Let’s get straight to the point about what is cyber attack, a term that dominates headlines and impacts our digital lives. A cyber attack is a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization. In my decade of experience in cybersecurity, I’ve seen these attacks evolve, but their core purpose remains the same: to compromise, steal, alter, or destroy data. This is a critical concept in the broader field of information security, and understanding it is the first step toward protecting yourself in our increasingly connected world.
I often tell people to think of a cyber attack like a digital burglary. Instead of breaking a window, attackers exploit a digital vulnerability. Instead of stealing jewelry, they steal data, money, or identities. Their goal is to gain unauthorized access to your digital ‘house’ and take your most valuable assets.
1. What is cyber attack? A clear definition for 2025
A cyber attack is an intentional act by an individual or organization using technology to illegally penetrate a computer system, network or digital device. The main goal is to disrupt, sabotage, control the system, or steal, change, destroy sensitive data for malicious purposes such as blackmail or espionage.
1.1. Cyber attack vs. cyber threat: Understanding the key difference
People often use the terms ‘cyber attack’ and ‘cyber threat’ interchangeably, but in my field, the distinction is crucial. A threat is the potential for harm, while an attack is the realization of that potential. To make this perfectly clear, I’ve broken down the difference in this table.
| Feature | Cyber Threat | Cyber Attack |
|---|---|---|
| Definition | A potential event or circumstance that could cause harm to a system or organization. | An active, malicious attempt to exploit a vulnerability and cause harm. |
| State | Potential / Possibility | Action / Event in progress |
| Example | A newly discovered software vulnerability in a popular application is a cyber threat. | An attacker actively exploiting that vulnerability to steal customer data is a cyber attack. |
2. How do cyber attacks happen? The anatomy of a breach
Cyber attacks rarely happen in a single, explosive moment. Instead, they are often methodical processes with several distinct stages. From my experience analyzing breaches, I’ve found that attackers typically follow a lifecycle, moving from initial research to achieving their final objective. This process exploits vulnerabilities not just in technology, but also in human behavior and organizational processes.
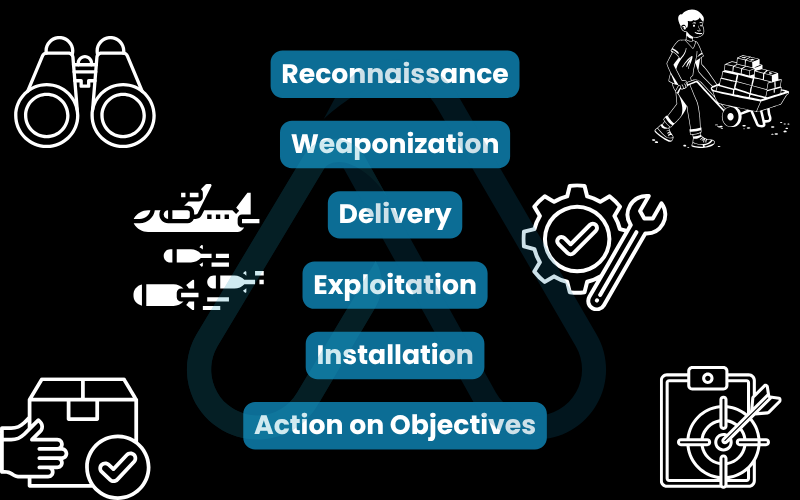
Here are the common stages of a breach, which you can visualize in the infographic below.
- Reconnaissance: The attacker scouts for weaknesses, like an outdated server, unpatched software, or an employee’s public social media profile.
- Weaponization: The attacker creates a malicious payload, such as a ransomware-laced email attachment or a custom virus designed to exploit a specific security vulnerability.
- Delivery: The weapon is sent to the target. This is commonly done through phishing emails, malicious websites, or infected USB drives.
- Exploitation: The malicious code is triggered, taking advantage of a vulnerability to gain an initial foothold in the system.
- Installation: The attacker installs malware or other tools to maintain persistent access to the compromised network.
- Action on Objectives: With access secured, the attacker carries out their goal, whether it’s stealing data (exfiltration), encrypting files for ransom, or disrupting operations.
