In a world driven by data, I often hear the term ‘cyber privacy’ used, but many people are unsure what it actually means. So, what is cyber privacy in 2025? It’s not just about hiding things; it’s about control. As we navigate an increasingly digital landscape shaped by new technologies like AI, understanding this concept is crucial for protecting your rights as an individual and your responsibilities as an organization. This guide is built from my decade of experience to give you a clear, practical understanding of modern data protection.
Cyber Privacy Definition:
Cyber privacy, also known as online or digital privacy, is the right of an individual to control how their personal information is collected, used, stored, and shared online. It focuses on the rules and standards governing data handling to ensure fairness, transparency, and user consent.
1. The core principles of modern cyber privacy
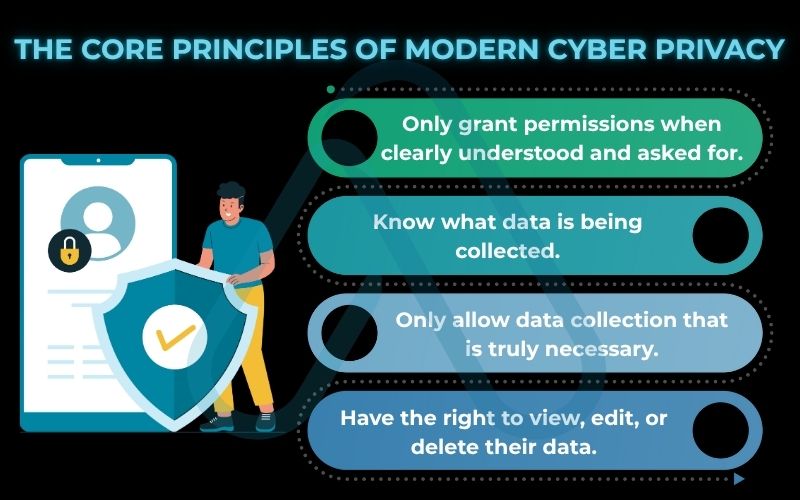
To truly grasp cyber privacy, I find it helps to think of it not as a single action, but as a framework built on four key principles. These principles are the foundation of digital trust. Imagine your personal data is like the valuable contents of a safe deposit box at a bank. For you to trust that bank, you’d expect certain rules to be followed. Here’s how that analogy applies to the digital world:
- Consent: You hold the key to your box. You must give explicit, informed permission before anyone can access or use what’s inside. This means no hidden clauses or automatic opt-ins.
- Transparency: You have the right to know exactly what the bank is storing for you and why. In the digital world, companies must be clear about what data they collect and how they intend to use it.
- Data Minimization: You would only put what’s absolutely necessary into your safe deposit box. Similarly, organizations should only collect the minimum amount of personal data required for a specific, stated purpose.
- User Control: It’s your box, so you should be able to access, change, or remove its contents whenever you want. This translates to your fundamental user rights to view, amend, and delete your personal data held by companies.
2. Understanding the crucial difference between Cyber privacy vs cybersecurity
One of the most common points of confusion I encounter is the mix-up between cyber privacy and cybersecurity. While they are deeply related, they serve different functions. Think of it like a house: Cybersecurity is the lock on your door, the alarm system, and the strong walls that keep intruders out. Cyber privacy is the set of rules about who you invite inside, what rooms they can enter, and what they’re allowed to do while they’re there. Cybersecurity protects the data from external threats, while privacy governs how that data is used correctly and ethically. To make it even clearer, I’ve broken down the distinction in this table:
| Aspect | Cyber Privacy | Cybersecurity |
| Goal | To ensure the ethical and legal use of personal data, focusing on user rights and consent. | To protect data, networks, and systems from unauthorized access, attacks, and damage. |
| Methods | Policies, legal frameworks (like GDPR), transparency reports, and user controls. | Firewalls, encryption, antivirus software, and intrusion detection systems. |
| Scope | Governs how personal information is collected, stored, and shared. It’s about ‘should we’. | Focuses on preventing and mitigating cyber threats. It’s about ‘can we’. |
3. Why cyber privacy matters more than ever in the digital age
Understanding the definition is the first step. Now, let’s explore the high-stakes implications for everyone online. The importance of cyber privacy has grown exponentially, and the consequences of ignoring it have never been more severe for both individuals and organizations.
