Ever felt like the cybersecurity experts on the news are speaking a different language? You’re not alone. In my decade of experience, I’ve seen how this complex topic can feel overwhelming. So, let’s get straight to the point and answer your question: what does cyber security entail? At its core, it’s about protecting our digital lives from personal photos to corporate secrets from theft, damage, or unauthorized access. This guide is designed to demystify the jargon and give you practical, actionable insights.
By the time you’re done reading, you’ll have a clear understanding of:
- The fundamental building blocks of cybersecurity.
- Why it’s critically important for you, your family, and your business.
- The most common threats you’re likely to face today.
- Actionable steps and best practices to protect yourself immediately.
- How you can even start a career in this growing field.
1. What are the main elements of cybersecurity?
Before we dive into the deep end, let’s establish a solid foundation. Think of cybersecurity like securing your home. You don’t just have one lock on the front door; you have locks on windows, maybe an alarm system, and perhaps a guard. Each layer adds protection. Cybersecurity applies this layered concept to your digital assets. It’s a key part of the broader field of information security, which covers the protection of data in all its forms, both digital and physical.
The entire practice is governed by three foundational principles, which I’ve seen serve as the bedrock of every effective security strategy. We call it the CIA Triad.
At the heart of all cybersecurity efforts are three core goals: Confidentiality (keeping secrets secret), Integrity (ensuring data is trustworthy and unaltered), and Availability (making sure data is accessible when needed).
The CIA Triad
1.1. The three pillars: Deconstructing the CIA triad
Understanding these three pillars is the first major step to grasping what cybersecurity truly is. Let me break down each one with a simple structure: its definition, why it matters, and a real-world example. I’ve put them into a simple table for clarity.
| Pillar | Definition & Why It Matters | Real-World Example |
|---|---|---|
| Confidentiality | Definition: Ensuring that information is not disclosed to unauthorized individuals, entities, or processes. Why it Matters: It protects your privacy and sensitive data from prying eyes. A breach of confidentiality can lead to identity theft, financial loss, or corporate espionage. | When you send a message on a secure app like Signal or WhatsApp, end-to-end data encryption scrambles the message so only you and the recipient can read it. |
| Integrity | Definition: Maintaining the consistency, accuracy, and trustworthiness of data over its entire lifecycle. Why it Matters: It ensures that the information you rely on is correct. Without integrity, financial records could be altered, and medical data could become dangerously inaccurate. | When you transfer $100 from your bank account, integrity ensures the system doesn’t accidentally change that amount to $1,000 or $10 mid-transfer. |
| Availability | Definition: Ensuring that systems and data are accessible and usable upon demand by an authorized user. Why it Matters: It guarantees that you can get to your information when you need it. A lack of availability can halt business operations or prevent you from accessing critical services. | An e-commerce website remaining online and functional during a massive Black Friday sales event is a perfect example of maintaining availability under high demand. |
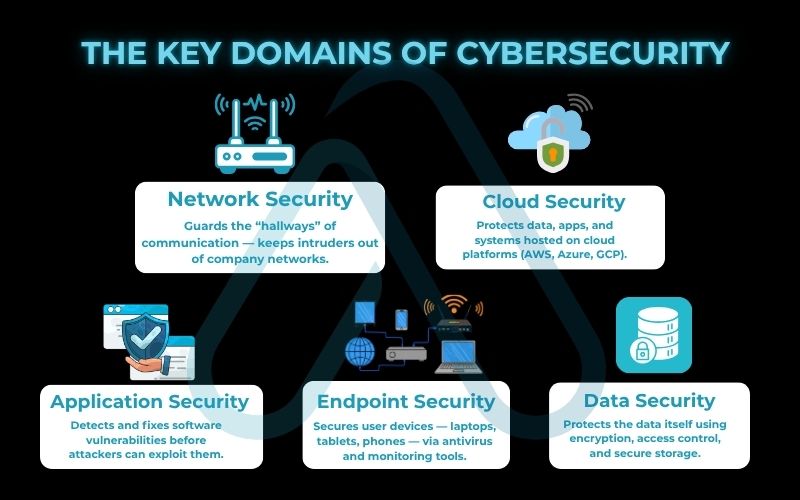
1.2. The key domains of cybersecurity
Cybersecurity isn’t a single job; it’s a collection of specialized fields that work together. Think of it like the different security teams in a large corporate building, one team guards the entrances, another monitors the surveillance cameras, and a third manages access badges. They’re all interconnected. Here are the key domains you’ll often hear about:
- Network Security: Securing the computer networks that connect everything, from servers to laptops, against intruders.
- Cloud Security: Protecting data, applications, and infrastructure hosted in cloud environments like AWS, Azure, or Google Cloud.
