Have you ever felt a chill after an ad for something you only talked about appeared on your screen? That unsettling feeling gets right to the heart of what is the internet privacy and the growing concern around it. In my years as a technology expert, I’ve seen this issue evolve from a niche concern to a mainstream anxiety. Simply put, internet privacy is your right to control how your personal information is collected, used, and shared online. It’s not about being completely invisible (that’s anonymity), but about having authority over your own data.
This guide will not only cover the risks we face today but also look ahead to the new challenges posed by AI and the Internet of Things (IoT), ensuring your personal information security is ready for the future.
“Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.”
Edward Snowden
1. Why internet privacy is so important in 2024
Understanding the importance of internet privacy goes beyond just avoiding creepy ads. It’s about safeguarding the core aspects of your modern life. In 2024, the lines between our physical and digital worlds have blurred, making the protection of our online selves more critical than ever.
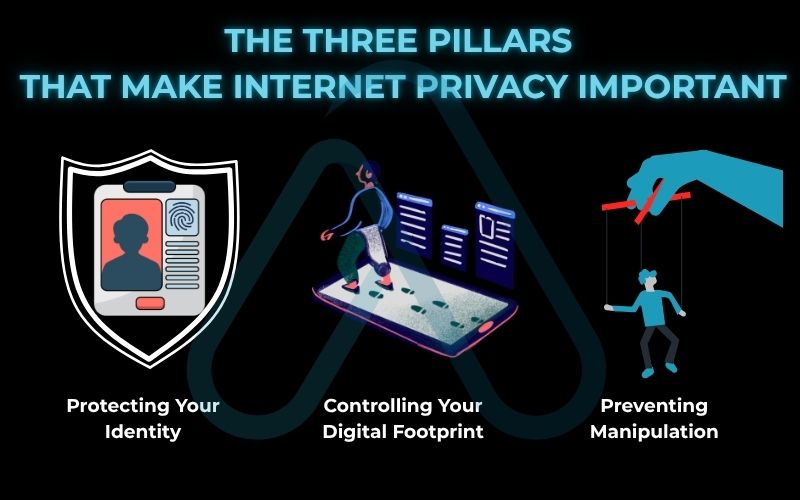
Here are the three pillars that explain why this matters so much:
- Protecting Your Identity: Your personal data, from your date of birth to your location history, is the key to your online identity. When this data is compromised, it can lead to financial fraud, impersonation, and reputational damage. Strong privacy practices are your first line of defense.
- Controlling Your Digital Footprint: Every click, search, and post contributes to your digital footprint. Without privacy controls, this massive trail of data can be used by companies to build detailed profiles about you, influencing everything from the news you see to the prices you’re offered for products.
- Preventing Manipulation: When your habits, beliefs, and vulnerabilities are known, they can be exploited. This isn’t just about targeted advertising; it’s about political campaigns, misinformation, and social engineering designed to influence your decisions and beliefs in ways you may not even realize.
1.1. The crucial difference between online privacy vs. cybersecurity
People often use these terms interchangeably, but they represent two different, yet connected, ideas. I find the easiest way to explain it is with a simple analogy: ‘Cybersecurity is the strong fence around your house. Online privacy is your right to decide who gets to look through your windows.’ They work together to keep you safe.
Here’s a breakdown of how they differ:
| Aspect | Online Privacy | Cybersecurity |
| Goal | To control who can see and use your data. It’s about consent and your rights. | To protect data, devices, and networks from unauthorized access or attack. It’s about defense. |
| Methods | Managing settings, being selective about sharing information, understanding policies. | Using firewalls, antivirus software, strong passwords, and encryption. |
| Real-World Example | Choosing not to share your location with a social media app. | Using a strong, unique password to prevent that social media account from being hacked. |
As you can see, implementing good cybersecurity best practices is fundamental to achieving online privacy. You can’t have privacy if your data isn’t secure.
