Ever feel like your smartphone is listening to your conversations? You’re not just paranoid. In my decade of experience in cybersecurity, I’ve seen the feeling of being watched grow from a niche concern to a mainstream reality. This guide is my answer to the crucial question of how can you protect your privacy online. We’re going beyond the basic tips to build a personalized, forward-looking strategy that puts you back in control.
We’ll start with the foundational mindset, move to a 15-minute security checklist, dive deep into browser settings, reclaim your data from brokers, and even tackle the new privacy frontiers of AI and smart devices.
According to recent studies, over 80% of consumers feel they have little to no control over the data companies collect about them. It’s time to change that.
In this guide, you’ll learn:
- How to assess your current privacy risk level and develop strong “digital hygiene.”
- A 15-minute checklist to instantly boost your online security with 2FA, password managers, and updates.
- How to configure browsers and extensions to block online tracking.
- The right way to opt out of data brokers and exercise your privacy rights.
- Essential privacy tools VPNs, encrypted email, and messaging apps and how to use them safely.
- How to secure your AI chats, smart home devices, and social media profiles.
- Simple daily habits to make privacy protection part of your digital routine.
1. Your first and best line of defense
Before we touch a single setting, let’s talk about the most powerful privacy tool you have: your own judgment. The best software in the world can’t protect you if you willingly give your data away. That’s why I always start by helping people develop what I call ‘digital hygiene’, a proactive and conscious approach to their online life.
This is about fostering a habit of ‘conscious sharing’ and performing a quick personal risk assessment before you click, post, or sign up for a new service. Technology is just a tool; your decisions are what truly form the foundation of your online identity protection. Think of it less as a set of rigid rules and more as a simple, reflexive habit that safeguards your digital self.
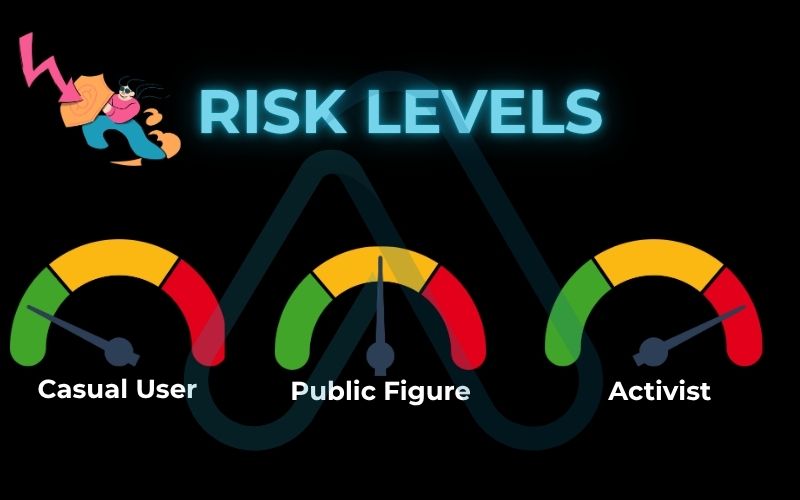
1.1. What’s your personal privacy risk level?
Your privacy needs aren’t the same as your neighbor’s. To figure out what to protect, you first need to understand who you are online and what your personal risks are. Let’s find your profile by asking a few simple questions.
To find your privacy profile, ask yourself these three questions:
- What data am I trying to protect? (e.g., my location, my browsing habits, my private conversations)
- Who am I trying to protect it from? (e.g., advertisers, strangers, an ex-partner, government agencies)
- What is the consequence if this data is exposed? (e.g., annoying ads, public embarrassment, identity theft, physical danger)
Based on your answers, you likely fall into one of these general profiles:
The Casual User
Your primary goal is to reduce tracking from advertisers, prevent spam, and keep your personal accounts secure from common cybercriminals. Your risk is generally low, but foundational security is key.
The Public Figure
Whether you’re an influencer, a business owner, or just have a large online following, your personal information is at higher risk of being targeted. You need to protect against doxxing, stalking, and reputational damage.
The Activist or High-Risk Individual
For journalists, activists, or those in sensitive professions, privacy is paramount for personal safety and the safety of your contacts. You need to protect against sophisticated tracking and state-level surveillance.
2. Your 15-minute privacy checklist
Now that you have the right mindset, let’s lock down the basics. These are the non-negotiable, low-hanging fruit of online privacy. Spending just 15 minutes on these steps will give you the biggest security boost for the least amount of effort. Think of this as building the walls of your digital fortress.
