If you’re asking yourself what are some practices to prevent hacking, you’re already taking the most important step toward a safer digital life. That small moment of panic when you see a strange login alert. I’ve been there, and after more than a decade in cybersecurity, I can tell you that in 2025, the question isn’t if you’ll be targeted, but how prepared you are. This guide is designed to be your blueprint for secure living. We’ll build foundational habits, secure every device you own, understand new threats on the horizon, and even create a recovery plan, just in case.
This isn’t just a list of tips; it’s a complete blueprint for digital safety.
1. Your interactive cybersecurity self-assessment
Before we build, we need to know where we’re starting. This checklist isn’t a test; it’s a no-judgment tool to help you see your current security posture at a glance. Let’s find your starting point. Check off each practice you currently follow.
- I use a unique, complex password for my primary email account.
- I use a password manager to store my credentials.
- I have multi-factor authentication (MFA) enabled on my critical accounts (email, banking, social media).
- My computer’s operating system is set to install updates automatically.
- My smartphone’s operating system and apps are regularly updated.
- I know how to check the sender’s full email address before clicking a link.
- I am skeptical of unexpected attachments or requests for personal information, even if they seem to come from someone I know.
2. Some of the best practices to prevent hacking
Mastering the fundamentals is the key to preventing the vast majority of common attacks I see every day. These three habits are the bedrock of your Secure Living Blueprint.
2.1. Master your access with passwords and multi-factor authentication (MFA)
Your first line of defense is always how you control access. I can’t stress enough that using simple or reused passwords is like leaving your front door wide open. Every single online account should have a unique, complex password (a mix of upper/lowercase letters, numbers, and symbols). The best way to manage this is with a password manager.
Think of it as a highly secure digital vault; you only need to remember one strong master password, and it handles the rest, creating and storing uncrackable passwords for you. But passwords alone aren’t enough. Multi-factor authentication, or MFA, is your single most powerful defense. It’s like needing both a key (your password) and a unique PIN code (sent to your phone) to open a safe. Even if a hacker steals your password, they can’t get in without that second factor, providing essential identity theft protection.
If you do only one thing from this guide, enable multi-factor authentication on your critical accounts.
2.2. The shield of now: the critical role of software updates
I often hear people say they delay updates because they’re inconvenient. This is a critical mistake. An unpatched piece of software is like a broken window in your house that you know about but haven’t fixed. It’s an open invitation for hackers. Updates don’t just add new features; their primary purpose is often to patch security vulnerabilities that have been discovered. Enabling automatic updates is one of the easiest and most effective security measures you can take. To ensure you’re covered, here’s where you should check for updates:
- Your OS: This includes Windows, macOS, Android, and iOS. These are the most critical updates to install promptly.
- Your Web Browser: Chrome, Firefox, Safari, and Edge are your gateways to the internet and are frequent targets.
- Your Apps: Any application you have installed, from your office suite to your messaging apps, can have vulnerabilities.
2.3. The human firewall: defending against phishing and social engineering
Technology can only do so much; you are the final checkpoint. Hackers know this, which is why phishing and social engineering attacks are more sophisticated than ever. They go beyond a simple fake link and prey on human psychology. I’ve seen them use tactics designed to make you act before you think, such as creating a false sense of urgency (‘Your account will be suspended in 1 hour!’) or impersonating a trusted authority (a fake email from your bank, boss, or even a government agency).
Effective phishing prevention means learning to spot these red flags. Here is a simple comparison of a phishing attempt versus a legitimate email:
| Red Flag | Phishing Email Example | Legitimate Email Example |
|---|---|---|
| Sender Address | `support@yourbank-secure.com` (Looks close, but isn’t the real domain) | `support@yourbank.com` (The official domain) |
| Greeting | `Dear Valued Customer,` (Generic and impersonal) | `Dear John Smith,` (Uses your actual name) |
| Urgency & Threats | `Click here IMMEDIATELY to verify your account or it will be locked.` | `You can review your recent statement by logging into your account.` |
| Links | Hovering reveals a strange URL: `http://bit.ly/xyz123` | Hovering reveals the official URL: `https://yourbank.com/login` |
3. Securing your digital spaces from your pocket to your living room
Your security blueprint must extend beyond your computer to cover every connected device you own. The core habits we just established, strong access control, timely updates, and personal awareness—apply everywhere.