2. What are the main risks to your internet privacy?
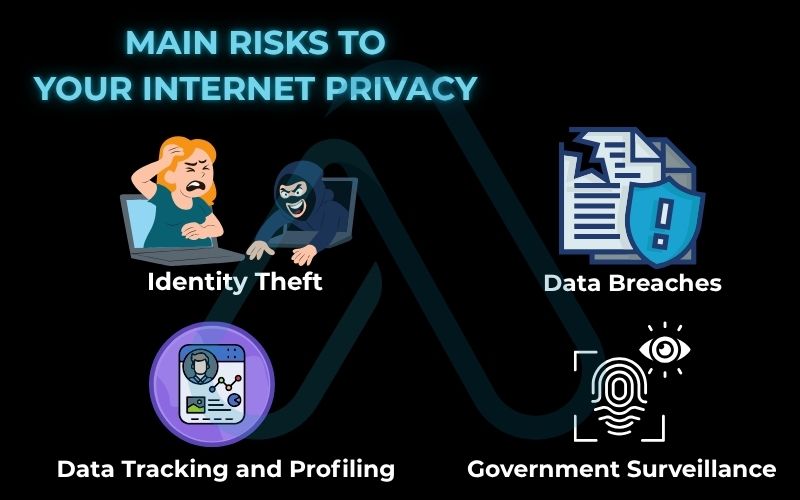
The threats to our digital lives are constantly evolving. Knowing who is collecting your data and how they’re doing it is the first step toward effective data protection. The risks generally come from three sources: corporations seeking to profit, governments conducting surveillance, and criminals aiming to exploit you.
Here are some of the most significant risks you face online:
- Data Tracking and Profiling: Tech giants, advertisers, and data brokers use cookies, trackers, and scripts across websites to monitor your browsing habits. They build a detailed profile of your interests, health, political views, and more to sell products or insights.
- Identity Theft: Cybercriminals use phishing scams, malware, and data breaches to steal your personal information. With enough data, they can open credit cards in your name, file fraudulent tax returns, or access your bank accounts, compromising your personal information security.
- Data Breaches: Sometimes the threat isn’t a direct attack on you, but on a company that holds your data. When a service you use is hacked, your name, email, password, and other sensitive information can be leaked onto the dark web for anyone to buy.
- Government Surveillance: Depending on your location, government agencies may have the authority to collect vast amounts of data on citizens’ online activities, often without their direct knowledge, in the name of national security.
Case study: The 2023 breach that exposed millions
To understand how these risks play out in the real world, let’s look at the 2023 data breach at the genetics company 23andMe. It serves as a stark reminder of how interconnected our data has become.
The Incident:
Hackers used a technique called ‘credential stuffing’, where they took usernames and passwords leaked from other, older breaches and tested them on 23andMe accounts. Because many people reuse passwords, they successfully gained access to thousands of accounts.
The Fallout:
The attackers didn’t just get the data of the breached accounts. They used a feature called ‘DNA Relatives’ to scrape the data of millions of other users connected to those accounts. This exposed highly sensitive ancestral and health-related information, which was then put up for sale online.
Your Takeaway:
This breach highlights two critical lessons. First, reusing passwords is a massive security risk. A breach at one company can compromise your accounts everywhere. Second, even if your own security is perfect, your data is only as safe as the companies you entrust it to. This reinforces the need for both strong personal habits and awareness of company data protection policies.