Did you know? According to recent industry reports, the average cost of a data breach has surpassed $4.45 million, and over 70% of consumers state they are more concerned about their online privacy now than they were a few years ago. This isn’t just an IT issue; it’s a fundamental trust issue.
3.1. Protecting your personal information and digital identity for individuals
Every time you go online, you leave a ‘digital footprint’—a trail of data created by your activities. Without strong cyber privacy practices, this footprint can be exploited by malicious actors. I’ve seen firsthand how a seemingly small data leak can spiral into a major personal crisis. The risks are real and damaging.
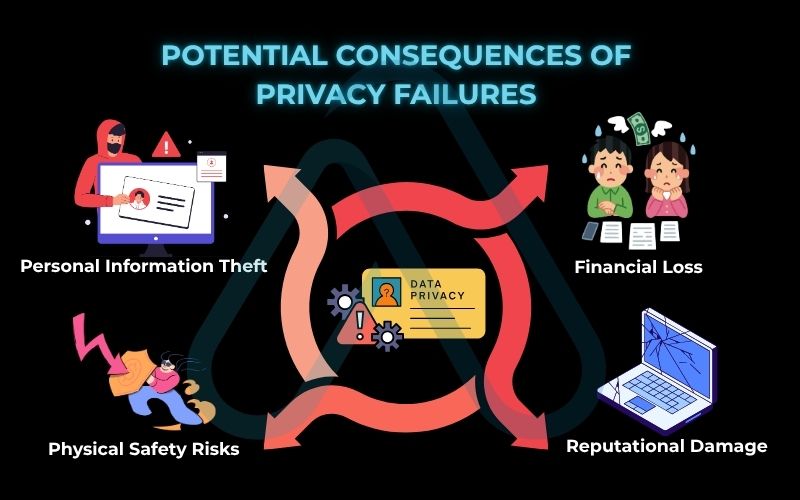
Here are some of the potential consequences of privacy failures you need to be aware of:
- Identity Theft: Cybercriminals can use stolen personal information (like your name, address, or social security number) to open accounts, take out loans, or commit crimes in your name.
- Financial Loss: Leaked financial details can lead directly to drained bank accounts or fraudulent credit card charges.
- Reputational Damage: Private messages, photos, or browsing history, if exposed, can be used for blackmail, public shaming, or to damage personal and professional relationships.
- Physical Safety Risks: The exposure of your real-time location or home address can create serious physical safety concerns from stalking or harassment.
Cyber privacy empowers you to manage that digital footprint, giving you control over who sees your data and how it’s used, thereby mitigating these serious cyber threats.
3.2. Building trust and avoiding costly penalties for organizations
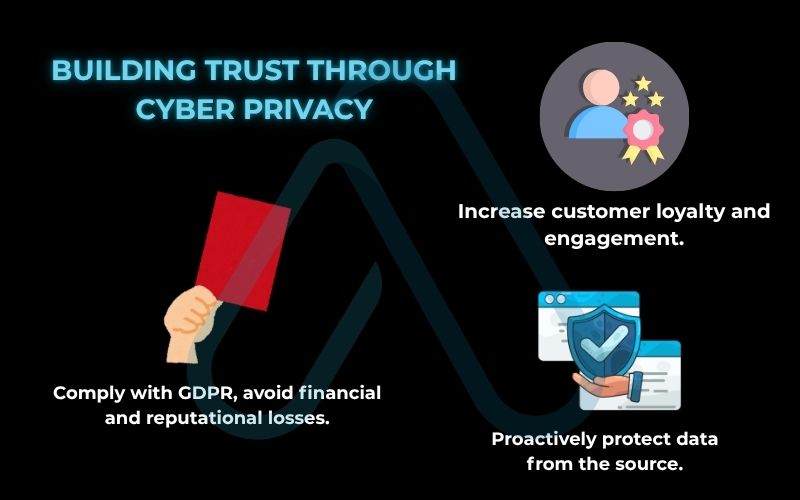
For any small business owner or IT professional I speak with, I stress that cyber privacy is not a legal hurdle, it’s a core business asset. In today’s economy, trust is your most valuable currency. A proactive approach to data protection, often called ‘privacy by design’, can be a significant competitive advantage.
When customers trust you with their data, they are more loyal and more willing to engage with your brand. Conversely, failing to protect that data can be catastrophic. The risks for businesses that neglect cyber privacy are twofold.