3.1. How can I protect my phone from hackers?
Our phones are arguably our most personal devices, holding everything from private messages to financial data, making them a prime target for hackers. Mobile threats include malicious apps from unofficial stores, the risks of unsecured public Wi-Fi, and SMiShing (phishing via SMS). The first step is basic malware protection: only download apps from official sources like the Google Play Store or Apple App Store and read the reviews. Beyond that, configuring your device’s built-in security is crucial. Below are some key settings for both iOS and Android:
| Security Setting | iOS (iPhone) | Android |
|---|---|---|
| App Permissions | Go to `Settings` > `Privacy & Security` to review which apps can access your camera, mic, location, etc. | Go to `Settings` > `Apps` > select an app > `Permissions` to control its access. |
| Find My Device | Enable `Find My iPhone` in `Settings` > `[Your Name]` > `Find My`. | Enable `Find My Device` in `Settings` > `Security` or `Google`. |
| Screen Lock | Use Face ID, Touch ID, or a strong passcode via `Settings` > `Face ID & Passcode`. | Use a PIN, pattern, or biometrics via `Settings` > `Security & privacy`. |
3.2. Home Wi-Fi security essentials
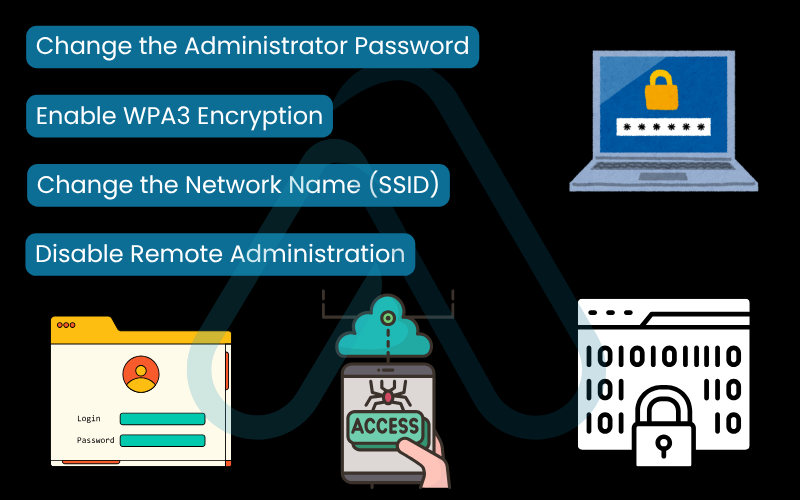
Your home router is the main gateway to the internet for all your devices, yet most people use the default settings it came with. This is a huge risk. Securing your network is easier than you think and provides a powerful layer of data encryption for your entire home. I recommend following these network security tips right away. You can typically access your router’s settings by typing its IP address (often found on a sticker on the router itself, e.g., 192.168.1.1) into a web browser. Follow this simple guide:
- Change the Administrator Password: This is not your Wi-Fi password. It’s the password to log into the router’s settings. The default is usually `admin` or `password`, which every hacker knows. Change it to something unique and strong.
- Enable WPA3 Encryption: In the wireless security settings, choose WPA3 if available. If not, WPA2 is the next best option. This encrypts the traffic between your devices and the router.
- Change the Network Name (SSID): Change the default network name (e.g., ‘Linksys12345’) to something that doesn’t identify your router brand or you personally.
- Disable Remote Administration: Ensure that the router’s settings can only be accessed from a device physically connected to your local network.