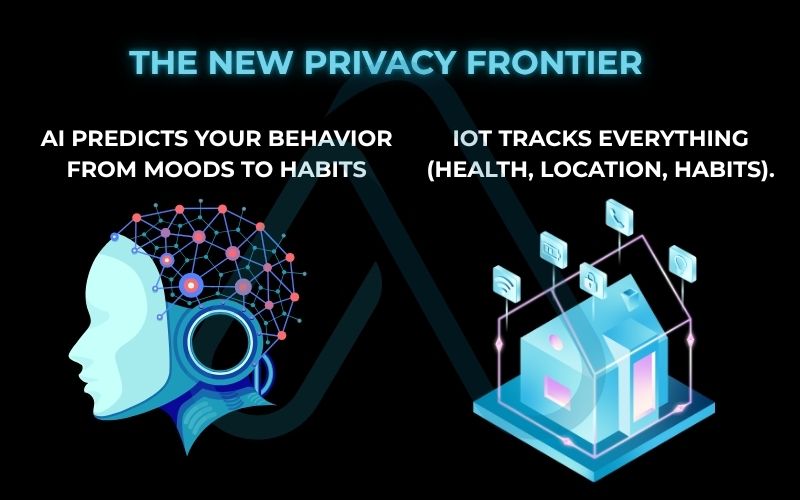
3. The new frontier: How AI and IoT are changing the privacy game
As we look to the horizon, two technologies are fundamentally reshaping the privacy landscape: Artificial Intelligence (AI) and the Internet of Things (IoT). These innovations offer incredible convenience, but I see them as a new frontier for privacy risks that we are only beginning to understand.
Artificial Intelligence (AI) and Predictive Power
AI’s ability to analyze massive datasets creates unprecedented privacy challenges. It’s no longer just about the data you’ve already created; it’s about what AI can predict you’ll do next. Your smart speaker isn’t just listening for ‘Hey Alexa,’ it’s learning the patterns of your life when you wake up, what music you like, the sound of your voice when you’re stressed.
AI can then use this to predict your behavior, purchasing habits, and even your mood. This deep, predictive analysis of your online identity is a goldmine for advertisers and a powerful tool for social control.
The Internet of Things (IoT) and Constant Collection
The IoT puts a sensor in everything from your doorbell and thermostat to your watch and refrigerator. Each of these devices is a data collection point, constantly feeding information about your daily life back to a server. Your smart watch tracks your health and location, your smart TV knows what you watch and when, and your smart fridge could one day track your dietary habits. This creates a persistent, 360-degree surveillance of your private life, making robust data protection more essential than ever.
4. How can I protect my personal information online? A practical guide
Feeling overwhelmed? Don’t be. The good news is that you have the power to significantly improve your privacy. I’ve always believed that empowerment comes from taking small, consistent actions. This section is a practical guide to doing just that, breaking it down into manageable steps.
4.1. Assess your personal privacy risk level
Before you can choose the right tools, you need to understand your own habits and vulnerabilities. I encourage everyone to take a moment for a quick self-assessment. It’s a crucial first step toward better internet privacy.
Ask yourself these questions:
- Do you use the same password for multiple websites?
- Do you click ‘Accept All’ on cookie banners without reading them?
- Do you check app permissions before installing a new app on your phone?
- Is your social media profile public, sharing personal details like your birthday or hometown?
- Do you regularly connect to public Wi-Fi without using a VPN?
Based on your answers, you can start to see where your biggest risks lie. For example, if you answered ‘yes’ to the first question, a password manager should be your top priority. If you often use public Wi-Fi, a VPN is essential. This self-diagnosis helps you focus your efforts where they’ll have the biggest impact.
4.2. Secure your browsing and communications
Your daily web browsing and messaging are primary sources of data leakage. Tightening them up is one of the most effective things you can do.
Here are the steps I recommend:
- Check Browser Privacy Settings: Go into your browser’s settings (like Chrome or Firefox) and look for the ‘Privacy and Security’ section. Here, you can block third-party cookies, send ‘Do Not Track’ requests, and increase your overall protection level.
- Understand Cookies: Think of it this way: First-party cookies help a website remember you (like keeping you logged in). Third-party cookies help other companies follow you across the web. Your goal is to block the latter.
- Always Use HTTPS: Ensure websites you visit have a padlock icon in the address bar. This means your connection to the site is encrypted, preventing your ISP or others on the network from snooping on the content.
