The question “are we under cyber attack?” is no longer just for corporate boardrooms; it’s a valid concern for anyone connected to the internet. With over a decade of experience in cybersecurity, I’ve seen how this uncertainty can cause real anxiety. My goal here is to give you the tools to find the answer for yourself, right now. This guide is structured to provide both a high-level view of the global threat landscape and a practical, personal checklist to assess your own immediate risk.
This guide moves beyond news reports to give you a real-time threat overview and an actionable checklist to assess your own security status.
1. Live cyber attack status dashboard: Today’s global threat level
To understand your personal risk, it helps to first know what’s happening on a global scale. This dashboard provides a summary of the current threat landscape, helping you recognize the most active dangers I’m seeing in the field.
| Note: This dashboard is updated weekly based on public advisories from CISA, NCSC, and major cybersecurity firms. For breaking alerts, I always recommend referring to official sources. |
1.1. Current ransomware activity
Ransomware remains one of the most disruptive threats to both individuals and organizations. Below is a summary of the current ransomware activity I’m tracking.
| Ransomware Strain | Primary Targets | Current Status/Advisory | Recent Example |
|---|---|---|---|
| LockBit 3.0 | Healthcare, Finance, Government | High. Actively exploiting known vulnerabilities. CISA recommends immediate patching. | Disruption of critical services at a major city’s municipal offices. |
| Clop | Education, Technology | Elevated. Known for large-scale data exfiltration attacks. | Exploitation of a zero-day vulnerability in a popular file transfer service. |
1.2. Active phishing and social engineering campaigns
Attackers are constantly refining their lures to trick us into giving up credentials or installing malware. These are some of the most common real-time cyber threat alerts related to phishing that I’m seeing today.
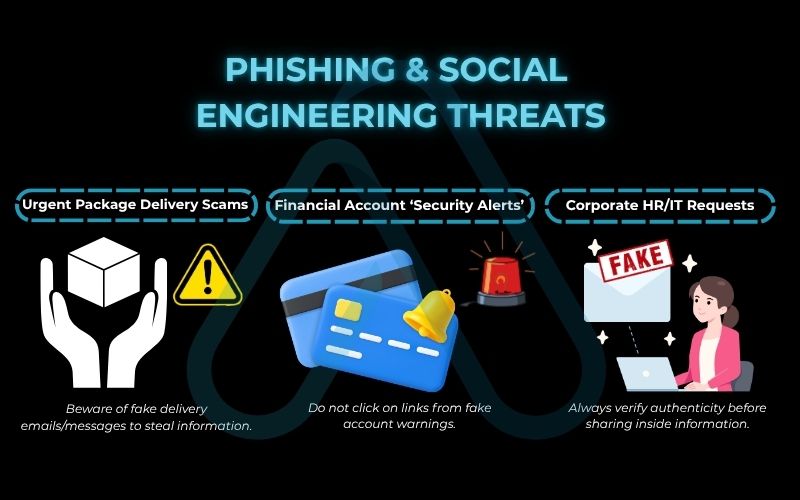
- Urgent Package Delivery Scams: Emails or text messages pretending to be from major couriers (FedEx, UPS, DHL) claim a package is on hold. The link leads to a fake login page designed to steal your credentials.
- Financial Account ‘Security Alerts’: Fake alerts from banks or services like PayPal warn of an ‘unauthorized login’. The goal is to create panic, making you click a malicious link to ‘secure’ your account, but you end up giving the attackers access.
- Corporate HR/IT Requests: These targeted emails mimic internal communications, asking employees to validate their credentials for a system upgrade or to view a new company policy.
1.3. Significant malware and botnet outbreaks
Beyond ransomware and phishing, there are always active malware strains spreading. A malware outbreak today can quickly compromise thousands of systems before it’s contained. Here is a threat profile of a currently active strain.
Threat Profile: Qakbot (or QBot)
Type: Banking Trojan / Malware Dropper
Impact: Initially steals financial information and login credentials. It’s often used as an entry point to deploy more dangerous payloads, including ransomware. It commonly spreads via hijacked email threads, making it look like a reply from a trusted contact, which is a key reason I advise extreme caution with unexpected attachments, even from known senders.
2. A self-assessment workflow about how to know if you are under attack right now
Now, let’s move from the global to the personal. This section is your diagnostic tool to help you detect a cyber attack on your own systems. Go through the following checklists. Seeing one sign may not be a cause for alarm, but multiple signs warrant immediate action. This is your personal cyber risk assessment.
2.1. Personal device and account warning signs
For your personal computer, phone, and online accounts, here are the key warning signs to look for.
