As a business owner, I know your focus is on growth, but figuring out what can be a threat to your business is a far bigger and more complex question than you might think. For over a decade, I’ve seen countless companies fixate on hackers and viruses, only to be blindsided by an internal mistake or a supply chain collapse. Most guides focus only on cybersecurity, but the real risks are much broader. This article is different. I’m here to give you a comprehensive, 360-degree view of the landscape.
In this guide, I’ll walk you through everything you need to know, from the ground up. We will cover:
- Core Cybersecurity Threats: The non-negotiable basics every business leader must understand, explained in simple terms.
- Internal & Operational Risks: How your own people and processes can become your biggest vulnerability.
- Critical Non-Cyber Risks: The external threats like regulations and supply chain failures that software can’t stop.
- An Actionable Audit: A step-by-step checklist you can use right now to assess your own company’s risk profile.
1. Core cybersecurity threats every business faces
Before we can talk about the bigger picture, we need to build a solid foundation. Understanding the most common cybersecurity threats to business is essential, not just for your IT team, but for you as a leader. These are the attacks I see successfully targeting small and medium businesses every single day because they prey on common weaknesses and human nature.
1.1. Phishing and social engineering: The art of deception
What it is:
Phishing is a fraudulent attempt, usually made through email, to trick someone into revealing sensitive information (like passwords or credit card numbers) or deploying malicious software. It’s a form of social engineering, which is the psychological manipulation of people into performing actions or divulging confidential information. Variations include ‘spear phishing’ (highly targeted at a specific person) and ‘pretexting’ (creating a fabricated scenario).
How it works:
These attacks bypass technology by targeting human trust. An attacker might impersonate a CEO, a trusted vendor like Microsoft, or a bank, creating a sense of urgency or authority to make you click a link or open an attachment without thinking. These phishing attacks are effective because they look legitimate.
A real-world SMB example:
An employee in accounting receives an email that appears to be from the CEO, urgently requesting a wire transfer to a new vendor to close a critical deal. The email uses the CEO’s name and signature. The employee, wanting to be helpful and feeling the pressure, makes the transfer. The money is lost forever.
Subject: Urgent: Invoice #78345 Overdue
Dear Accounts Payable,
Your recent invoice from us is overdue. Please click the link below to view the invoice and submit payment immediately to avoid service interruption.
View Invoice and Pay Here <– RED FLAG 1: Hovering over this link would show a strange, unofficial URL.
Failure to pay within 24 hours will result in account suspension. <– RED FLAG 2: Creates false urgency.
Sincerely,
The Microsoft Billing Team <– RED FLAG 3: Impersonating a trusted brand.
1.2. The business-halting threat
What it is:
Ransomware is a type of malicious software that encrypts your files, making them completely inaccessible. The attackers then demand a ransom payment, usually in cryptocurrency, in exchange for the decryption key. It is a devastating, business-halting threat.
How it works:
It often gets into your system through the very ransomware and phishing attacks we just discussed, or by exploiting unpatched software vulnerabilities. Once inside, it spreads silently across your network, encrypting everything from spreadsheets to customer databases. Modern attackers often use a ‘double-extortion’ tactic: they steal a copy of your sensitive data *before* encrypting it, threatening to leak it publicly if you don’t pay.
A real-world SMB example:
A small marketing firm comes into work on a Monday to find every computer displaying a ransom note. They can’t access client files, send emails, or issue invoices. Their operations are completely frozen. They now face a terrible choice: pay a huge ransom with no guarantee of getting their data back, or try to rebuild from scratch, which could take weeks and destroy their reputation.
The average cost of a ransomware attack for a small business, including downtime, recovery, and the ransom itself, can easily run into the hundreds of thousands of dollars, a crippling blow from which many never recover.
2. Uncovering operational and insider threats
While we spend a lot of time building walls to keep external attackers out, I’ve often found that the most damaging events originate from within. It’s a common mistake to assume all threats are external. When asked if insider threats are more dangerous than external hackers, my answer is that they can be far more damaging. An insider already has trust and access, two things an external hacker has to fight for. These internal issues, including both human error and flawed processes, create significant operational vulnerabilities.
2.1. The human element between accidental vs. malicious insiders
Insider threats aren’t just about disgruntled employees trying to cause harm. In my experience, accidental incidents are far more common, though both can be equally destructive. It’s a management and training challenge, not just a security one. Understanding the difference is key to building the right defenses.