- Use Secure Messaging Apps: Switch to messaging apps that offer end-to-end encryption, like Signal or WhatsApp. This ensures only you and the person you’re communicating with can read your messages.

4.3. Manage your digital footprint and social media
Think of your online presence like a garden. It needs regular weeding to stay healthy and private. This means actively managing the information you’ve shared over the years.
Here’s how to start your audit:
- Review Social Media Settings: Go through the privacy settings on each social media account (Facebook, Instagram, X, etc.). Set your profile to private, limit who can see your posts, and remove personal details like your exact birth date and phone number.
- Conduct a Data Audit: Search your own name online to see what’s publicly available. Use services like Have I Been Pwned to check if your email has been part of a data breach.
- Delete Old Accounts: We all have accounts for services we no longer use. These old, forgotten accounts are a security risk. Make a list and take the time to formally delete them, removing your data from their servers.
Your 10-Minute Privacy Audit Checklist:
- Set main social profile to ‘Private’.
- Remove your phone number from public view on social media.
- Review and revoke permissions for third-party apps connected to your Google or Facebook account.
- Delete one old, unused online account.
5. Your privacy toolkit: A comparison of essential services
Taking control of your privacy requires the right tools. I’ve spent years testing and evaluating different services, and I’ve found that a combination of a few key types of software can provide a powerful shield for your digital life. This isn’t about endorsing one brand, but about empowering you to choose what you need for better personal information security.
Here is a comparison of the essential tools that can help you achieve greater internet anonymity and privacy:
| Tool Category | What It Does | Top Examples | Pros | Cons | Best For… |
| VPN (Virtual Private Network) | Encrypts your internet traffic and hides your IP address from your ISP and websites you visit. | NordVPN, ExpressVPN, ProtonVPN | Strong encryption, bypasses geo-restrictions, secures public Wi-Fi. | Can slightly slow down internet speed; requires a paid subscription for best results. | The everyday user, especially those who use public Wi-Fi or want to hide activity from their ISP. |
| Privacy-Focused Browsers | Blocks trackers, ads, and scripts by default to prevent cross-site tracking. | Brave, Firefox (with strict settings), DuckDuckGo Browser | Enhanced default privacy, less data sent to tech giants. | Can occasionally ‘break’ websites that rely heavily on trackers. | The beginner looking for an easy, set-and-forget privacy boost. |
| Password Managers | Creates, stores, and fills in strong, unique passwords for all your online accounts. | 1Password, Bitwarden, Dashlane | Massively improves account security, syncs across devices, secure storage. | Creates a single point of failure if the master password is forgotten or stolen. | Everyone. This is the single most important security tool I recommend. |
| Encrypted Email | Provides end-to-end encryption for your emails, so only you and the recipient can read them. | ProtonMail, Tutanota | Protects sensitive communications from being scanned or read by the provider. | Encryption only works if both sender and receiver use compatible services. | Journalists, activists, or anyone regularly sending sensitive information. |
6. What laws protect your internet privacy?
While personal tools are your first line of defense, government regulation also plays a crucial role. Over the last decade, I’ve watched privacy evolve from a feature to a legally protected right in many parts of the world. These laws give you specific rights over your data.
Here’s a brief overview of the major regulations:
- GDPR (General Data Protection Regulation): This landmark EU law is the global gold standard. It gives consumers rights like the ‘right to be forgotten’ (erasure) and the right to know what data a company holds on them. GDPR compliance is mandatory for any company serving EU citizens.
- CCPA/CPRA (California Consumer Privacy Act / California Privacy Rights Act): Often called ‘America’s GDPR,’ this law gives California residents the right to opt out of the sale of their personal information and request its deletion. It has inspired similar laws in other US states.
- Other Global Laws: Many other countries, including Brazil (LGPD) and Canada (PIPEDA), have enacted their own comprehensive data protection laws, creating a global trend toward greater consumer control.