3. What are the most common types of cyber attacks?
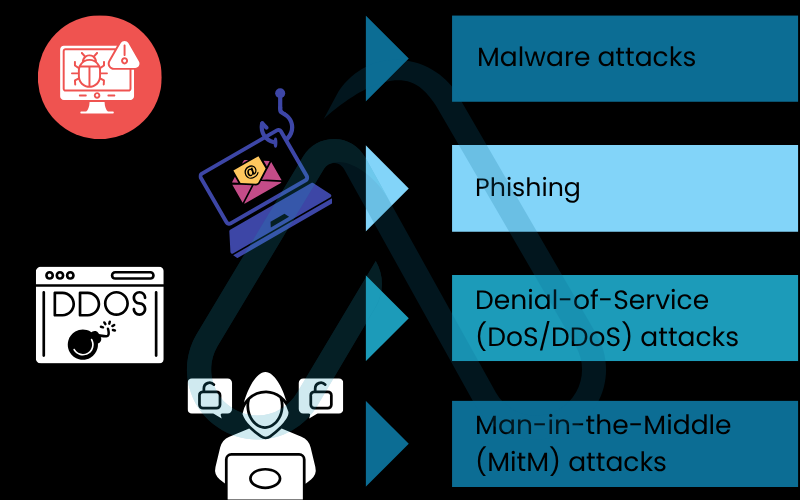
The methods attackers use are incredibly diverse, but from my experience, most incidents fall into a few key categories. Understanding these common attack types is essential for recognizing and defending against them. I’ll walk you through the most prevalent ones you’re likely to encounter.
3.1. Malware attacks: The digital infection
Malware, short for malicious software, is one of the most common weapons in an attacker’s arsenal. It’s an umbrella term for any software intentionally designed to cause damage to a computer, server, client, or computer network. These digital infections can be used to steal information, disrupt systems, or hold data for ransom.
Here are a few of the most common forms of malware attacks I see.
- Viruses: Malicious code that attaches itself to clean files and spreads through the system, often corrupting data or causing operational issues.
- Trojans: Malware disguised as legitimate software to trick users into installing it, creating a backdoor for attackers to access the system.
- Spyware: Software that secretly records a user’s actions, such as keystrokes and browsing habits, to steal sensitive information.
- Ransomware: A particularly nasty form of malware that encrypts a victim’s files. Imagine all your files being locked with a digital key, and the attacker demands payment for its release. That’s a ransomware attack.
3.2. Phishing: The art of digital deception
Phishing is a type of social engineering attack where attackers impersonate a trusted entity to trick victims into revealing sensitive information like passwords, credit card numbers, or personal details. It’s less about hacking code and more about hacking human trust.
While some phishing campaigns are broad, more targeted attacks, known as spear phishing, are tailored to a specific individual or organization for higher success rates. The goal is nearly always credential theft or to deliver malware.
| Warning Phishing emails often create a false sense of urgency, like a password reset request you didn’t initiate, a fake invoice demanding immediate payment, or a notice that your account has been suspended. |
3.3. Denial-of-Service (DoS/DDoS) attacks: Overwhelming the system
The goal of a Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attack isn’t to steal data, but to make a website or online service unavailable to its legitimate users. A DoS attack comes from a single source, while a much more powerful DDoS attack uses a network of compromised computers (a ‘botnet’) to launch the assault from many sources at once.
I like to use a simple analogy: A DDoS attack is like sending thousands of phantom cars to clog a single roadway, preventing legitimate traffic from getting through to its destination.
3.4. Man-in-the-Middle (MitM) attacks: The digital eavesdropper
A Man-in-the-Middle (MitM) attack is a form of digital eavesdropping. The attacker secretly intercepts and potentially alters the communication between two parties who believe they are communicating directly with each other.
This is a common threat on unsecured public networks. For example, an attacker on a public coffee shop Wi-Fi network could position themselves between you and the router to intercept your login credentials when you access your online banking.
Security Tip: I always advise against conducting sensitive transactions like banking or online shopping when connected to unsecured public Wi-Fi. Always look for the padlock icon in your browser and use a VPN if possible.
4. Who are the targets? Attacks on individuals vs. enterprises
Not all cyber attacks are created equal, and the target often determines the motive and method. I’ve worked with both individual users and large corporations, and it’s clear that attackers tailor their strategies based on who they’re after. Understanding this difference can help you recognize the threats most relevant to you.