Here is a simple breakdown of the two main types of insider threats:
| Accidental Insider Threat | Malicious Insider Threat |
|---|---|
| An employee who makes an honest mistake without intending to cause harm. | A current or former employee, contractor, or partner who intentionally misuses their authorized access to compromise data or systems. |
| Example: Emailing a sensitive client spreadsheet to the wrong recipient with a similar name. | Example: A sales representative who is about to leave for a competitor downloads the entire client list to their personal device. |
| Prevention Goal: Better training, clear processes, and technology that can catch mistakes (e.g., data loss prevention tools). | Prevention Goal: Strong access controls (least privilege principle), activity monitoring, and formal offboarding procedures. |
2.2. System and process failures
Beyond individual actions, your company’s day-to-day operational procedures can be a massive threat. I often say that strong processes are just as crucial as strong software. When your internal systems and policies are weak, you are essentially leaving the door open for both accidental data leaks and determined attackers. This includes the risk of ‘shadow IT’ when employees use unapproved software or cloud services that your IT team can’t secure.
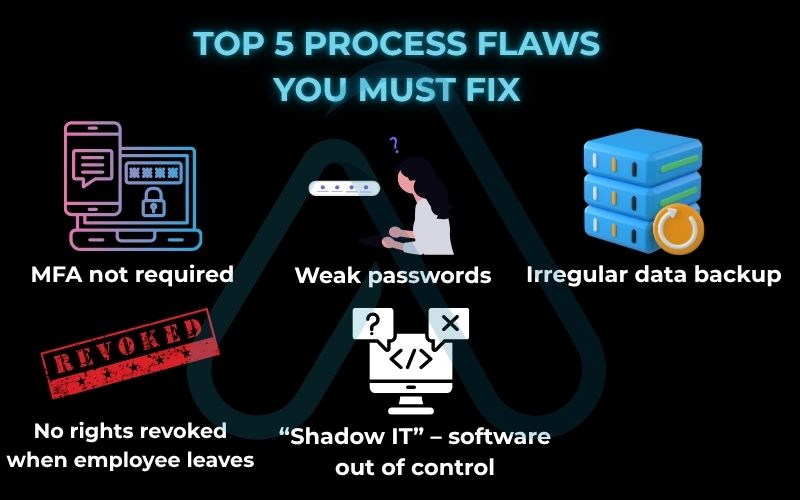
Here are some common process flaws I regularly see that you should assess in your own business:
- No mandatory multi-factor authentication (MFA) on email and critical systems.
- Weak or shared password policies among employees.
- Irregular or untested data backup schedule.
- No formal process for revoking access when an employee leaves.
- Lack of a policy for installing and using third-party software.
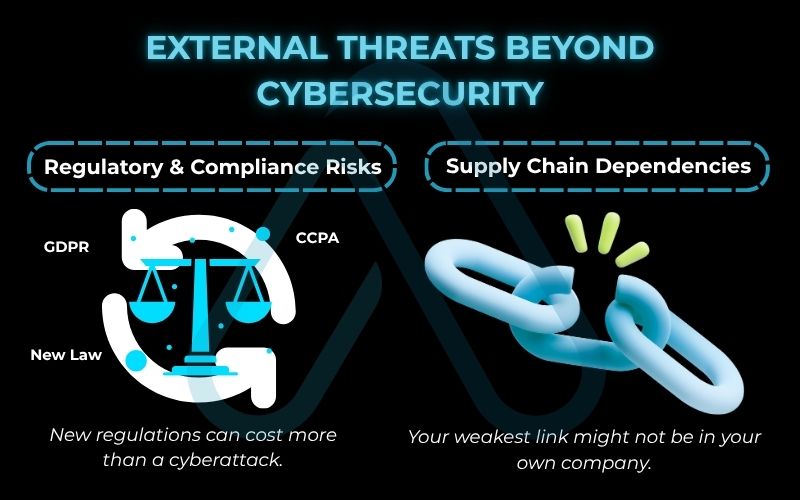
3. What can be a threat to your business from the outside world
Your strongest firewall can’t protect you from a new regulation or a broken supply chain. This is where my guide differs from most cybersecurity checklists. I’ve seen stable, successful businesses get completely derailed by external factors they never considered. These are business risks not related to cybersecurity, but they can have an equally, if not more, devastating impact on your bottom line and ability to operate.
