA methods, from most to least secure:
- App-based Authenticators (Most Secure): Apps like Google Authenticator or Authy generate time-sensitive codes on your device. This is much safer than SMS because the codes aren’t transmitted over the cellular network.
- SMS/Text Message Codes (Less Secure): Receiving a code via text is better than nothing, but it’s vulnerable to SIM-swapping attacks, where a scammer tricks your mobile carrier into porting your number to their phone.
- Email Codes (Least Secure): If a hacker has already compromised your email, using it for 2FA is like locking your front door and leaving the key under the mat. Avoid this method whenever possible.
2.3. Practice smart social media and data sharing
Every piece of information you share online contributes to your ‘digital footprint.’ Cybercriminals use this footprint as an arsenal. That fun quiz revealing your first pet’s name or your mother’s maiden name? Those are the answers to common security questions. Your public birthday posts? That’s another piece of your identity puzzle. The data you share publicly is exactly what powers the hyper-personalized AI phishing attacks I mentioned earlier.
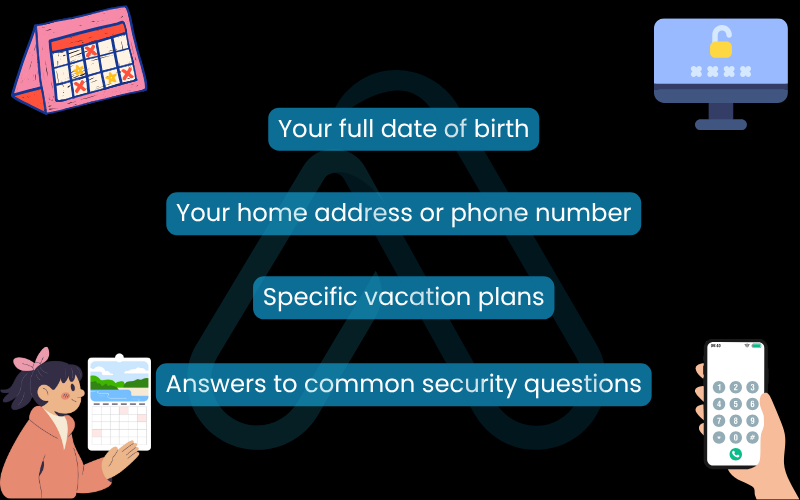
As part of your digital privacy best practices, I strongly advise you to conduct a privacy check-up on your social media accounts and never share certain information publicly. Here is a list of what to keep private:
- Your full date of birth: Year, month, and day are a trifecta for identity thieves.
- Your home address or phone number: This should never be public.
- Specific vacation plans: Announcing you’ll be away from home is an open invitation to both digital and physical theft.
- Answers to common security questions: Things like your first pet’s name, your mother’s maiden name, or the street you grew up on.
3. How to know if your identity has been stolen
Spotting a problem early is the key to minimizing damage. Many people ask me, ‘How can you tell if your identity has been stolen?’ The warning signs aren’t always obvious, but they often fall into a few key categories. If you notice any of the following, it’s time to act immediately. Here’s what to look for.
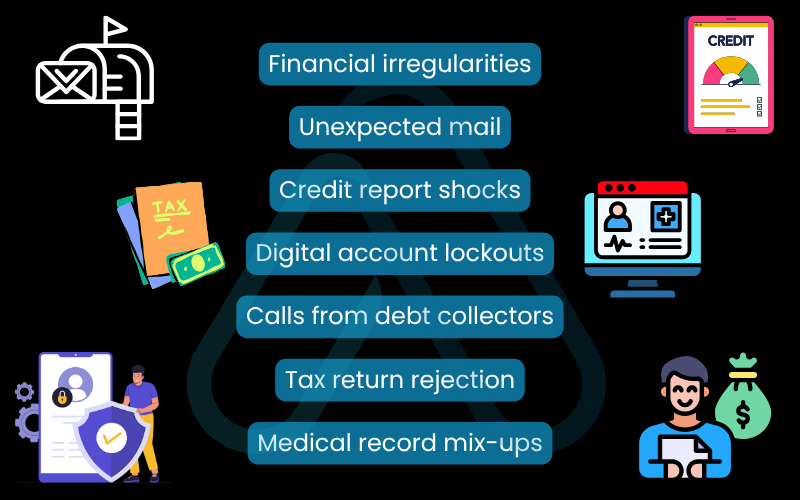
I recommend reviewing this self-diagnostic checklist periodically:
- Financial irregularities: You see unfamiliar charges on your credit card statements or withdrawals from your bank account you don’t recognize.