This table breaks down the typical differences I’ve observed.
| Target | Common Motives | Typical Attack Methods |
|---|---|---|
| Individuals | Financial gain (bank details, credit cards), identity theft, credential harvesting for resale. | Phishing emails, malware delivered via fake downloads, social media scams, smishing (SMS phishing). |
| Enterprises | Data exfiltration (customer data, intellectual property), financial fraud, espionage, operational disruption. | Spear phishing, ransomware, exploiting software vulnerabilities, supply chain attacks, large-scale data breaches. |
5. Anatomy of a major 2024 data breach
To understand how these concepts apply in the real world, let’s dissect a hypothetical but highly realistic major data breach from early 2024. Analyzing these events is a critical part of my job, as it provides invaluable lessons on how to improve our defenses.
5.1. The attack vector and business impact
In this scenario, a large e-commerce company, let’s call it OmniRetail, suffered a significant data breach. The attackers gained initial access via a sophisticated spear phishing email targeting a finance department employee. The email appeared to be a legitimate invoice from a known vendor but contained a malicious macro.
Once the employee opened it, malware was installed, giving the attackers a foothold. Over several weeks, they moved laterally through the network, escalating privileges until they accessed the main customer database.
The consequences were severe: the personal and financial data of over 10 million customers were stolen, leading to massive financial loss, regulatory fines, and irreparable reputational damage. This incident highlights how a single security vulnerability. In this case, human error can lead to a catastrophic system-wide failure.
5.2. Actionable lessons learned for your own security
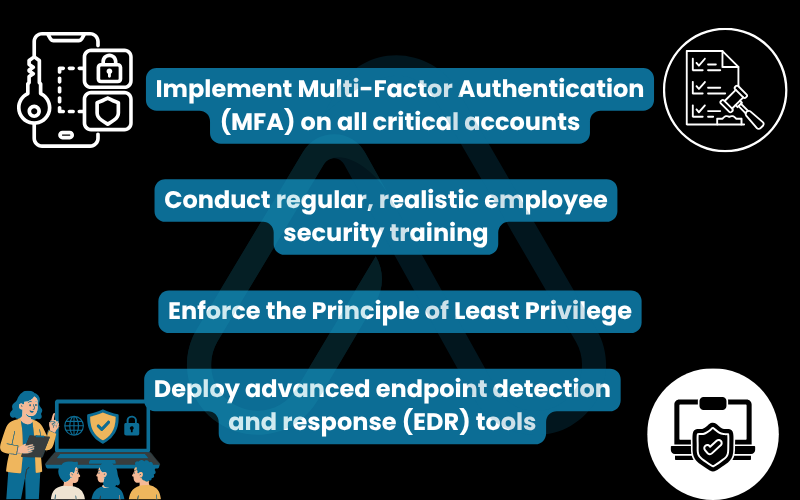
The OmniRetail breach offers critical lessons for both individuals and organizations. Based on my analysis, several key measures could have prevented or significantly mitigated this attack. Here are the most important takeaways.
- Implement Multi-Factor Authentication (MFA) on all critical accounts. Even if the attackers stole the employee’s password, MFA would have served as a powerful second barrier, preventing them from accessing the account.
- Conduct regular, realistic employee security training. Staff are the first line of defense. Training them to identify and report sophisticated phishing attempts is one of the highest-return investments in information security.
- Enforce the Principle of Least Privilege. The compromised employee’s account should not have had access paths to critical databases. Limiting access to only what is necessary for a job function contains the damage if an account is breached.
- Deploy advanced endpoint detection and response (EDR) tools. Modern security software can often detect and block the malicious activity seen in this attack, such as lateral movement and data exfiltration, before significant damage is done.
6. Latest cyber attack trends and statistics for 2025
The cybersecurity landscape is never static. As a technology expert, a huge part of my job is tracking the evolution of threats to provide up-to-date advice. Looking ahead to 2025, several trends are reshaping the nature of cyber attacks, making them more sophisticated and harder to detect.
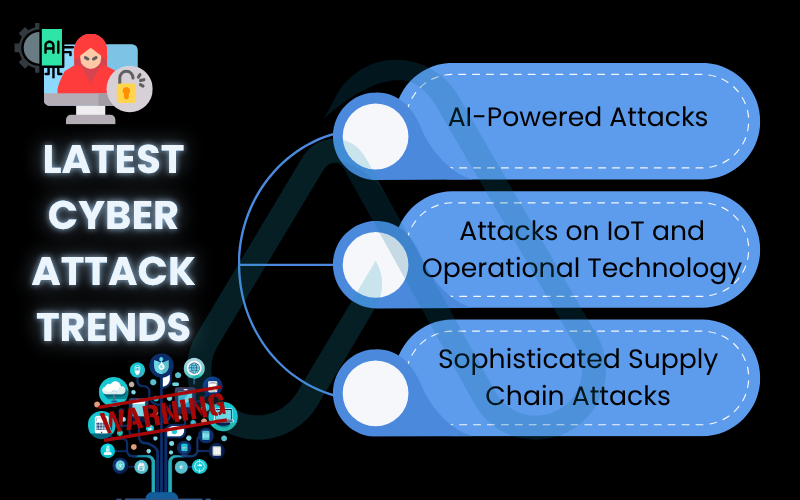
Here are three key trends I’m closely monitoring.