- Application Security: Finding and fixing vulnerabilities in software and applications before they can be exploited by attackers.
- Endpoint Security: Protecting the end-user devices like laptops, smartphones, and tablets. This often involves endpoint protection software like antivirus.
- Data Security: Implementing measures like encryption and access controls to protect the data itself, both when it’s stored and when it’s being transmitted.
2. Why is cybersecurity important for businesses and individuals?
Now that we understand the ‘what’, let’s focus on the ‘why’. The importance of cybersecurity has skyrocketed as our lives have become increasingly digital. For businesses, a cyber attack can be catastrophic, leading to financial loss, severe reputational damage, and major operational disruption. A proactive approach, known as risk management, is no longer optional; it’s essential for survival. It involves identifying potential threats and implementing strategies to minimize their impact.
The numbers don’t lie. According to a 2023 report from IBM, the average cost of a data breach reached an all-time high of $4.45 million. That’s a staggering figure that many small businesses simply cannot absorb.
The personal cost of a breach
But this isn’t just a corporate problem. For individuals, the stakes are just as high. A compromised email account can lead to identity theft. Hacked social media can result in reputational damage among friends and colleagues. As a remote worker, an unsecured home network could even lead to a breach at your company, putting your job at risk. My personal data, your personal data. It’s all valuable, and we need to be the first line of defense in protecting it.
3. What are the biggest cybersecurity threats today?
To defend yourself, you need to understand the modern threat landscape. While it’s constantly evolving, a few common attack vectors are responsible for the vast majority of incidents I’ve seen. The scary part? Many of them rely on simple human error, making awareness one of our most powerful weapons. I’ve summarized the most common threats in the table below to make them easier to digest.
| Threat Name | How it Works (Simple Explanation) | Real-World Example |
|---|---|---|
| Phishing | Attackers send fraudulent emails or messages disguised as legitimate ones to trick you into revealing sensitive information like passwords or credit card numbers. | You receive an email that looks like it’s from Netflix, saying your account is suspended. It asks you to click a link and re-enter your payment details, but the link leads to a fake website. |
| Malware (including Ransomware) | Malicious software designed to disrupt operations, steal data, or gain unauthorized access. Ransomware is a specific type that encrypts your files and demands a ransom payment for their release. | You download a free software utility from an untrusted website. Unbeknownst to you, it contains ransomware that locks all your personal photos and documents, displaying a message demanding a Bitcoin payment. |
| Man-in-the-Middle (MitM) Attack | An attacker secretly intercepts and relays communication between two parties who believe they are communicating directly with each other. | You connect to a fake public Wi-Fi network at a coffee shop (e.g., “Free_Cafe_WiFi” instead of “Cafe_Official_WiFi”). The attacker who set it up can now see all the unencrypted data you send and receive. |
| Denial-of-Service (DoS) Attack | An attacker floods a server or network with overwhelming traffic, making the service unavailable to legitimate users. | A group of attackers simultaneously sends millions of requests to a bank’s website, causing it to crash and preventing customers from accessing their online banking services. |
4. What tools and strategies help protect against cyber attacks?
Facing these threats can feel daunting, but the good news is that we have a powerful defensive toolkit at our disposal. I like to group protective measures into two main categories: the technology we use and the human-centric practices we follow. Both are essential for a strong defense. Modern security frameworks like Zero Trust, which operates on the principle of “never trust, always verify” and guidelines from organizations like NIST provide a roadmap for robust protection.
Ultimately, a strong defense relies on building multiple layers of security, a core principle of cybersecurity best practices.
4.1. Practical first steps for small businesses and entrepreneurs
If you’re a small business owner, you’re a prime target because attackers assume you have fewer defenses. From a risk management perspective, you need to protect your most critical assets first. Here is a simple plan to get you started.
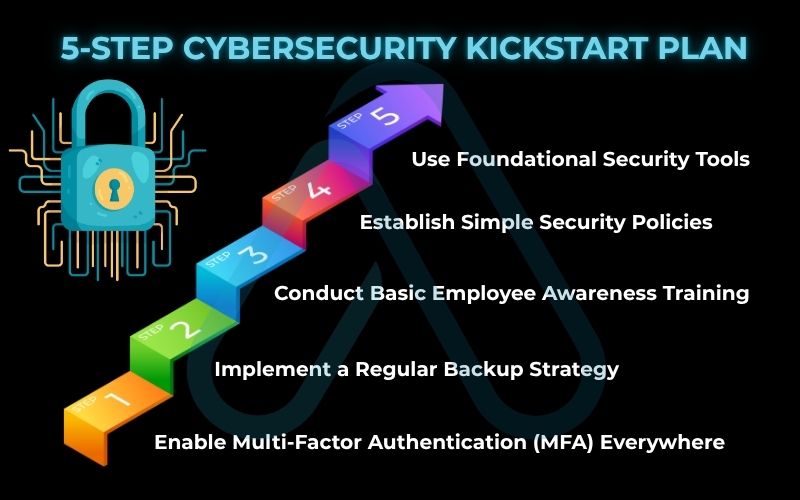
Here is my recommended 5-Step Cybersecurity Kickstart Plan:
- Enable Multi-Factor Authentication (MFA) Everywhere: This is your single most impactful action. Require MFA for email, financial accounts, and all critical systems. It’s like adding a second, high-tech lock to your front door.