Here are the essential steps I recommend everyone take to protect their privacy online right now:
- Enable Two-Factor Authentication (2FA) Everywhere: This is your single most effective defense against unauthorized account access.
- Use a Password Manager: Create and store strong, unique passwords for every single account without having to remember them.
- Keep Your Software and Apps Updated: Install security updates as soon as they are available to patch critical vulnerabilities.

2.1. Enable two-factor authentication (2FA) everywhere
In simple terms, two-factor authentication (2FA) means you need two things to log in: something you know (your password) and something you have (your phone or a physical key). It’s like needing both a key and a PIN code to open a safe. Even if a hacker steals your password, they can’t get into your account without that second factor. It’s a game-changer for account security.
Here are guides to enable it on major platforms:
| Pro Tip An authenticator app (like Google Authenticator or Authy) is more secure than receiving codes via SMS text message. SMS can be intercepted through SIM-swapping attacks. |
2.2. Use a password manager
If you’re still using ‘Password123’ or reusing the same password across multiple sites, you’re leaving the door wide open for attackers. A password manager is an encrypted digital vault that securely stores all your passwords. I know what you might be thinking: ‘Isn’t it risky to keep all my passwords in one place?’ It’s a valid concern, but these tools are protected by strong, military-grade encryption. As long as you protect your one master password, it’s vastly more secure than any other method.
The core benefits are simple and powerful:
- Generate unbreakable passwords: Create long, random passwords like `8#k&2jP!z@qG` for every site.
- Secure storage: All your passwords are encrypted and stored in one secure place.
- Auto-fill convenience: The manager automatically fills in your login details, saving you time.
Trusted options I often recommend to start with include Bitwarden (great free tier) and 1Password (excellent user experience).
2.3. Keep your software and apps updated
Those constant update notifications might seem annoying, but they are one of your most critical lines of defense. Updates don’t just add new features; they often contain vital security patches that fix vulnerabilities discovered by researchers. Leaving your software outdated is like leaving a known broken window in your house. The best habit you can develop is to enable automatic updates whenever possible.
Here’s how to enable them on major platforms:
- [Windows Icon] Windows: Go to Settings > Update & Security > Windows Update > Advanced options, and ensure ‘Automatic’ is on.
- [macOS Icon] macOS: Go to System Settings > General > Software Update, click the (i) icon next to Automatic updates, and turn on all options.
- [iOS Icon] iOS/iPadOS: Go to Settings > General > Software Update > Automatic Updates, and turn on ‘Download iOS Updates’ and ‘Install iOS Updates’.
- [Android Icon] Android: App updates are typically managed via the Google Play Store. Open Play Store > Profile > Settings > Network Preferences and set ‘Auto-update apps’ to ‘Over Wi-Fi only’.
3. Taking control of your browser: How to prevent online tracking
Every time you browse the web, you leave behind digital breadcrumbs. Companies use these breadcrumbs cookies, tracking pixels, and your browser’s unique ‘fingerprint’ to build a detailed profile of your interests, habits, and life. This section will show you how to prevent companies from tracking your online activity through better browser settings and a few essential tools. Effective data tracking prevention starts right here.
3.1. Choose and configure a secure browser
Your web browser is your main gateway to the internet, and not all gateways are created equal. While you can improve the privacy settings of any browser, starting with a secure browser built for privacy is the best-case scenario. My recommendation follows a ‘Good, Better, Best’ hierarchy.
Here is a simple comparison of popular choices:
| Browser | Key Privacy Feature | Best For |
| Good: Chrome/Edge | Large extension library; can be hardened with the right settings. | Users who need compatibility but are willing to manually adjust settings. |
| Better: Firefox | Enhanced Tracking Protection is strong by default and highly customizable. | Users who want a great balance of privacy, customization, and performance. |
| Best: Brave | Blocks trackers and ads by default with its ‘Shields’ feature. | Users who want maximum privacy and security out-of-the-box with minimal setup. |
If you stick with Chrome, I strongly advise you to go into `Settings > Privacy and security` and turn on ‘Send a “Do Not Track” request’ and set ‘Third-party cookies’ to ‘Block third-party cookies’.
3.2. Install essential privacy extensions
Extensions can supercharge your browser’s privacy capabilities. However, be careful installing too many extensions, or extensions from untrusted sources, can create new security risks. I recommend sticking to a small, powerful, and well-vetted list. For over 99% of users, this core trifecta is all you need.