- AI-Powered Attacks: Attackers are now using artificial intelligence to their advantage. This includes creating highly convincing deepfake videos or voice clones for phishing, automating the search for security vulnerabilities on a massive scale, and crafting malware that can adapt and evade detection.
- Attacks on IoT and Operational Technology (OT): The number of connected devices from smart home gadgets (IoT) to industrial control systems (OT) is exploding. These devices are often insecure, creating a massive new attack surface for criminals seeking to cause physical disruption or steal data.
- Sophisticated Supply Chain Attacks: Instead of attacking a well-defended company directly, attackers are targeting their less secure software suppliers. By compromising a single software update, they can push malicious code to thousands of the supplier’s customers at once. I find this trend particularly concerning, as it undermines the trust we place in the software we use daily.
7. How can you protect yourself from cyber attacks?
After learning about all these threats, it’s easy to feel overwhelmed. But the good news is that you can take concrete, powerful steps to protect yourself. I’ve always believed that good information security is about building layers of defense through simple, consistent habits. This section is all about empowering you with the knowledge to do just that.
7.1. Essential security tips for individuals
For personal protection, you don’t need to be a security expert. Focusing on the fundamentals will block the vast majority of attacks I see every day. Here is my essential checklist for every user.
- Use a password manager. It’s the single best thing you can do for your security. A password manager creates and stores strong, unique passwords for every site, so you don’t have to remember them.
- Enable Multi-Factor Authentication (MFA) wherever possible. This adds a crucial second layer of security, usually a code from your phone, that prevents access even if your password is stolen.
- Keep your software updated. Updates often contain critical patches for security vulnerabilities. Turn on automatic updates for your operating system, browser, and applications.
- Be skeptical of unsolicited messages. Whether it’s an email, text, or social media message, be wary of links and attachments, especially if they create a sense of urgency. When in doubt, don’t click.
7.2. Foundational security measures for organizations
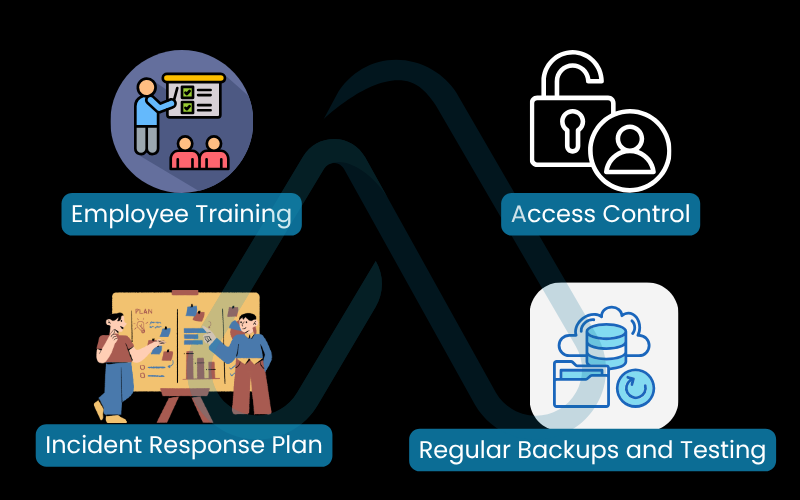
For businesses and organizations, security is a team sport that requires building a strong security culture. Beyond technology, it’s about processes and people. Here are the foundational pillars I recommend every organization build upon to mitigate any cyber threat.
- Employee Training: Your staff is your first line of defense and potentially your weakest link. Regular, engaging training on topics like phishing identification and password hygiene is non-negotiable.
- Access Control: Implement the Principle of Least Privilege. Employees should only have access to the data and systems absolutely necessary for their jobs. This limits the potential damage of a compromised account.