The key takeaway is that you often have legal rights to control your data. Look for ‘Privacy Policy’ or ‘Do Not Sell My Personal Information’ links on websites to exercise them.
What to watch for
The legal landscape is always changing, and I make it a point to keep a close eye on what’s next. This is a dynamic field, and new challenges are constantly emerging that require new rules.
Here’s what I’m watching on the horizon:
- A US Federal Privacy Law: There is ongoing bipartisan discussion in the US about creating a single, comprehensive federal privacy law to replace the current patchwork of state laws. If passed, this would be a major development for American consumers.
- AI-Specific Regulations: Governments worldwide are grappling with how to regulate artificial intelligence. Future laws will likely address how AI models can be trained on personal data and ensure that automated decisions are fair and transparent.
| Note: This section is updated regularly to reflect the changing legal landscape and ensure you have the most current information. |
7. FAQs about what is the internet privacy?
I get a lot of questions about internet privacy, and many of them are recurring. Here are quick, clear answers to some of the most common ones.
Is incognito mode enough for privacy?
No. It only hides local history. It does not hide you from your ISP, employer, or websites.
Can my ISP see what I do online?
Yes. They can see the sites you visit and when. A VPN is the main way to limit that.
What is a digital footprint?
It’s the trace of everything you do online, both what you post yourself and what is collected about you in the background.
Glossary of key terms
To help you better understand the concepts discussed, I’ve compiled a list of key terms.
| Abbreviation | Full Term | Meaning |
| AI | Artificial Intelligence | The simulation of human intelligence in machines, particularly in learning and problem-solving. |
| IoT | Internet of Things | A network of physical devices (vehicles, home appliances, etc.) embedded with sensors and software that connect and exchange data over the internet. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and routes it through a secure server to hide your IP address and online actions. |
| GDPR | General Data Protection Regulation | A regulation in EU law on data protection and privacy for all individual citizens of the European Union and the European Economic Area. |
| CCPA/CPRA | California Consumer Privacy Act / California Privacy Rights Act | State-wide data privacy laws in California that give consumers more control over the personal information that businesses collect about them. |
| ISP | Internet Service Provider | The company that provides you with access to the internet (e.g., Comcast, Verizon, AT&T). |
| HTTPS | Hypertext Transfer Protocol Secure | The secure version of HTTP, the protocol over which data is sent between your browser and the website you are connected to. It means the connection is encrypted. |
| Phishing | – | A type of cyberattack where attackers impersonate legitimate entities to trick people into revealing sensitive information like passwords or credit card numbers. |
| Malware | Malicious Software | Software intentionally designed to cause damage to a computer, server, client, or computer network. |
| Cookies | – | Small blocks of data created by a web server while a user is browsing a website and placed on the user’s computer or other device by the user’s web browser. |
8. Final thoughts: Taking control of your digital life
Navigating the complexities of internet privacy can seem daunting, but it’s far from a lost cause. As I’ve shown, the risks are real and evolving, particularly with the rise of AI and IoT. However, your awareness and your actions are the most powerful tools you have. Understanding the threats, implementing basic security hygiene, and using the right tools can dramatically shift the balance of power back into your hands.
Remember that perfect privacy is an unrealistic goal; the aim is proactive control. Start today by taking one small step to reclaim your digital autonomy.
Here are the most critical actions you can take right now:
- Install a Password Manager: This is the single biggest security upgrade you can make. Start using it to create unique, strong passwords for every account.
- Review Your Social Media Privacy Settings: Take 10 minutes to go through the settings on your most-used platform and limit what you share publicly.
- Block Third-Party Cookies: Go into your main browser’s settings and block third-party trackers. It’s a simple click that makes a huge difference.
Protecting your privacy is an ongoing journey, not a one-time fix. I hope this guide has empowered you with the knowledge and confidence to take charge of your digital life. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.