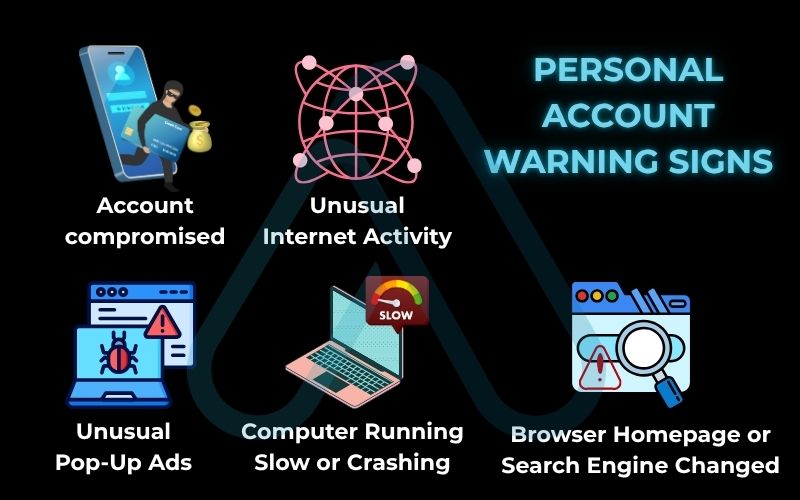
- Is your computer suddenly running extremely slow or crashing? While performance issues can have many causes, a sudden and dramatic slowdown can be a sign that malware is consuming resources in the background.
- Are you seeing an unusual amount of pop-up ads? If pop-ups appear even when your browser is closed, it’s a strong indicator of adware or malware on your system.
- Has your browser homepage or default search engine changed without your permission? This is a classic sign of a browser hijacker, a type of malware that forces traffic to specific websites.
- Are you seeing emails or social media posts from your account that you didn’t send? This is a clear sign your account credentials have been compromised.
- Is your internet activity unusually high? Unexpected network activity is like a stranger using your Wi-Fi, it could be malware communicating with its command-and-control server.
2.2. Business system and network indicators
For my fellow IT professionals and business owners, the indicators of compromise (IoCs) are often more technical. Here are some of the key signals I look for during an investigation.
| Indicator/Symptom | What It Could Mean | Severity |
|---|---|---|
| Unusual outbound traffic on non-standard ports | A compromised system may be communicating with an external server controlled by an attacker. | High |
| Multiple failed login attempts from a single IP | This can indicate a brute-force attack trying to guess passwords for a user account. | Medium |
| Unexpected changes to system files or registry keys | Malware often modifies system settings to ensure it runs every time the computer starts. | High |
| Legitimate admin tools (e.g., PowerShell) used at odd hours | Attackers often use a system’s own tools against it to avoid detection, a technique called ‘living off the land’. | High |
3. Region-specific risk signals and indicators
Cyber threats are not uniform across the globe; different regions face different prevalent attacks based on geopolitics, economic factors, and infrastructure. Here are some regional cyber threats and geo-targeted warnings to be aware of.
3.1. North America
In my experience, this region sees a high volume of ransomware attacks targeting critical infrastructure, healthcare, and state and local governments.
- Primary Threat: Sophisticated ransomware campaigns.
- Regional Agency: The Cybersecurity and Infrastructure Security Agency (CISA) in the United States.
3.2. Europe
Data privacy is a major focus, so phishing campaigns aimed at stealing personal data to bypass GDPR protections are very common. State-sponsored espionage is also a significant concern.
- Primary Threat: GDPR-themed phishing and state-sponsored attacks.
- Regional Agency: The European Union Agency for Cybersecurity (ENISA).
3.3. Asia-Pacific (APAC)
This region often sees a high prevalence of mobile malware and attacks targeting the financial and technology supply chains.
- Primary Threat: Mobile malware and supply chain attacks.
- Regional Agency: National CERTs (e.g., JPCERT/CC in Japan, CERT-In in India).
4. What recent cyber attacks should I be aware of?
Learning from the latest cyber attacks is one of the best ways to understand current attacker tactics. Here are a few case studies that I believe offer valuable lessons for all of us.
| Case Study: The MOVEit Transfer Breach | Case Study: The MGM Resorts Ransomware Attack | |
| The attack | A vulnerability was discovered in a popular file transfer software used by thousands of companies worldwide. The Clop ransomware gang exploited this weakness to steal massive amounts of data from hundreds of organizations before the vulnerability was even publicly known. | Attackers reportedly used social engineering, tricking an IT help desk employee into giving them access. From there, they deployed ransomware that crippled hotel operations, from slot machines to room keys. |
| The impact | Millions of individuals had their personal information stolen, including social security numbers and financial data. | The company suffered massive financial losses and significant reputational damage. |
| The takeaway for you | This was a supply chain attack. It shows that your security is not just about what you do, but also depends on the security of the software vendors you trust. Always apply security patches immediately. | The human element is often the weakest link. This highlights the critical importance of multi-factor authentication (MFA) and employee training to spot social engineering attempts. |
5. Your rapid response guide: What to do in the first hour
If you suspect you’re under attack, the actions you take in the first 60 minutes are critical. The goal is to contain the damage. Here are the immediate steps you should take if you suspect a cyber attack.
5.1. If you’re an individual, you should contain the damage
If you believe your personal computer has been compromised, follow these steps methodically.