- Incident Response Plan: Don’t wait for an attack to happen to figure out what to do. Have a clear, practiced plan that outlines who to contact, how to contain the breach, and how to communicate with stakeholders.
- Regular Backups and Testing: Maintain regular, isolated backups of critical data. Just as importantly, test your ability to restore from those backups to ensure they’ll work when you need them most.
8. How to react to a cyber attack: Your immediate steps cheat-sheet
Even with the best defenses, an attack can sometimes succeed. In these moments, your immediate actions are critical to containing the damage. If you suspect your device or account has been compromised, the panic can be paralyzing. I’ve created this simple cheat sheet to guide you through the first few crucial steps.
Here is my recommended immediate action plan.
- Disconnect from the Network. (Icon: Wi-Fi disconnect) If you suspect malware on your computer, immediately disconnect it from the internet by turning off Wi-Fi or unplugging the Ethernet cable. This can prevent the malware from spreading or sending your data to the attacker.
- Do Not Turn Off the Machine. This might seem counterintuitive, but turning off your computer can erase volatile memory (RAM) that may contain crucial evidence for forensic investigators.
- Report the Incident Immediately. (Icon: Phone) If this is a work device, contact your IT or security department right away. For personal accounts, contact the service provider (e.g., your bank, email provider) to report the breach.
- Change Your Passwords. From a separate, trusted device, change the passwords for the compromised account and any other accounts that use the same or a similar password. Prioritize critical accounts like email and banking.
- Scan for Malware. Use a reputable antivirus or anti-malware program to scan your device for threats.
9. FAQs about what is cyber attack?
Over my years in this field, I’ve noticed that certain questions come up again and again. To help you build a complete understanding, I’ve answered some of the most common ones here.
What is the goal of a cyber attack?
The main goals include financial gain, data theft (espionage), service disruption, or promoting a political cause.
Can a cyber attack be stopped?
While 100% immunity isn’t possible, the vast majority can be prevented with a resilient, multi-layered defense.
Who is behind cyber attacks?
Perpetrators vary widely, including organized criminals (profit), nation-states (espionage), hacktivists (politics), and insiders
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| DDoS | Distributed Denial-of-Service | An attack that uses many compromised computers to overwhelm a server or network, making it unavailable. |
| DoS | Denial-of-Service | An attack from a single source to make a server or network unavailable. |
| IoT | Internet of Things | A network of physical devices, vehicles, home appliances, and other items embedded with electronics and software that enables them to connect and exchange data. |
| MFA | Multi-Factor Authentication | A security process that requires users to provide two or more verification factors to gain access to a resource. |
| MitM | Man-in-the-Middle | An attack where the attacker secretly intercepts and relays messages between two parties who believe they are communicating directly. |
| OT | Operational Technology | Hardware and software that detects or causes a change through the direct monitoring and/or control of physical devices, processes, and events in the enterprise (e.g., industrial control systems). |
| N/A | Malware | Software intentionally designed to cause damage to a computer, server, client, or computer network. |
| N/A | Phishing | A social engineering attack that uses deceptive emails and websites to trick victims into revealing sensitive information. |
| N/A | Ransomware | A type of malware that encrypts a victim’s files and demands a ransom payment to restore access. |
| N/A | Social Engineering | The psychological manipulation of people into performing actions or divulging confidential information. |
10. Final thoughts
Navigating the digital world of 2025 requires a clear understanding of the threats we face. As we’ve covered, a cyber attack is a deliberate act of intrusion with motives ranging from financial gain to global espionage. The threat landscape is constantly evolving, with new tactics like AI-powered attacks emerging all the time. However, knowledge and proactive defense remain our most powerful tools.
My final advice is to focus on what you can control. Here are the most critical takeaways I want you to remember.
- Understanding is the First Step: Knowing what a cyber attack is, how it works, and who it targets is foundational to your digital safety.
- Basics Matter Most: Simple, consistent habits like using a password manager, enabling MFA, and keeping software updated will protect you from the vast majority of threats.
- Proactive Defense is Critical: Don’t wait to become a victim. Whether you’re an individual or an organization, building layers of security and having a response plan is essential.
- Stay Informed: The threats of today won’t be the threats of tomorrow. Committing to ongoing learning is key to staying ahead of attackers.
In the digital landscape of 2025 and beyond, understanding the nature of cyber attacks is the first and most crucial step toward building a secure future for yourself and your organization. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.