3.1. Regulatory and compliance changes
New laws and regulations, particularly around data privacy, can appear overnight and create significant financial and operational risks. For example, a small online retailer in the US might suddenly find they need to comply with Europe’s GDPR or California’s CCPA if they sell to customers in those regions. This means overhauling how they collect, store, and manage customer data. The risk of non-compliance isn’t just theoretical; it comes with the threat of heavy fines and legal action.
A single compliance failure can result in fines that exceed the cost of a data breach, making regulatory awareness a critical business function.
3.2. Supply chain disruptions and dependencies
Modern businesses are incredibly interconnected. The risk of being over-reliant on a single supplier is a threat that has become painfully obvious in recent years. Think about the global semiconductor shortage or the shipping container crises. These events had cascading effects on thousands of businesses.
Your supply chain risks are not just about whether your supplier can deliver parts; it’s also about their own security. If your critical software vendor suffers a breach, that breach can directly impact you. A single failure anywhere in your supply chain can halt your production, delay services, and damage your customer relationships.
3.3. ESG, geopolitical instability, and natural disasters
To truly future-proof your business, you have to look at the bigger picture. A new category of large-scale, often uncontrollable events is creating an unpredictable business environment. This includes everything from extreme weather events disrupting logistics to political conflicts impacting market access. Being aware of these macro-level threats is the first step in building a resilient business strategy.
Here is how I recommend business owners think about these emerging risks:
| Risk Category | Definition | Key Question for Your Business |
|---|---|---|
| Environmental, Social, & Governance (ESG) | Risks related to changing societal expectations, environmental regulations, and corporate responsibility. | Are our business practices sustainable and aligned with the evolving values of our customers and investors? |
| Geopolitical Instability | Risks from international conflicts, trade disputes, and political changes that can disrupt markets or supply chains. | How exposed is our business to suppliers, partners, or customers in politically unstable regions? |
| Environmental & Natural Disasters | Risks from extreme weather events like floods, wildfires, or hurricanes that can destroy infrastructure and halt operations. | Do we have a contingency plan and adequate insurance to handle a physical disruption to our primary place of business? |
4. Calculating the true cost: The financial, legal, and reputational impact
Understanding a threat is one thing, but it’s not until you calculate its potential cost that the need for prevention becomes truly urgent. A single incident can spiral outwards, affecting your finances, legal standing, and the trust you’ve built with your customers. The financial and reputational impact is often far greater than business owners anticipate, extending well beyond the initial event.
4.1. The direct and indirect financial fallout
The financial costs of a security incident are multifaceted. Direct costs are the immediate, out-of-pocket expenses you’ll incur to manage the crisis. These include things like ransom payments, regulatory fines, legal fees for counsel, and hiring IT forensics and recovery services. But in my experience, the indirect costs are what truly cripple a business.
These are the costs of business downtime, lost revenue from being unable to operate, the long-term increase in your insurance premiums, and the cost of notifying customers and offering credit monitoring. For a small business, weeks of lost revenue can be an extinction-level event.
4.2. Rebuilding trust after reputational damage
One of the most common questions I get is, ‘How can cyberattacks affect a business’s reputation?’ My answer is simple: it can destroy it. Reputational damage is insidious because it’s hard to quantify and can outlast any financial harm. It manifests as a loss of customer trust, negative press coverage, and a tarnished brand value that you’ve spent years building.
Customers are less likely to do business with a company they believe can’t protect their data. A hypothetical quote I often use to illustrate this is, “I loved their product, but after they lost my data, I just couldn’t trust them with my credit card information again.” This erosion of trust is incredibly difficult and expensive to rebuild.
5. Your interactive business threat audit: A 3-step self-assessment
Now that we’ve covered the landscape of threats, it’s time to turn this knowledge into action. I’ve designed this section as a practical, pen-and-paper exercise to help you get an immediate sense of your own company’s vulnerabilities. Go through these questions honestly. The goal isn’t to get a perfect score, but to identify your priority action items.
5.1. Step 1: Auditing your cybersecurity posture
These questions cover your fundamental technical defenses.
- Is Multi-Factor Authentication (MFA) enabled on all critical accounts (email, banking, cloud services)? (Yes/No)
- Do you have a strong, enforced password policy (e.g., minimum length, complexity)? (Yes/No)
- Are your data backups performed automatically, regularly, and are they periodically tested? (Yes/No)
- Do you provide regular cybersecurity awareness training to all employees? (Yes/No)
5.2. Step 2: Evaluating your operational resilience
These questions focus on your internal processes and human-centric security.