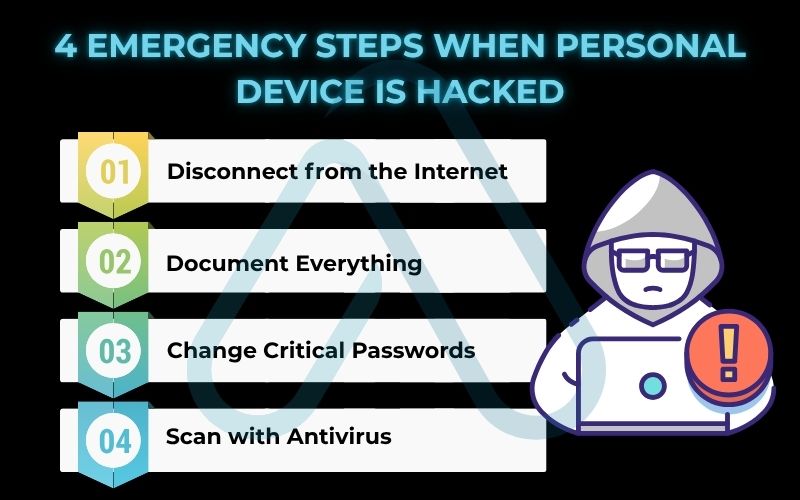
- Disconnect from the Internet: Immediately unplug the ethernet cable or turn off the Wi-Fi on the affected device. This cuts the attacker’s connection.
- Document Everything: Take photos of any strange messages or screen behavior with your phone. Note down the time you first noticed the issue.
- Change Critical Passwords: From a separate, trusted device (like your smartphone on cellular data), change the passwords for your most important accounts: email, banking, and social media.
- Scan with Antivirus: Run a full system scan using a reputable antivirus program.
| DO NOT turn off the machine unless instructed by a professional. Memory data can be crucial for investigation. |
5.2. If you’re an organization, you should activate your incident response plan
For a business, a structured response is essential. If you have an Incident Response (IR) plan, activate it now. If you don’t, here are the universal first steps.
- Isolate Affected Systems: Disconnect the compromised computers, servers, or network segments from the rest of the network to prevent the threat from spreading.
- Preserve Evidence: Do not wipe or reboot machines indiscriminately. This can destroy crucial evidence that will be needed for forensic analysis.
- Escalate Communication: Immediately inform your IT/security lead, management, and legal counsel. Depending on the situation, you may also need to contact your cyber insurance provider.
- Secure Backups: Verify that your backups are secure, isolated, and have not been compromised.
Here is a quick reference for who to contact:
- IT/Security Lead
- Legal Counsel
- Cyber Insurance Provider
- PR/Communications
6. FAQs about are we under cyber attack?
I’ve gathered some of the most common questions I receive about cyber attacks and ways to protect you from attacks.
What are the first signs of an ongoing cyber attack?
Sudden slowdown, unexpected pop-ups, strange account activity, or unusual network traffic.
Who is being targeted by cyber attacks right now?
Everyone via broad phishing, but healthcare, finance, and critical infrastructure are the top targeted sectors.
Can a cyber attack affect my phone as well?
Yes. Common signs are fast battery drain, high data usage, and unfamiliar apps.
How can I check if my data has been exposed in a past breach?
Use Have I Been Pwned if exposed, change your password immediately.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
|---|---|---|
| 2FA | Two-Factor Authentication | A security process where users provide two different authentication factors to verify themselves. |
| APAC | Asia-Pacific | A geographic region that includes East Asia, South Asia, Southeast Asia, and Oceania. |
| CERT | Cyber Emergency Response Team | An expert group that handles computer security incidents. |
| CISA | Cybersecurity and Infrastructure Security Agency | A U.S. federal agency responsible for cybersecurity and infrastructure protection. |
| ENISA | European Union Agency for Cybersecurity | The EU’s agency dedicated to achieving a high common level of cybersecurity across Europe. |
| IoC | Indicator of Compromise | A piece of forensic data, like a file hash or IP address, that indicates a security breach has occurred. |
| IR | Incident Response | An organized approach to addressing and managing the aftermath of a security breach or cyberattack. |
| Malware | Malicious Software | Software specifically designed to disrupt, damage, or gain unauthorized access to a computer system. |
| Phishing | N/A | A type of social engineering attack used to steal user data, including login credentials and credit card numbers. |
| Ransomware | N/A | A type of malware that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid. |
| Smishing | SMS Phishing | A phishing cybersecurity attack carried out over mobile text messaging. |
6. Final thoughts
Navigating the digital world can feel intimidating, but my goal with this guide was to replace that anxiety with awareness and action. Understanding the current threat landscape is your first line of defense, and knowing how to check for signs of compromise on your own systems empowers you to protect yourself. Staying informed and prepared are your best defenses against any cyber attack.
Here are the most critical takeaways I want you to remember:
- Stay Aware: Use the global threat dashboard as a regular check-in to understand what types of attacks are currently active.
- Trust Your Gut: The self-assessment checklists are your personal diagnostic tools. If something feels wrong with your device or account, investigate it.
- Prepare for the Worst: Have a plan. Know the first steps to take whether you’re an individual or an organization. Your actions in the first hour matter most.
Bookmark this page as your go-to resource for monitoring cyber threats. Proactive awareness is your strongest shield. For more in-depth guides, explore our Online Security & Privacy categories on Afdevinfo.