- Unexpected mail: You receive bills or collection notices for accounts you never opened, or you get credit cards you didn’t apply for.
- Credit report shocks: You are denied for a loan or credit card due to a poor credit score you weren’t aware of, or you find new accounts on your credit report.
- Digital account lockouts: You can no longer log in to your email or social media accounts, or you notice posts and messages that you didn’t send.
- Calls from debt collectors: You start getting calls about debts that are not yours.
- Tax return rejection: The IRS rejects your tax return because a return has already been filed using your Social Security number.
- Medical record mix-ups: You receive a bill for medical services you didn’t receive, or your health plan rejects a legitimate claim because records show you’ve reached your benefits limit.
4. A guide to identity protection tools
While good habits are your first line of defense, specialized identity protection tools can act as a 24/7 security guard for your personal information. These services are designed to monitor vast sources of data and alert you to suspicious activity, helping you prevent identity theft before it spirals out of control. I often get asked what these tools actually do. In short, they typically offer a suite of services like dark web monitoring, which scans criminal marketplaces for your credentials; credit monitoring, which alerts you to changes in your credit files; and data breach alerts that notify you if your information has been exposed in a known breach.
Comparison of top identity protection services
Navigating the market for identity protection tools can be confusing. To simplify it, I’ve compared a few of the leading options to help you decide what’s right for your needs and budget. This table provides a side-by-side look at their features.
| Service | Key Features | Pricing Tier | Best For |
|---|---|---|---|
| Aura | All-in-one protection: credit monitoring (3 bureaus), dark web scanning, antivirus, VPN, and a password manager. | Paid (Individual & Family plans) | All-in-one simplicity and families. |
| IdentityForce | Strong focus on recovery, with fully managed restoration services. Includes credit monitoring, social media monitoring, and PC protection tools. | Paid (Multiple tiers) | Users who prioritize recovery assistance. |
| LifeLock with Norton 360 | Combines identity theft protection with Norton’s well-known cybersecurity suite (antivirus, VPN). Includes extensive alerts. | Paid (Various tiers) | Users wanting to bundle identity protection with device security. |
| Free Alternatives | Use free credit monitoring from services like Credit Karma, set up transaction alerts with your bank, and check your email on HaveIBeenPwned.com. | Free | Budget-conscious users willing to manage multiple services. |
5. Tailored guidance for you and your family
Online identity protection isn’t one-size-fits-all. Your risks change based on your age, family, and career. As an expert, I believe in providing advice that acknowledges these differences. Here’s my tailored plan for some of the key groups I often advise.
5.1. Protecting your children’s ‘clean slate’ identity for parents
The Risk: A child’s Social Security number is a blank slate, making it a prime target for synthetic identity fraud. Thieves can use it for years to build a fraudulent credit history without anyone noticing until your child applies for a student loan or their first credit card.