First, there’s the immense reputational damage that follows a data breach. News travels fast, and losing customer trust can be impossible to recover from. Second, there are the staggering regulatory fines. Under laws like GDPR, penalties can reach into the millions of euros for non-compliance. These aren’t just threats; they are enforced regularly.
Fulfilling your compliance requirements isn’t just about avoiding penalties; it’s about demonstrating your commitment to your customers’ safety and building a resilient, trustworthy business.
4. The 2025 global privacy landscape: Laws, rights, and regulations
To practice good cyber privacy, you need to understand the rulebook. The digital world is governed by a growing patchwork of laws and regulations that define the rights of individuals and the obligations of organizations. This legal landscape is constantly evolving, making it essential to stay current.
4.1. What’s new? Key data privacy laws and enforcement trends for 2024-2025
While foundational laws like Europe’s GDPR and California’s CCPA/CPRA set the standard, the legislative landscape is far from static. As a technology expert, I’m constantly tracking these changes to understand their impact. The key trend for 2025 is the continued expansion of comprehensive privacy laws at the state and national levels. Here are some of the most significant developments:
- U.S. State-Level Proliferation: Following California’s lead, several other states have enacted their own privacy laws. The Virginia Consumer Data Protection Act (VCDPA) and the Colorado Privacy Act (CPA) are now in full effect, with similar laws emerging in Utah, Connecticut, and beyond. Each has unique requirements, creating a complex compliance map for businesses operating nationwide.
- Stricter GDPR Enforcement: In the EU, regulators are not just creating rules; they’re enforcing them with increasing vigor. We’re seeing a focus on the legal basis for data processing, especially concerning ad-tech and international data transfers. Fines are becoming more common and substantial.
- Emerging Global Regulations: Other countries are rapidly advancing their own global data regulations. Brazil’s LGPD is now fully operational, and India’s proposed Digital Personal Data Protection Bill signals a major shift in one of the world’s largest digital economies.
For any business, it is critical to consult official sources and legal counsel to ensure full compliance with these evolving regulations.
4.2. Comparing key jurisdictions
Navigating these different global data regulations can be daunting. To help you get a quick overview, I’ve created this simplified matrix comparing some of the key features across major privacy laws. This table is a starting point to help you identify your primary compliance requirements.
| Feature / Right | GDPR (EU) | CCPA/CPRA (California) | PIPEDA (Canada) |
| Right to Deletion | Yes (Right to be Forgotten) | Yes | Yes (Right of Erasure) |
| Consent Requirement | Opt-in (explicit consent required before collection) | Opt-out (right to opt-out of sale/sharing of data) | Implied or express consent, depending on sensitivity |
| Data Breach Notification | Mandatory within 72 hours to authorities | Required when specific personal info is compromised | Required if there is a real risk of significant harm |
| Scope | Applies to any organization processing EU residents’ data | Applies to for-profit entities meeting size/processing thresholds | Applies to commercial activities across Canada |
5. Navigating what is new in cyber privacy threats
The privacy rules of the past are not enough for the technology of tomorrow. Here’s what you need to watch out for. As our tools become more advanced, the threats to our personal data become more sophisticated and insidious, moving far beyond simple website trackers.
5.1. How AI and generative models are changing the privacy game
Artificial Intelligence is no longer science fiction; it’s a part of our daily lives, and its impact on privacy is profound. AI models, especially large language models (LLMs) like those behind generative AI, are trained on unimaginably vast datasets. The problem? Those datasets often include personal information scraped from the public internet without consent. This creates a host of new risks that define the challenge of AI privacy.
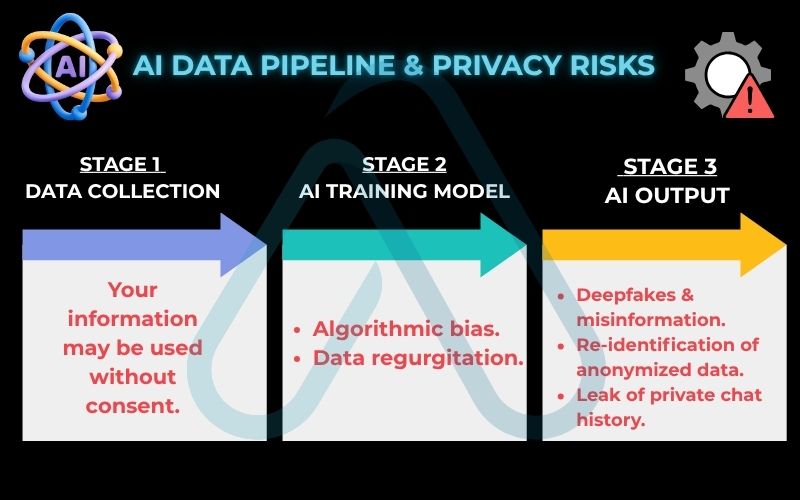
Here’s the data pipeline and its risks:
- Data Collection: Personal data from blogs, social media, and websites is scraped to train AI. The privacy risk is that your information is being used for purposes you never agreed to.