3.3. Securing your smart home and IoT devices
One of the biggest gaps in personal cybersecurity I see today is the Internet of Things (IoT). Your smart speakers, cameras, TVs, and even smart refrigerators are all computers connected to the internet. A hacked smart camera is a terrifying invasion of privacy. Because these devices are often ‘set it and forget it’, their security is neglected. When you bring any new smart device into your home, I urge you to follow this simple checklist to protect yourself.
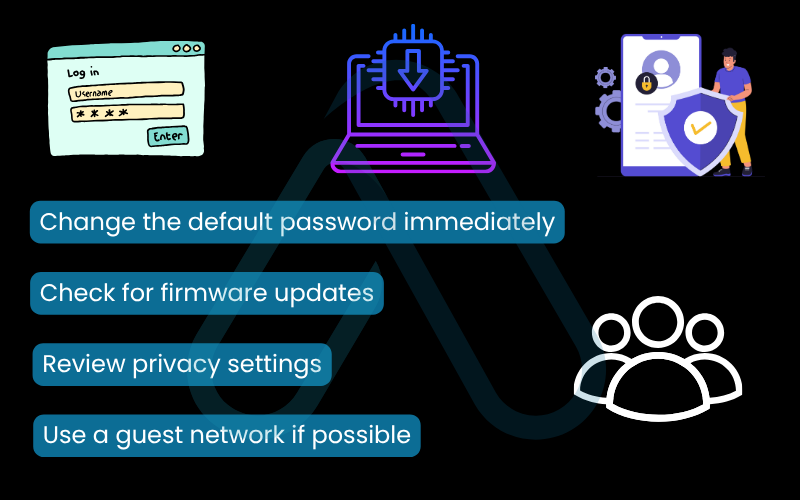
New Smart Device Setup Checklist:
- Change the default password immediately. This is the single most important step. Default credentials for thousands of devices are available online.
- Check for firmware updates. As soon as you connect the device, go into its settings and install any available updates.
- Review privacy settings. Understand what data the device collects and disable any features you don’t need, like remote voice activation on a smart TV.
- Use a guest network if possible. Many modern routers allow you to create a separate ‘guest’ Wi-Fi network. Putting your IoT devices on this network isolates them from your primary devices like your laptop and phone.
4. What hackers are doing right now
To truly be prepared, you need to understand how the attacks themselves are evolving. The core principles of defense remain the same, but the methods hackers use are becoming more sophisticated. Forewarned is forearmed.
4.1. The rise of AI-driven attacks
Artificial Intelligence (AI) has supercharged hacking. I’ve seen it used to create phishing emails with perfect grammar and personalization, making them incredibly difficult to spot. Imagine an email that references a recent public event you attended and is sent at the exact moment you’re likely to be distracted.
AI also allows attackers to automate their efforts, testing millions of password combinations or searching for vulnerabilities at a massive scale. The defense remains the same: a skeptical eye and strong technical controls like MFA.
4.2. Deepfake phishing: when you can’t trust your eyes or ears
Deepfake technology allows attackers to create fake audio or video of someone you know. The most common scam I’m seeing is a voice clone used in ‘CEO fraud’, an employee receives a call that sounds exactly like their boss, urgently requesting a wire transfer. The same tactic can be used to impersonate a family member in distress. The key is verification through a separate channel.
| Warning: If a request for money or sensitive data seems unusual. Even if it sounds like someone you know, always verify through a separate, trusted channel like calling them back on their known phone number. |
4.3. Mobile-first vulnerabilities: beyond the browser
As we live more of our lives on our phones, hackers are focusing their efforts there. This goes beyond just malicious apps. For instance, that QR code you scan at a restaurant to see the menu? Hackers are now placing stickers with malicious QR codes over real ones, leading you to a phishing site that steals your data. Other emerging threats include calendar injection scams that fill your calendar with spammy, malicious events, and new vulnerabilities in mobile payment apps.
5. What to do if you’ve been hacked: a rapid recovery plan
Discovering a security breach is stressful, but having a clear plan can make all the difference and minimize the damage. If you suspect you’ve been hacked, my advice is to stay calm and follow these steps immediately.