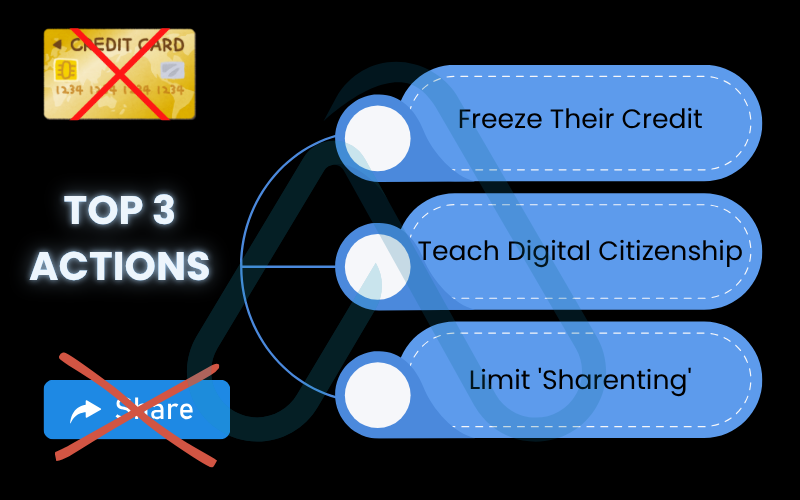
My Top 3 Actions:
- Freeze Their Credit: This is the single most important step. A credit freeze restricts access to their credit file, making it much harder for thieves to open new accounts.
- Teach Digital Citizenship: Educate your children about the dangers of oversharing personal information online and the importance of strong, private passwords.
- Limit ‘Sharenting’: Be mindful of how much information you share about your children online. Details like their full name, birthdate, and school can be pieced together by criminals.
Consider placing a security freeze on your child’s credit files with all three major bureaus (Equifax, Experian, and TransUnion). It’s free and is the most powerful tool you have.
5.2. Navigating digital risks with confidence
My Top 3 Actions:
- Follow Simple Rules: Create and follow a few non-negotiable rules to avoid common traps. I have a list below to get you started.
- Be Skeptical of Urgency: Scammers create a false sense of urgency to make you act without thinking. Any legitimate organization will not pressure you into an immediate decision or payment.
- Involve a Trusted Advisor: For any significant financial decision or unexpected request for money or information, consult a trusted family member or financial advisor first.
Here are my simple rules to post near your computer or phone:
- Never give remote access to your computer to someone who called you out of the blue.
- Hang up on robocalls and suspicious callers immediately. Do not press any buttons.
- Government agencies will never call you to demand immediate payment via gift card or wire transfer.
| The Risk: Seniors are often targeted by specific, high-pressure scams, including tech support scams (where a fake agent requests remote access to ‘fix’ a non-existent virus), government impersonation scams (fake calls from the IRS or Social Security), and romance scams. |
5.3. Separating personal and professional risk for freelancers and business owners
My Top 3 Actions:
- Separate Your Networks: Use a VPN (Virtual Private Network) for all work activities to encrypt your connection, especially on public Wi-Fi. If possible, have a separate Wi-Fi network for your business devices.
- Secure Your Data: Use separate devices and accounts for business and personal use. Encrypt sensitive client files and use secure methods for payment processing.
- Back Up Everything: Regularly back up your important business and personal data to a separate, secure location. This protects you against data loss from ransomware or hardware failure.
| The Risk: When you work for yourself, the line between your personal and professional digital life can blur. Using personal devices for work and managing client data creates unique vulnerabilities. A breach can damage not just your personal finances but also your professional reputation and your clients’ trust. |
6. What to do if your identity is compromised
If the worst happens, don’t panic. I know it’s a stressful and frightening experience, but taking immediate, methodical action can significantly limit the damage. Take a deep breath and follow these steps in my recovery playbook immediately. This is your guide on what should you do if your online identity is compromised.
6.1. Step 1: Contain the damage (The first hour)
Your immediate goal is to lock the criminals out of your accounts and stop them from doing more harm. This is what you need to do right away.
Your top priority is to change the password for your primary email account. This is the master key to all your other accounts.
- Change Critical Passwords: After securing your email, change the passwords for your online banking, financial accounts, and any other sensitive accounts.
- Place a Fraud Alert or Credit Freeze: Contact one of the three major credit bureaus (Equifax, Experian, or TransUnion) to place a one-year fraud alert on your file. That bureau is required to notify the other two. For even stronger protection, I recommend placing a credit freeze with all three bureaus, which you must do individually. A freeze prevents anyone from opening new credit in your name.