Here are my top recommendations:
- uBlock Origin: This is more than an ad blocker; it’s a wide-spectrum content blocker that stops ads and tracking scripts at the source, making your browsing faster and more private. [Get it here]
- Privacy Badger: Developed by the Electronic Frontier Foundation (EFF), this extension automatically learns to block invisible trackers that follow you across the web. [Get it here]
- HTTPS Everywhere: Another tool from the EFF, this extension ensures your connection to websites is encrypted whenever possible, protecting you from snooping on public Wi-Fi. [Get it here]

4. Reclaiming your data: Opting out and exercising your rights
So far, we’ve focused on defense blocking new tracking. Now it’s time to go on offense and remove the data that’s already out there. This is a critical step that many guides miss. We’ll cover how to opt out of data brokers and how to use privacy laws to your advantage.
4.1. How to remove your data from people-search sites (data brokers)
Data brokers, also known as people-search sites, are companies that scrape public records, social media, and purchasing data to create detailed profiles about you, your address, phone number, relatives, and more and then sell it. Getting your information off these sites is tedious but essential for your privacy.
Here is a starter guide for a few of the biggest data brokers:
- Whitepages: Go to their opt-out page, find your profile, and follow the steps to request removal. You’ll need to verify your identity via a phone call.
- Spokeo: Go to their opt-out page, search for your profile, and submit the URL for removal. You’ll need to confirm via an email link.
- BeenVerified: Go to their opt-out page, search for your name, and submit your removal request.

For those who find this process overwhelming, paid services like DeleteMe or Incogni can automate these removal requests for you.
| Important Removing your data from brokers is not a one-time task. They often re-add your profile, so I recommend checking back every 6-12 months to repeat the process. |
4.2. A practical guide to submitting a Data Subject Access Request (DSAR)
Privacy laws like Europe’s GDPR (General Data Protection Regulation) and California’s CCPA (California Consumer Privacy Act) give you powerful rights, including the right to see what data a company has on you (a DSAR) and the right to request its deletion (the ‘right to be forgotten’).
Submitting one is easier than it sounds. You can typically find a ‘Privacy’ or ‘Data Request’ link in a website’s footer. If not, you can email their privacy officer (often privacy@company.com). For example, if you wanted to request your data from a social media platform, you could send them an email like this.
Here is a simple template you can adapt:
Subject: Data Subject Access Request
To Whom It May Concern,
Pursuant to my rights under applicable data privacy laws (such as GDPR or CCPA), I hereby request a copy of all personal data you hold about me.
My account information is as follows:
Name: [Your Full Name]
Email: [Your Email Address]
Username: [Your Username]
Please provide this information to me in a portable, machine-readable format within the legally mandated timeframe.
Thank you,
[Your Name]5. The modern privacy toolkit: A comparison of essential tools
To navigate the modern web safely, you need the right tools for the job. This section provides a clear, use-case-based comparison of the most important privacy tools: VPNs, encrypted messaging apps, and secure email. This will help you answer the question, ‘What are the safest tools for secure browsing and messaging?’.
I’ve summarized the key details in this table:
| Tool Category | What It Does | Top Recommendatios | Use Case | Typical Cost |
| VPN | Hides your IP address and encrypts your internet traffic. | ProtonVPN, Mullvad | Securing your connection on public Wi-Fi; preventing your ISP from seeing your activity. | $5-12/month |
| Encrypted Messaging | Uses end-to-end encryption so only you and the recipient can read messages. | Signal, WhatsApp | Secure, private conversations that can’t be read by the service provider. | Free |
| Encrypted Email | Encrypts your emails so the email provider cannot scan their contents. | ProtonMail, Tutanota | Protecting sensitive email communications from third-party scanning and data breaches. | Free to $10/month |
5.1. Virtual Private Networks (VPNs)
A Virtual Private Network (VPN) creates an encrypted tunnel for your internet traffic. This hides your online activity from your Internet Service Provider (ISP) and masks your IP address, which is like your home address on the internet. It’s crucial when using untrusted networks like coffee shop Wi-Fi. However, a VPN does not make you anonymous. Websites can still track you via cookies and account logins.
When choosing a VPN, I always look for two non-negotiable features: a strict no-logs policy (they don’t record your activity) and a kill switch (which cuts your internet if the VPN disconnects).
5.2. Encrypted messaging apps
Standard SMS text messages are not secure. Your cell carrier can see them. In contrast, encrypted messaging apps use something called end-to-end encryption. This means the message is scrambled on your device and can only be unscrambled on the recipient’s device.
Apps like Facebook Messenger may offer it as an option, but for true privacy, I recommend apps like Signal where it’s the default and mandatory setting for all communication. For secure and private conversations, using one of these apps is a must.