- Do you have a formal process to immediately revoke access for departing employees? (Yes/No)
- Is access to sensitive data restricted on a ‘need-to-know’ basis? (Yes/No)
- Do you have a clear policy on the use of personal devices and third-party applications for work? (Yes/No)
- Is there a physical security plan for your office, including access control? (Yes/No)
5.3. Step 3: Assessing your external risk exposure
These final questions look at your preparedness for non-cyber threats.
- Have you identified your critical suppliers, and do you have alternative options or backup plans? (Yes/No)
- Are you aware of the key data privacy regulations (like GDPR or CCPA) that apply to your business? (Yes/No)
- Do you have a business continuity plan for events like natural disasters or power outages? (Yes/No)
- Is your business insurance (including cyber insurance) reviewed annually and aligned with your current risk profile? (Yes/No)

| How to interpret your results: For every ‘No’ you answered, you have identified a significant vulnerability. Add each of these items to a priority action list. This is the starting point for building a more resilient business. |
6. From awareness to action: Building your business risk management framework
Your audit has given you a list of weaknesses. Now, let’s build the framework to fix them. A strong business risk management strategy isn’t about buying a single piece of software; it’s a multi-layered approach that combines technology, people, and processes. This is how you take proactive steps to protect your business from security threats and build true resilience.
6.1. Technical safeguards: Your first line of defense
These are the foundational tools that protect your digital assets. They are your first line of defense against the cyber threats we discussed in the first section.
Here are the essential technical controls I recommend for every business:
- Firewall & Endpoint Protection: A firewall acts as a gatekeeper for your network traffic, while endpoint protection (antivirus/anti-malware) secures individual devices like laptops and servers.
- Email Filtering: An advanced email security service can scan incoming emails for phishing links, malicious attachments, and spam before they ever reach your employees’ inboxes.
- Regular Patching: Ensure that all your software, from your operating systems to your applications, is consistently updated. These patches often fix critical security vulnerabilities that attackers exploit.
- Data Encryption: Encrypting sensitive data both at rest (on your hard drives) and in transit (over the internet) ensures that even if it’s stolen, it remains unreadable.
6.2. Fostering a security-aware company culture
I cannot stress this enough: technology alone is never enough. Your employees can either be your weakest link or your greatest security asset. Fostering a culture of security awareness is one of the highest-return investments you can make. This is about transforming security from an IT problem into a shared responsibility for everyone in the company.
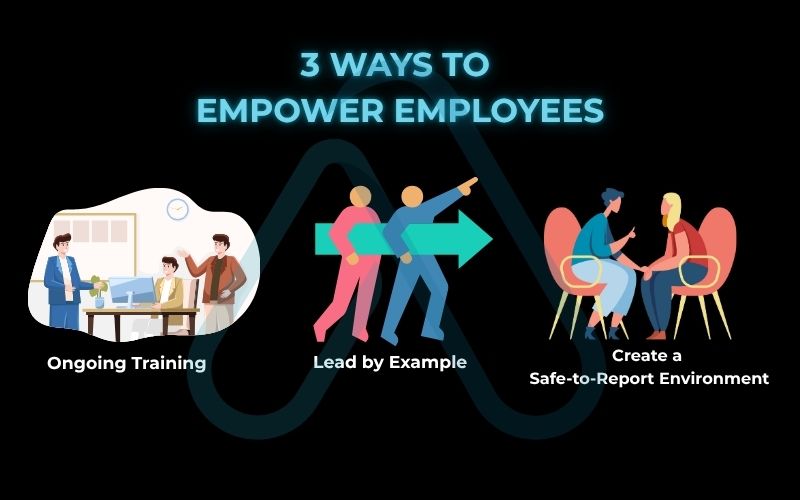
Your Human Firewall: 3 Ways to Empower Employees
- Ongoing Training: Don’t just do a one-time orientation. Conduct regular, engaging training sessions on how to spot phishing emails and practice good security hygiene. Use real-world examples.
- Create a Safe-to-Report Environment: Make it clear that employees will not be punished for reporting a security mistake, like clicking on a suspicious link. The sooner you know, the faster you can respond.
- Lead by Example: As a leader, you must follow the same security policies you expect from your team. Your commitment sets the tone for the entire organization.