- Implement a Regular Backup Strategy: Regularly back up all critical data to a secure, offsite location. The 3-2-1 rule is a great start: three copies of your data, on two different media types, with one copy offsite. This is your ultimate defense against ransomware.
- Conduct Basic Employee Awareness Training: Your employees are your first line of defense. Train them to recognize phishing emails, use strong passwords, and report suspicious activity.
- Establish Simple Security Policies: Create a basic ‘Acceptable Use Policy’ that outlines rules for using company devices and data. You don’t need a 100-page document; a simple one-pager is better than nothing. You can find many free templates online to get started.
- Use Foundational Security Tools: Invest in a good password manager for your team (like Bitwarden or 1Password), reputable endpoint protection software (antivirus/anti-malware), and encourage secure communication.
4.2. Essential cybersecurity best practices for everyone
Whether you’re at home, at a coffee shop, or in the office, these universal habits can dramatically improve your personal security. Think of them as digital hygiene. These are the core cybersecurity best practices I share with all my friends and family. When these practices fail, a company moves into an incident response phase, which is a far more stressful and costly situation.
The FBI’s 2022 Internet Crime Report states that implementing MFA could prevent over 99.9% of account compromise attacks.
Here are some key do’s and don’ts:
- Do this: Use a strong, unique password for every account, preferably generated and stored in a password manager.
- Avoid this: Reusing the same password across multiple sites. If one gets breached, they all get breached.
- Do this: Keep your software and operating systems updated. These updates often contain critical security patches.
- Avoid this: Ignoring update notifications. You’re leaving a known vulnerability open for attackers.
- Do this: Be skeptical of unsolicited emails and messages. Hover over links to check the true destination before clicking.
- Avoid this: Clicking links or downloading attachments from unknown or suspicious senders.
- Do this: Use a Virtual Private Network (VPN) when connecting to public Wi-Fi to encrypt your internet traffic.
- Avoid this: Conducting sensitive activities like online banking on unsecured public networks.
5. How do I start a cybersecurity career?
With the demand for security professionals at an all-time high, I get this question a lot. It’s an incredibly rewarding field, and the best part is you don’t need to be some sort of elite ‘hacker’ to get started. The industry needs people from diverse backgrounds with a wide range of skills, from deep technical analysis to policy and communication. Many information security roles are open to newcomers who are curious and willing to learn.
There are several common pathways into the industry:
- Formal Education: A university degree in computer science, IT, or a specialized cybersecurity program provides a strong theoretical foundation.
- Certifications: Industry-recognized certifications like CompTIA Security+, Certified Ethical Hacker (CEH), or CISSP can validate your skills and open doors, sometimes even more effectively than a degree.
- Self-Learning & Bootcamps: With countless online resources, labs (like TryHackMe or Hack The Box), and intensive bootcamps, it’s more possible than ever to build practical, hands-on skills on your own.
5.1. Comparing cybersecurity careers, roles, and required skills
The term ‘cybersecurity professional’ covers a huge range of jobs. To help you understand the landscape, I’ve created a table comparing a few popular roles. The skills required for these roles often include elements of incident response (reacting to a breach) and risk management (proactively preventing one).
I also want to specifically highlight the growing global demand for remote talent. This has created incredible opportunities for professionals in Africa and the Global South, where tech hubs are rapidly expanding and the need for skills in cloud security and data privacy is immense.