5.3. Encrypted email services
Major free email providers like Gmail often scan the content of your emails to serve you targeted ads. Encrypted email services are designed so that not even the company can read your emails. They are stored on the server in an encrypted format that only you have the key to.
If you regularly send sensitive information via emai, financial documents, legal contracts, or personal health information. I strongly recommend using a service like ProtonMail or Tutanota.
6. Privacy for AI and smart devices
Our world is now filled with AI assistants and internet-connected (IoT) devices. These technologies present unique privacy challenges that older guides don’t cover. My philosophy isn’t to avoid this tech, but to use it smarter and with a clear understanding of the data you’re giving up.
6.1. AI chatbots and your data (e.g., ChatGPT)
When you chat with an AI model like ChatGPT, your conversations are often saved and may be reviewed by human trainers to improve the system. It’s critical to treat these chats as semi-public conversations. You can, and should, manage this data. On OpenAI’s platform, you can go into your settings to delete your chat history and opt-out of having your data used for future training. You can find these controls on OpenAI’s data controls page.
| Warning: Never share this information with a public AI chatbot – Passwords, social security numbers, or financial details – Private medical information – Confidential work or business data – Secrets you wouldn’t want to be made public |
6.2. Securing your smart home and IoT devices
Smart speakers, cameras, doorbells, and even light bulbs can pose a privacy risk. They can listen for wake words, record video, and track your daily routines. Locking down your smart home is just as important as securing your computer.
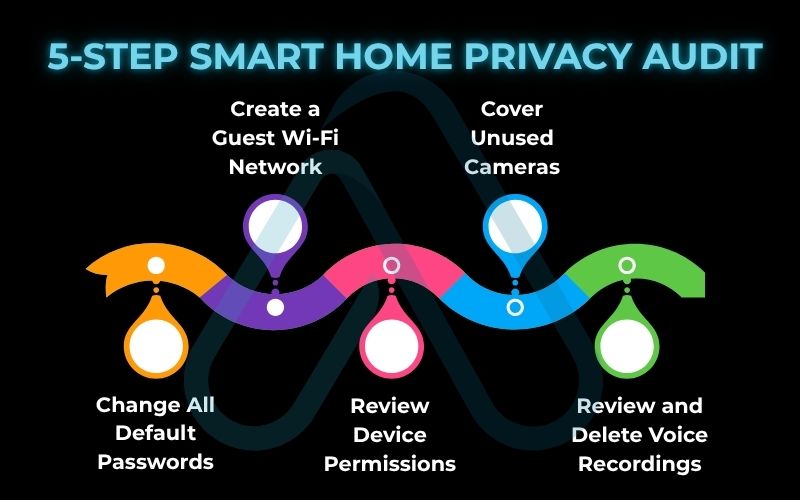
Here is a simple checklist for your 5-step smart home privacy audit:
- Change All Default Passwords: This is the #1 rule. Default passwords are often publicly known and easily hacked.
- Create a Guest Wi-Fi Network: Put all your IoT devices on a separate guest network. If one is compromised, it can’t infect your main computer or phone.
- Review Device Permissions: Go through your smart device apps and turn off any unnecessary microphone, camera, or location permissions.
- Cover Unused Cameras: A simple piece of tape over a laptop or smart display camera is a foolproof way to ensure it’s not watching when you don’t want it to.
- Review and Delete Voice Recordings: Both Amazon and Google allow you to review and delete your voice command history. I recommend doing this periodically. You can manage your history here: Amazon Alexa Privacy Hub and Google Assistant Activity Controls.
7. Social media privacy lockdown: Securing your public profile
Social media platforms are designed for sharing, but you have significant control over what you share and with whom. Taking the time to perform a privacy checkup is one of the most important things you can do to protect your digital identity. The core principles are to limit your audience, control who can tag you, and regularly prune third-party app connections.
7.1. Key settings to check on Facebook, Instagram, and X
While the exact location of settings can change, the core functions are similar across platforms. I recommend you open your favorite social app right now and check these settings.
Here are the most critical settings to look for on each platform:
Facebook:
- Privacy Checkup: Use this guided tool to review who can see your posts.
- Limit Past Posts: A powerful one-click tool to change all your old public posts to ‘Friends only’.
- Timeline and Tagging: Set this to ‘On’ so you must approve any post you’re tagged in before it appears on your timeline.
- Apps and Websites: This is crucial. Remove any old apps or games you no longer use that have access to your data. [Placeholder for screenshot]
- Off-Facebook Activity: Review the list of businesses sharing data about you with Facebook and clear your history.