5.1. Step 1: How do I know if I’ve been hacked?
Before you act, you need to recognize the signs. Here are some common indicators that an account or device has been compromised:
- You receive login alerts or password reset emails you didn’t initiate.
- Friends tell you they’re receiving strange messages or posts from your social media accounts.
- You see unfamiliar transactions on your bank or credit card statements.
- Your computer suddenly slows down, crashes, or displays lots of pop-up ads.
- You get a ransomware message demanding payment to unlock your files.
5.2. Step 2: Contain the damage
Your immediate priority is to stop the hacker from doing more harm. The first thing I do in this situation is to disconnect the suspect device from the internet (turn off Wi-Fi and unplug any network cables).
Then, using a separate, trusted device (like your phone or another computer), immediately change the passwords for your most critical accounts, starting with your primary email, followed by banking and any financial accounts. This is crucial because a compromised device may have a keylogger recording everything you type. Finally, contact your financial institutions to alert them to potential fraud.
5.3. Step 3: Eradicate and recover
Once contained, you need to remove the threat. Run a full scan with a reputable antivirus and anti-malware program. For severe infections, especially on a PC, the safest and most reliable method I recommend is to back up your essential files and perform a full factory reset of the operating system. This is why having regular backups is so important.
After cleaning your system, you can begin restoring your data. Report the incident to the relevant authorities, such as the FTC in the US. Finally, consider using an identity theft protection service to monitor your credit and personal information for any future misuse.
6. FAQs about what are some practices to prevent hacking?
Here are quick answers to some of the most common questions I get about personal cybersecurity.
Are password managers safe to use?
Yes. Reputable password managers use strong end-to-end encryption. Using weak or reused passwords is far riskier.
Is it possible to be 100% unhackable?
No. Nothing is perfect. The goal is to raise the difficulty so attackers move on.
Should I use public Wi-Fi?
Avoid it if possible. If you must use it, use a VPN, never access sensitive accounts without one.
What is the single most important step to prevent hacking?
Enable MFA on every critical account, it’s the strongest defense against account takeover.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| MFA | Multi-Factor Authentication | A security method that requires a user to provide two or more verification factors to gain access to an account. |
| IoT | Internet of Things | A network of physical devices (like smart speakers, cameras, and appliances) embedded with sensors and software to connect and exchange data over the internet. |
| SSID | Service Set Identifier | The public name of a Wi-Fi network that is broadcast to users. |
| WPA3 | Wi-Fi Protected Access 3 | The latest and most secure protocol for encrypting data sent over a Wi-Fi network. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your IP address, providing privacy and security, especially on public Wi-Fi. |
| SMiShing | SMS Phishing | A phishing attack conducted through text messages (SMS) to trick users into revealing personal information or clicking malicious links. |
| FTC | Federal Trade Commission | A U.S. government agency that handles consumer protection, including reporting identity theft and cybercrime. |
| AI | Artificial Intelligence | The simulation of human intelligence in machines, which can be used by hackers to automate and enhance attacks like phishing. |
7. Final thoughts: living securely in a connected world
Building strong digital security isn’t about a single, one-time fix. The Secure Living Blueprint I’ve outlined here is about developing conscious, consistent habits that become second nature. By taking control of your digital life, you can shift your mindset from one of fear to one of confidence and preparedness. Your security is a journey, not a destination. To get started, here are the most critical takeaways from this guide:
- Enable MFA everywhere. It is your single most powerful defense against account takeover.
- Automate your updates. Let your devices protect themselves by installing security patches as soon as they are available.
- Trust, but verify. Always be skeptical of urgent or unusual requests for information, even if they seem to be from a known source.
- Secure your entire ecosystem. Your security is only as strong as your weakest link, so apply these principles to your phone, router, and smart devices.
Your digital security is a journey, not a destination. Start with one step today and build a safer tomorrow.
For more in-depth guides to protect your digital life, I encourage you to explore our Online Security & Privacy categories on Afdevinfo.