- AI Training Model: The model learns patterns from this data. This can lead to algorithmic bias, where the AI makes prejudiced decisions based on flawed or unrepresentative data. It also creates a risk of ‘data regurgitation’, where the model might inadvertently reveal the personal information it was trained on.
- AI Output: The trained model generates content. This poses risks like the creation of deepfakes for misinformation or harassment and the re-identification of ‘anonymized’ data, where AI can piece together anonymous data points to identify a specific person. I saw a case where a user prompted a chatbot and received another user’s private conversation history—a stark reminder of these new vulnerabilities.
5.2. The next battleground for data protection
As we push the boundaries of technology, we are entering the ultimate frontier of personal data: our own minds. I’m talking about neural privacy, which is the protection of data generated by a person’s brain activity. This data is collected by neuro-technologies like Brain-Computer Interfaces (BCIs), which are becoming more common in medical and even consumer applications.
The implications here are staggering. Unprotected neural data could potentially be used to infer an individual’s thoughts, emotions, political leanings, or intentions without their knowledge or consent.
| Warning: The concept of neural privacy is not a distant future concern. As BCIs and related technologies develop, establishing strong legal and ethical safeguards now is critical. The right to cognitive liberty, the freedom of thought, may depend on it. This is a topic I am following with intense focus, as it represents the most intimate form of data protection we will ever need. |
5.3. IoT, wearables, and smart device risks
Cyber privacy is no longer confined to your computer screen. It’s in your living room, on your wrist, and in your car. The Internet of Things (IoT) has filled our lives with devices that are constantly collecting data. While convenient, each device is a potential privacy vulnerability, creating new vectors for cyber threats.
Consider the sensitive personal information these common devices collect:
- Smart Watch / Fitness Tracker: Collects your heart rate, sleep patterns, daily activity, and precise geolocation data.
- Smart Speaker: Records your voice commands and can capture ambient sounds and conversations in your home.
- Smart TV: Tracks your viewing habits, which can be sold to data brokers to build a detailed profile of your interests.
- Smart Home Security Camera: Captures video and audio from inside and outside your home.
The central privacy question I always ask is: did we provide meaningful consent for this level of continuous monitoring? Often, this data is collected under broad terms of service that few people read, creating a detailed, minute-by-minute profile of our lives that can be easily misused or exposed in a data breach.
6. Recent data breach case studies
Sometimes, the best way to understand the importance of privacy is to see what happens when it fails. By analyzing real-world incidents, we can learn valuable lessons to apply to our own practices. Here are a couple of recent case studies that highlight critical privacy failures.
The Social Media Platform Leak
This case involved a major social media platform where a feature designed to help users find friends inadvertently exposed user data.
- The Incident: A vulnerability in an API allowed malicious actors to scrape the personal phone numbers and linked accounts of over 500 million users. This data was then compiled and sold on cybercrime forums.
- The Privacy Failure: The core issue was a failure of ‘privacy by design’. The feature was built for convenience without fully considering how it could be abused. Furthermore, the data collected was not properly minimized; user phone numbers were retained and accessible long after they were needed for initial verification.
- The Lesson: Convenience should never come at the expense of security. For businesses, this is a clear warning to audit all public-facing APIs and features for potential data scraping abuse. For individuals, it’s a reminder to provide the minimum amount of personal information necessary when signing up for services.
The Healthcare Data Breach
A recent data breach at a large healthcare provider exposed the sensitive health information of millions of patients.
- The Incident: Cybercriminals gained access to the provider’s network through a phishing attack on an employee. Once inside, they were able to access a database containing patient names, diagnoses, and treatment histories.
- The Privacy Failure: While the initial entry was a security failure, the privacy failure was the lack of sufficient internal data segregation and access controls. A single compromised account should not have had access to the entire patient database. Sensitive data was not adequately encrypted at rest, making it easy for the attackers to exfiltrate and read.