| Role Title | Primary Responsibility | Key Skills (Technical & Soft) | Typical Entry Point |
|---|---|---|---|
| Security Analyst | Monitors an organization’s networks and systems for security breaches or intrusions. Often the first line of defense. | Technical: Network monitoring tools, log analysis, intrusion detection systems. Soft: Attention to detail, analytical thinking. | Entry-level role, often from an IT support background. CompTIA Security+ is a common starting certification. |
| Penetration Tester (Pen Tester) | Acts as an ‘ethical hacker’ by legally and ethically trying to break into computer systems to find vulnerabilities before malicious hackers do. | Technical: Hacking tools, scripting (Python/Bash), deep knowledge of networks and operating systems. Soft: Creativity, problem-solving, reporting. | Intermediate role. Often requires hands-on experience and certifications like OSCP or CEH. |
| Security Consultant | Advises companies on how to improve their security posture, develop policies, and manage risk. | Technical: Broad knowledge of security domains, frameworks (NIST, ISO 27001). Soft: Communication, project management, business acumen. | Mid-to-senior level role. Often requires years of experience and high-level certifications like CISSP. |
6. Your interactive checklist: Applying cybersecurity fundamentals
Knowledge is only powerful when applied. To help you put everything we’ve discussed into practice, I’ve created a checklist based on common, real-world scenarios. Go through these and see how you stack up.
Here are some actions you can take right now:
| Action item | Why it matters | |
| Scenario 1: You’re a remote worker connecting from a cafe. | Connect to the internet using a VPN on your laptop and phone. | This encrypts your traffic, preventing anyone on the public Wi-Fi (including attackers) from snooping on your activity. This is a core tenant of cybersecurity best practices. |
| Scenario 2: You’re a small business owner setting up a new employee laptop. | Install reputable endpoint protection (antivirus/anti-malware) software before the employee starts using the device. | This provides a critical layer of defense against malware from day one, forming the basis of your endpoint protection strategy. |
| Scenario 3: You just received a ‘password reset’ email you didn’t request. | Do not click the link. Go directly to the official website by typing the address in your browser and check your account security there. Enable MFA if you haven’t already. | This is a classic phishing attempt to steal your credentials. Verifying directly on the site bypasses the attacker’s trap. |
| Scenario 4: A new app on your phone is asking for access to your contacts and microphone. | Deny the permissions unless the app absolutely needs them to function (e.g., a calling app needing the microphone). | This follows the principle of ‘least privilege,’ minimizing the data an app can access and reducing your risk if the app’s developer is breached. |
7. FAQs about what does cyber security entail
Here are answers to some of the most common questions I get about cyber security entail. These provide quick, direct answers and link back to more detailed sections of this guide.
Is cybersecurity only for big companies?
No. SMBs are targeted a lot because criminals assume they have weaker security.
Do I need to be an expert coder to work in cybersecurity?
No. Some roles need coding, but many focus on policy, training, risk, and communication.
Is ‘cybersecurity’ the same as ‘information security’?
Not exactly. InfoSec covers all information (digital + physical). Cybersecurity focuses on digital systems only.
Can 100% security be achieved?
No. Absolute security is impossible. The goal is to manage risk and use layered defenses.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| CIA | Confidentiality, Integrity, and Availability | The three core principles of information security, forming the CIA Triad. |
| DoS | Denial-of-Service | A type of cyber attack that aims to make a machine or network resource unavailable to its intended users. |
| GRC | Governance, Risk, and Compliance | An area of cybersecurity focused on policy, risk management, and adherence to legal and industry regulations. |
| MFA | Multi-Factor Authentication | A security process that requires users to provide two or more verification factors to gain access to a resource. |
| MitM | Man-in-the-Middle | An attack where the attacker secretly intercepts and relays communications between two parties. |
| NIST | National Institute of Standards and Technology | A US agency that develops cybersecurity standards, guidelines, and best practices. |
| VPN | Virtual Private Network | A tool that creates a secure, encrypted connection over a public network like the internet. |
| Malware | Malicious Software | Any software intentionally designed to cause disruption to a computer, server, client, or computer network. |
| Ransomware | Ransom-demanding Malware | A type of malware that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid. |
| Phishing | N/A | A social engineering attack used to trick users into revealing sensitive information. |
8. Final thoughts
Navigating the world of cybersecurity doesn’t have to be intimidating. By now, I hope you have a much clearer picture of what the field entails, why it’s so critical in our digital age, and the practical first steps you can take to protect yourself. It’s not about becoming an overnight expert; it’s about building better habits and understanding the basics.
Here are the key takeaways I want you to remember:
- Cybersecurity is the practice of protecting digital systems and data from attack, built on the core principles of Confidentiality, Integrity, and Availability.
- It is essential for everyone, not just large corporations. The personal and financial costs of a breach can be devastating for individuals and small businesses.
- Awareness is your best defense. Understanding common threats like phishing and malware can help you avoid becoming a victim.
- Simple, proactive steps like using MFA, keeping software updated, and practicing good password hygiene provide a massive boost to your security.
Your digital safety is in your hands. Taking one small, proactive step today is more powerful than worrying about a thousand potential threats tomorrow.
I encourage you to start with one thing from this guide, like turning on MFA for your primary email account. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.