6.2. Step 2: Report and document (The first 24 hours)
Creating an official paper trail is critical for disputing fraudulent charges and proving you were a victim. You need to report the theft to the proper authorities.
Here’s who to contact:
- The Federal Trade Commission (FTC): Go to IdentityTheft.gov and file a report. This is a crucial step. The FTC will give you a personalized recovery plan and an official report that serves as proof of the crime.
- Local Police Department: File a report with your local police. Bring a copy of your FTC report, a photo ID, and any proof you have of the theft. Get a copy of the police report.
Keep a detailed log of every phone call, email, and letter. Note the date, the person you spoke with, and what was discussed. This documentation is your best friend during the recovery process.
6.3. Step 3: Monitor and prevent a recurrence
After you’ve contained and reported the theft, you need to stay vigilant to prevent identity theft from happening again. This is an ongoing process of rebuilding your security.
Here is a final checklist for long-term protection:
- Regularly review your credit reports from all three bureaus.
- Set up transaction and login alerts on your bank and credit card accounts.
- Consider signing up for one of the identity protection services I mentioned earlier for continuous monitoring.
- Continue to use a password manager and enable 2FA on all your accounts.
7. FAQs about how to protect identity online
As an expert in this field, I get a lot of questions about online identity protection. Here are my direct answers to some of the most common ones.
What are the best ways to protect your identity online?
Use a password manager, enable 2FA, limit personal info sharing, monitor accounts regularly, and consider a credit freeze.
Is two-factor authentication enough to stop identity theft?
No. It prevents account takeovers but can’t stop phishing or synthetic identity fraud.
Are there free tools for identity protection?
Yes. Use Bitwarden for passwords, Credit Karma for credit monitoring, bank alerts, and HaveIBeenPwned to check data breaches.
What is the first thing you should do if your identity is stolen?
What is the first thing you should do if your identity is stolen?
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| AI | Artificial Intelligence | The simulation of human intelligence in machines, used by scammers to create highly personalized and realistic fraudulent messages. |
| Phishing | N/A | A fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity in an electronic communication. |
| Smishing | SMS Phishing | A phishing attack conducted over text messages (SMS). |
| Deepfake | N/A | Synthetic media (video or audio) in which a person’s likeness is replaced with someone else’s, often used in scams. |
| 2FA | Two-Factor Authentication | A security process where users provide two different authentication factors to verify themselves, such as a password and a code from their phone. |
| SSN | Social Security Number | A nine-digit number issued to U.S. citizens and residents, a key piece of information targeted by identity thieves. |
| Dark Web | N/A | A part of the internet that isn’t indexed by search engines and requires special software to access. It’s often used for illegal activities, including selling stolen personal information. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your online identity, providing a secure connection, especially on public Wi-Fi. |
| FTC | Federal Trade Commission | A U.S. government agency that protects consumers; its website, IdentityTheft.gov, is the primary resource for reporting and recovering from identity theft. |
8. Final thoughts: Taking control of your digital life
After more than a decade in this field, I’ve learned that protecting your identity is an ongoing practice, not a one-time fix. The threats we face online will continue to evolve, but so will our knowledge and the tools we have to combat them. The steps I’ve outlined in this guide are not about creating fear, but about building confidence. By understanding the risks and taking proactive, manageable steps, you can build a formidable defense around your digital life.
Here are the most critical takeaways from our guide:
- Master the Fundamentals: A strong, unique password for every account (managed by a password manager) and two-factor authentication are your most powerful defenses.
- Be Aware of New Threats: Recognize that AI is making scams more sophisticated. Be skeptical of urgent requests, even if they seem personal.
- Monitor and Protect: Regularly check your financial statements and consider a credit freeze to lock down your most valuable asset.
- Have a Plan: Know the immediate steps to take if your identity is compromised. A quick response can make all the difference.
Your digital security is in your hands start building your fortress today. Take five minutes right now to implement just one new habit, whether it’s downloading a password manager or enabling 2FA on your email account. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.