- The Lesson: Strong external defenses are not enough. Organizations, especially those handling sensitive data, must implement a ‘zero trust’ model internally. Data should be segmented, and access should be granted on a strict need-to-know basis. This incident underscores the critical link between cybersecurity measures and the protection of privacy.
7. Your actionable cyber privacy framework
Theory is important, but practical action is what truly protects you. Now that you have a firm grasp of what cyber privacy is and why it matters, I want to provide you with an actionable framework. This is the ‘how-to’ section, designed to empower you to take immediate steps to improve your privacy posture.
7.1. A 10-step checklist to protect your privacy online
Here is a practical checklist I’ve developed to help you secure your digital life. Following these steps can dramatically reduce your exposure to common privacy risks.
| Action | Why it matters |
| Use a Virtual Private Network (VPN): A VPN encrypts your internet traffic, hiding your IP address and online activity from your internet service provider (ISP) and others on public Wi-Fi. | It provides a crucial layer of privacy for your day-to-day browsing and enhances your online security. |
| Review and Manage App Permissions: Regularly check the permissions your mobile apps have. Does that game really need access to your contacts and microphone? Revoke any permissions that aren’t necessary for the app’s function. | This stops apps from collecting more personal information than they need, a key principle of data minimization. |
| Use a Privacy-Focused Browser: Switch to browsers like Brave or Firefox that have strong, built-in tracking protection to block third-party cookies and trackers. | It reduces the amount of data that advertisers and data brokers can collect about your browsing habits. |
| Strengthen Your Passwords: Use a password manager to create and store unique, complex passwords for every single online account. Enable two-factor authentication (2FA) wherever possible. | This is your first line of defense against unauthorized account access if one service suffers a data breach. |
| Audit Your Social Media Privacy Settings: Go through the privacy settings on all your social media accounts. Limit who can see your posts, your friends list, and your personal details. | It helps you control your digital footprint and prevents oversharing of sensitive information with the public. |
| Be Wary of Public Wi-Fi: Avoid accessing sensitive accounts (like banking) on unsecured public Wi-Fi networks. If you must, always use a VPN. | Unsecured networks are a prime hunting ground for cybercriminals looking to intercept your data. |
| Limit Data Sharing on Forms: When signing up for a service, only fill out the required fields. Be skeptical of any form asking for unnecessary personal details. | The less data you give away, the less data can be compromised in a breach. |
| Use Aliased or Temporary Email Addresses: Sign up for newsletters or non-essential services with a disposable email address to protect your primary inbox from spam and tracking. | It compartmentalizes your digital identity, making it harder for companies to link your activities across different platforms. |
| Clear Your Cookies and Cache Regularly: Make it a habit to periodically clear your browser’s cookies and cached data to remove stored trackers. | It gives you a cleaner slate and makes it more difficult for websites to track you over long periods. |
| Read Privacy Policies (or Summaries): While tedious, take a moment to understand how a service will use your data before you agree to its terms. Tools exist that can summarize these policies for you. | This is the essence of informed consent knowing what you’re agreeing to before you share your data. |
7.2. A practical compliance decision tree
For small and medium-sized businesses, navigating compliance requirements can seem overwhelming. This simplified decision tree is designed to help you identify your basic obligations and determine your next steps. This is a starting point, not a substitute for legal advice.
Here is a text-based version of the decision-making process:
| Question | If YES | If NO |
| Do you collect, store, or process any personal data from customers, users, or employees? (e.g., names, emails, IP addresses, cookies) | Proceed to Question 2. | Your privacy obligations are minimal, but it’s wise to have a basic privacy statement on your website. |
| Do you have users/customers in jurisdictions with specific privacy laws (GDPR, CCPA/CPRA, etc.)? | You are legally required to comply with those specific regulations. Proceed to Question 3. | You still have a duty of care to protect the data you hold. Focus on core data protection principles like security, transparency, and data minimization. |
| Do you have a clear, public, and easily accessible Privacy Policy? | Proceed to Question 4. | This is your first and most critical step. Your policy must detail what data you collect, why you collect it, how you protect it, and how users can exercise their rights. |
| Do you have a documented process for handling user data requests and a plan for responding to a data breach? | Excellent. Ensure you review and test these plans regularly to keep them effective. | You need to develop these internal procedures immediately. They are core components of most privacy laws. |
| Disclaimer This decision tree is for informational purposes only and does not constitute legal advice. I strongly recommend consulting with a qualified legal professional to ensure your organization is fully compliant with all applicable privacy laws. |
8. The Afdevinfo cyber privacy self-assessment
Ready to see how you stack up? I’ve put together this quick self-assessment to give you a snapshot of your current privacy readiness. Answer the questions honestly to get a sense of your strengths and weaknesses in data protection against modern cyber threats.