6.3. Infographic: Mapping threats to responses for different business scales
The right response to a threat can depend on the size and resources of your business. A solo entrepreneur has different capabilities than a 40-person office. The following table provides a blueprint for prioritizing your actions based on your business scale.
| Threat | Response for a Small Business (1-10 Employees) | Response for a Medium Business (10-50 Employees) |
|---|---|---|
| Ransomware / Phishing | Focus on basics: mandatory MFA on all accounts, automated cloud backups (e.g., Google Drive, OneDrive), and basic employee training on spotting fake emails. | Implement a dedicated email filtering service, conduct regular phishing simulation tests, and have a formal incident response plan. |
| Accidental Insider Threat | Establish simple, clear data handling policies. Use cloud platforms with basic user permission settings to limit access. | Deploy more granular access controls. Create a formal employee offboarding checklist that includes revoking all access. |
| Supply Chain Failure | Identify the one or two suppliers that would shut your business down if they failed. Research at least one alternative for each. | Actively diversify key suppliers. Maintain a small buffer inventory for critical components. Include security and reliability clauses in supplier contracts. |
7. Aligning insurance and compliance with your risk profile
Once you’ve built your internal defenses, the final layer of your strategy is the safety net: insurance and compliance. I see these not as burdens, but as strategic tools. Cyber insurance can provide a financial backstop in a worst-case scenario, while adhering to compliance standards gives you a proven roadmap for building a secure operation. This advanced-level thinking is what separates resilient businesses from vulnerable ones.
Many business owners ask me, “Do I need cyber insurance?” In today’s landscape, my answer is an emphatic yes. A good cyber liability policy can cover costs related to data recovery, legal fees, customer notifications, and regulatory fines. However, it’s crucial to understand what it *doesn’t* cover. Most policies won’t pay for system upgrades or the full extent of reputational damage. It’s a critical financial tool, not a replacement for good security practices.
Another common question is, “Is a standard like ISO 27001 only for large enterprises?” While full certification might be too much for a small business, using the framework as a guide is incredibly valuable. It provides a world-class checklist for managing information security, helping you identify and plug gaps you might have otherwise missed.
8. FAQs about what can be a threat to your business
Here are answers to some of the most common questions I get about can be a threat to your business. These provide quick, direct answers and link back to more detailed sections of this guide.
What are the top threats facing small businesses today?
Phishing and ransomware, insider threats, and supply chain failures.
How does it work?
External attacks happen more frequently.
Insiders can cause more damage because they already have legitimate access.
Are insider threats more dangerous than external hackers?
Regulatory fines, supplier collapse, economic shifts, reputational damage, natural disasters.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| MFA | Multi-Factor Authentication | A security process that requires users to provide two or more verification factors to gain access to a resource, such as a password and a code from their phone. |
| GDPR | General Data Protection Regulation | A regulation in EU law on data protection and privacy for all individual citizens of the European Union and the European Economic Area. |
| CCPA | California Consumer Privacy Act | A state statute intended to enhance privacy rights and consumer protection for residents of California, United States. |
| ESG | Environmental, Social, and Governance | A set of standards for a company’s operations that socially conscious investors use to screen potential investments. |
| Shadow IT | Shadow Information Technology | The use of IT systems, devices, software, applications, and services without explicit IT department approval. |
9. Final thoughts: From threatened to prepared
The goal of this guide was not to scare you, but to empower you. Understanding what can be a threat to your business is the first and most critical step toward building a truly resilient organization. The modern threat landscape is too complex for a narrow, cybersecurity-only focus. A proactive, holistic approach to risk management is no longer optional, it is essential for survival and growth.
By now, I hope you see your business not just as a creator of value, but as an ecosystem that needs protection on multiple fronts. Here are the most critical takeaways:
- Look Beyond Hackers: The most significant threats to your business integrate cyber, operational, and external risks. You must plan for all three.
- People are Your Perimeter: Your employees and your internal processes can be either your biggest vulnerability or your strongest defense. Invest in training and clear procedures.
- Action Over Awareness: Knowledge is only powerful when applied. Use the threat audit I provided to identify your specific weaknesses and build a concrete action plan.
The journey from threatened to prepared begins today. Start with one small change: enable MFA on your primary email account, schedule a backup test, or review your supplier list. Each step forward makes your business stronger and more capable of weathering the storms ahead.
For more in-depth guides to secure your digital life and business operations, explore our Online Security & Privacy categories on Afdevinfo.