Instagram:
- Private Account: This is the simplest and most effective setting. If enabled, only followers you approve can see your posts and stories.
- Story Controls: Limit who can reply to and share your stories.
- Activity Status: Turn this off to prevent others from seeing when you were last active.
X (formerly Twitter):
- Protect your Posts: This makes your account private, so only your followers can see your posts.
- Photo Tagging: Change this from ‘Anyone can tag you’ to ‘Only people you follow can tag you’ or turn it off completely.
- Location Information: Disable the ability to add location information to your posts.
8. The ‘Should I share this?’ interactive decision flow
The goal of the privacy mindset is to internalize a thought process that happens automatically before you share something. To help build that habit, I’ve created this simple decision-making flow. The next time you’re about to post, run through these questions in your head.
Text-Based Decision Flow:
Do I truly need to share this information?
If No -> Stop.
If Yes -> Proceed to 2.
Who will be able to see this, both now and in the future? (Think: friends, public, the platform itself, data miners)
If you are not comfortable with the audience -> Stop or find a more private way.
If you are -> Proceed to 3.
How could this information be misinterpreted or used against me? (Think: job prospects, personal relationships, legal issues)
If the risk is too high -> Stop.
If the risk is acceptable -> Proceed to 4.
Am I okay with this being effectively permanent? (Assume everything online can be saved and resurfaced)
If No -> Stop.
If Yes -> Proceed to 5.
Is there a more private way to share this? (e.g., a direct message instead of a public post)
If Yes -> Use the more private method.
If No -> You have made a conscious decision to share.
9. FAQs about how can you protect your privacy on the internet
Here are answers to some of the most common questions I get about online privacy. These provide quick, direct answers and link back to more detailed sections of this guide.
Is ‘private browsing’ or ‘incognito mode’ enough to protect my privacy?
No. It only clears local history and cookies; your ISP, employer, and websites can still see your activity. Use a VPN for stronger privacy.
Can a VPN make me completely anonymous online?
No. A VPN hides your IP and encrypts traffic but can’t stop tracking through cookies, logins, or fingerprinting.
Do I really need to worry about privacy if I have nothing to hide?
Yes. Privacy is about control, not secrecy. It protects you from data misuse, fraud, and manipulation.
Glossary of key terms
| Abbreviation | Full Term | Meaning |
| 2FA | Two-Factor Authentication | A security method requiring two forms of identification to access an account. |
| CCPA | California Consumer Privacy Act | A California state law that gives consumers more control over the personal information that businesses collect about them. |
| Data Broker | N/A | A company that collects personal information about consumers and sells it to other organizations. |
| DSAR | Data Subject Access Request | A formal request made by an individual to a company to see what personal data the company holds about them. |
| End-to-End Encryption | N/A | A secure communication method that prevents third parties from accessing data while it’s transferred from one device to another. |
| Fingerprinting | Browser Fingerprinting | A tracking technique that collects specific details about your browser and device to create a unique ‘fingerprint’ to identify and track you. |
| GDPR | General Data Protection Regulation | A regulation in EU law on data protection and privacy for all individuals within the European Union and the European Economic Area. |
| IoT | Internet of Things | A network of physical devices (like smart speakers and cameras) embedded with sensors and software that connect to the internet. |
| IP Address | Internet Protocol Address | A unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. |
| VPN | Virtual Private Network | A service that encrypts your internet traffic and hides your IP address, providing a layer of security and privacy. |
10. Final thoughts: Making privacy a daily habit
We’ve covered a lot of ground, from mindset to specific tools and settings. The most important thing I want you to take away is that online privacy isn’t a one-time fix; it’s an ongoing practice and a habit. Don’t feel like you need to do everything on this list today. Start with one or two things, like enabling 2FA or installing a password manager and build from there.
Here are the most critical takeaways from this guide:
- Start with the Mindset: Your decisions are your best defense. Think before you share.
- Master the Foundations: Use 2FA, a password manager, and keep your software updated. These three actions solve a majority of common security threats.
- Control Your Browser: Use a privacy-focused browser and essential extensions to drastically reduce corporate tracking.
- Reclaim Your Data: You have the right to see and delete your data. Don’t be afraid to use it by opting out of data brokers and sending DSARs.
I hope this guide has empowered you to take meaningful steps toward a more private digital life. Protecting your data is a journey, and Afdevinfo is here to help you every step of the way. For more in-depth guides, explore our Online Security & Privacy categories.