For Individuals:
- Do you use the same password for more than one critical account (e.g., email, banking)? (Yes/No)
- Have you reviewed your social media privacy settings in the last six months? (Yes/No)
- Do you use two-factor authentication (2FA) on your primary email account? (Yes/No)
- Do you regularly accept all cookies on websites without reviewing the options? (Yes/No)
- Do you use a VPN when connected to public Wi-Fi? (Yes/No)
For Organizations:
- Do you have an inventory (or ‘data map’) of all the personal data you collect and store? (Yes/No)
- Is your customer-facing Privacy Policy updated to reflect current laws like GDPR/CCPA? (Yes/No)
- Do you provide regular security and privacy training for your employees? (Yes/No)
- Do you have a written incident response plan in case of a data breach? (Yes/No)
- Do you limit employee access to sensitive data on a ‘need-to-know’ basis? (Yes/No)
Scoring Your Results:
- 4-5 ‘Yes’ answers: Excellent! You have a strong privacy posture. Keep staying vigilant and up-to-date on new threats.
- 2-3 ‘Yes’ answers: Good start, but there are clear areas for improvement. Use the checklist in the previous section to address your gaps.
- 0-1 ‘Yes’ answers: Warning. Your current practices put you at high risk. I urge you to prioritize implementing the steps outlined in this guide immediately.
9. FAQs about what is cyber privacy
I’ve gathered some of the most common questions I receive about cyber privacy to provide you with quick and clear answers.
What are my basic rights regarding my personal data online?
You have the rights to access, correct, delete, and transfer your personal data under laws like GDPR.
Can cyber privacy ever be 100% guaranteed?
No. Total privacy isn’t possible, but you can greatly reduce risk through awareness and secure practices.
What are the major challenges of current agriculture?
Current agriculture faces challenges like soil degradation, water scarcity, climate change, and overuse of chemical fertilizers and pesticides. These issues threaten long-term productivity and sustainability.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
| AI | Artificial Intelligence | The simulation of human intelligence in machines, programmed to think and learn. |
| BCI | Brain-Computer Interface | A device that translates neural activity into commands for a computer or machine. |
| CCPA/CPRA | California Consumer Privacy Act / California Privacy Rights Act | A state-level data privacy law in California that grants consumers more control over their personal information. |
| CPA | Colorado Privacy Act | A state-level data privacy law in Colorado. |
| GDPR | General Data Protection Regulation | A comprehensive data protection law in the European Union that governs the processing of personal data. |
| IoT | Internet of Things | A network of physical devices embedded with sensors and software that connect and exchange data over the internet. |
| LGPD | Lei Geral de Proteção de Dados | Brazil’s comprehensive data protection law. |
| PIPEDA | Personal Information Protection and Electronic Documents Act | Canada’s federal privacy law for private-sector organizations. |
| VCDPA | Virginia Consumer Data Protection Act | A state-level data privacy law in Virginia. |
| VPN | Virtual Private Network | A service that creates a secure, encrypted connection over a public network like the internet. |
10. Final thoughts
As we’ve explored, understanding cyber privacy in 2025 is about much more than just a simple definition. It’s a dynamic and critical field that touches every aspect of our digital lives. From the laws that govern data to the emerging challenges posed by AI and neuro-technology, the need for proactive data protection has never been greater. My goal with this guide was to move you from awareness to action, giving you the knowledge and tools to take control.
Here are the most critical takeaways I want you to remember:
- Privacy is Control, Not Secrecy: Cyber privacy is your right to manage how your personal information is used.
- It’s a Team Effort: Cyber privacy protects the data, while cybersecurity defends the systems. You need both.
- The Landscape is Always Evolving: New technologies and laws require constant vigilance and adaptation from both individuals and businesses.
- Action is Essential: Small, consistent steps in managing your settings, permissions, and passwords are the most effective way to protect your digital identity.
Ultimately, managing your cyber privacy is an ongoing practice, not a one-time fix. By staying informed and making conscious choices, you can navigate the digital world with greater confidence and security. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.









